I keep getting bad image errors everytime I open a program and or file. I also have a hrad time opening MS Word. Everytime I try and open it a box pops up that says Windows Installer, however it doesn't do anything. Will will however open after a few times of opening and closing the program. I Googled on how to rid the problem and came across this site. I read through the instructions and did the appropiate scans and have the logs ready to be pasted. I saved my system specifications in my profile as well. I believe that just about covers it. Looking forward to your guys help! Thanks.
Malwarebytes
Malwarebytes Anti-Malware (Trial) 1.60.1.1000
www.malwarebytes.org
Database version: v2012.02.06.01
Windows XP Service Pack 3 x86 NTFS
Internet Explorer 8.0.6001.18702
Owner :: OWNER-EEE [administrator]
Protection: Disabled
2/6/2012 5:19:08 AM
mbam-log-2012-02-06 (05-19-08).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 180181
Time elapsed: 5 minute(s), 57 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
GMER
GMER 1.0.15.15641 - http://www.gmer.net
Rootkit quick scan 2012-02-06 05:39:34
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3 ST9160310AS rev.0303
Running: ccyf97rv.exe; Driver: C:\DOCUME~1\Owner\LOCALS~1\Temp\ugdcypow.sys
---- Devices - GMER 1.0.15 ----
AttachedDevice \FileSystem\Ntfs \Ntfs AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
AttachedDevice \FileSystem\Fastfat \Fat fltmgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
AttachedDevice \FileSystem\Fastfat \Fat AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
AttachedDevice \Driver\Tcpip \Device\Ip avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Tcp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Udp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\RawIp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
---- EOF - GMER 1.0.15 ----
DDS Notepad
.
DDS (Ver_2011-08-26.01) - NTFSx86
Internet Explorer: 8.0.6001.18702 BrowserJavaVersion: 1.6.0_17
Run by Owner at 5:44:05 on 2012-02-06
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2039.966 [GMT -6:00]
.
AV: AVG Anti-Virus Free Edition 2012 *Enabled/Updated* {17DDD097-36FF-435F-9E1B-52D74245D6BF}
AV: Lavasoft Ad-Watch Live! Anti-Virus *Disabled/Updated* {A1C4F2E0-7FDE-4917-AFAE-013EFC3EDE33}
.
============== Running Processes ===============
.
C:\PROGRA~1\AVG\AVG2012\avgrsx.exe
C:\Program Files\AVG\AVG2012\avgcsrvx.exe
C:\WINDOWS\system32\svchost.exe -k DcomLaunch
svchost.exe
C:\WINDOWS\System32\svchost.exe -k netsvcs
svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\Program Files\AVG\AVG2012\avgwdsvc.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe
C:\Program Files\EeePC\ACPI\AsAcpiSvr.exe
C:\Program Files\Elantech\ETDCtrl.exe
C:\Program Files\AVG\AVG2012\avgtray.exe
C:\Documents and Settings\All Users\Application Data\Ad-Aware Browsing Protection\adawarebp.exe
C:\Program Files\BillP Studios\WinPatrol\winpatrol.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\Program Files\ASUS\EeePC\Super Hybrid Engine\SuperHybridEngine.exe
C:\WINDOWS\System32\TUProgSt.exe
C:\Program Files\AVG\AVG2012\avgnsx.exe
C:\Program Files\AVG\AVG2012\avgemcx.exe
C:\WINDOWS\system32\igfxext.exe
C:\WINDOWS\system32\igfxsrvc.exe
C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe
C:\Program Files\Adobe\Acrobat 9.0\Acrobat\AcroTray.exe
C:\Program Files\Lavasoft\Ad-Aware\AAWService.exe
C:\Program Files\Lavasoft\Ad-Aware\AAWTray.exe
C:\Program Files\Malwarebytes' Anti-Malware\mbamgui.exe
C:\Program Files\internet explorer\iexplore.exe
C:\Program Files\internet explorer\iexplore.exe
C:\Program Files\AVG\AVG2012\AVGIDSAgent.exe
C:\Program Files\internet explorer\iexplore.exe
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://www.google.com/?rlz=1V1IPYX
uURLSearchHooks: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
BHO: ContributeBHO Class: {074c1dc5-9320-4a9a-947d-c042949c6216} - c:\program files\adobe\/Adobe Contribute CS4/contributeieplugin.dll
BHO: Adobe PDF Link Helper: {18df081c-e8ad-4283-a596-fa578c2ebdc3} - c:\program files\common files\adobe\acrobat\activex\AcroIEHelperShim.dll
BHO: AVG Safe Search: {3ca2f312-6f6e-4b53-a66e-4e65e497c8c0} - c:\program files\avg\avg2012\avgssie.dll
BHO: Spybot-S&D IE Protection: {53707962-6f74-2d53-2644-206d7942484f} - c:\progra~1\spybot~1\SDHelper.dll
BHO: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
BHO: Adobe PDF Conversion Toolbar Helper: {ae7cd045-e861-484f-8273-0445ee161910} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {dbc80044-a445-435b-bc74-9c25c1c588a9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl Class: {e7e6f031-17ce-4c07-bc86-eabfe594f69c} - c:\program files\java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
BHO: SmartSelect Class: {f4971ee7-daa0-4053-9964-665d8ee6a077} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
TB: Adobe PDF: {47833539-d0c5-4125-9fa8-0819e2eaac93} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
TB: Contribute Toolbar: {517bdde4-e3a7-4570-b21e-2b52b6139fc7} - c:\program files\adobe\/Adobe Contribute CS4/contributeieplugin.dll
TB: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
uRun: [ctfmon.exe] c:\windows\system32\ctfmon.exe
mRun: [AsusACPIServer] c:\program files\eeepc\acpi\AsAcpiSvr.exe
mRun: [ETDWare] c:\program files\elantech\ETDCtrl.exe
mRun: [AVG_TRAY] "c:\program files\avg\avg2012\avgtray.exe"
mRun: [Ad-Aware Browsing Protection] "c:\documents and settings\all users\application data\ad-aware browsing protection\adawarebp.exe"
mRun: [WinPatrol] c:\program files\billp studios\winpatrol\winpatrol.exe -expressboot
dRun: [DWQueuedReporting] "c:\progra~1\common~1\micros~1\dw\dwtrig20.exe" -t
dRunOnce: [adaware] reg.exe delete "HKCU\Software\AppDataLow\Software\adaware" /f
dRunOnce: [adaware_XP] reg.exe delete "HKCU\Software\adaware" /f
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\superh~1.lnk - c:\program files\asus\eeepc\super hybrid engine\SuperHybridEngine.exe
IE: Append Link Target to Existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Append to existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert link target to Adobe PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
IE: Convert link target to existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Convert to Adobe PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIECapture.html
IE: E&xport to Microsoft Excel - c:\progra~1\micros~2\office11\EXCEL.EXE/3000
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\progra~1\spybot~1\SDHelper.dll
DPF: {02BCC737-B171-4746-94C9-0D8A0B2C0089} - hxxp://office.microsoft.com/sites/production/ieawsdc32.cab
DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} - hxxp://update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1245530025921
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0017-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} - hxxp://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} - hxxp://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab
TCP: DhcpNameServer = 192.168.1.254
TCP: Interfaces\{3DA55623-8632-41CD-96BF-1DD0F84320C8} : DhcpNameServer = 192.168.1.254
Handler: linkscanner - {F274614C-63F8-47D5-A4D1-FBDDE494F8D1} - c:\program files\avg\avg2012\avgpp.dll
Notify: igfxcui - igfxdev.dll
AppInit_DLLs: acaptuser32.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\WPDShServiceObj.dll
SEH: Microsoft AntiMalware ShellExecuteHook: {091eb208-39dd-417d-a5dd-7e2c2d8fb9cb} - c:\progra~1\wifd1f~1\MpShHook.dll
Hosts: 127.0.0.1 www.spywareinfo.com
.
================= FIREFOX ===================
.
FF - ProfilePath - c:\documents and settings\owner\application data\mozilla\firefox\profiles\ooi0b1pb.default\
FF - prefs.js: browser.search.selectedEngine - Google
FF - prefs.js: browser.startup.homepage - hxxp://www.google.com/?rlz=1V1IPYX
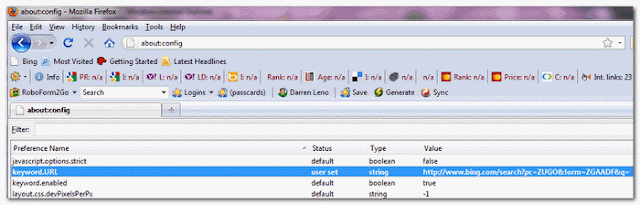
FF - prefs.js: keyword.URL - hxxp://search.search-star.net/?sid=10101040100&s=
FF - plugin: c:\program files\divx\divx plus web player\npdivx32.dll
FF - plugin: c:\program files\microsoft silverlight\4.0.60831.0\npctrlui.dll
FF - Ext: Default: {972ce4c6-7e08-4474-a285-3208198ce6fd} - c:\program files\mozilla firefox\extensions\{972ce4c6-7e08-4474-a285-3208198ce6fd}
FF - Ext: Java Quick Starter: jqs@sun.com - c:\program files\java\jre6\lib\deploy\jqs\ff
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\microsoft.net\framework\v3.5\windows presentation foundation\DotNetAssistantExtension
FF - Ext: AVG Safe Search: {1E73965B-8B48-48be-9C8D-68B920ABC1C4} - c:\program files\avg\avg2012\Firefox4
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - %profile%\extensions\{20a82645-c095-46ed-80e3-08825760534b}
FF - Ext: Ad-Aware Security Toolbar: {87934c42-161d-45bc-8cef-ef18abe2a30c} - %profile%\extensions\{87934c42-161d-45bc-8cef-ef18abe2a30c}
.
---- FIREFOX POLICIES ----
FF - user.js: browser.search.selectedEngine - Google
FF - user.js: browser.search.order.1 - Google
FF - user.js: keyword.URL - hxxp://search.search-star.net/?sid=10101040100&s=
.
============= SERVICES / DRIVERS ===============
.
R0 AVGIDSEH;AVGIDSEH;c:\windows\system32\drivers\AVGIDSEH.sys [2010-9-13 23120]
R0 Avgrkx86;AVG Anti-Rootkit Driver;c:\windows\system32\drivers\avgrkx86.sys [2010-9-7 32592]
R0 Lbd;Lbd;c:\windows\system32\drivers\Lbd.sys [2009-9-2 64512]
R1 Avgldx86;AVG AVI Loader Driver;c:\windows\system32\drivers\avgldx86.sys [2010-9-7 230608]
R1 Avgmfx86;AVG Mini-Filter Resident Anti-Virus Shield;c:\windows\system32\drivers\avgmfx86.sys [2010-9-7 40016]
R1 Avgtdix;AVG TDI Driver;c:\windows\system32\drivers\avgtdix.sys [2010-11-9 295248]
R2 AVGIDSAgent;AVGIDSAgent;c:\program files\avg\avg2012\AVGIDSAgent.exe [2011-10-12 4433248]
R2 avgwd;AVG WatchDog;c:\program files\avg\avg2012\avgwdsvc.exe [2011-8-2 192776]
R2 Lavasoft Ad-Aware Service;Lavasoft Ad-Aware Service;c:\program files\lavasoft\ad-aware\AAWService.exe [2011-12-23 2152152]
R2 MBAMService;MBAMService;c:\program files\malwarebytes' anti-malware\mbamservice.exe [2012-1-31 652360]
R3 AVGIDSDriver;AVGIDSDriver;c:\windows\system32\drivers\AVGIDSDriver.sys [2010-8-19 134608]
R3 AVGIDSFilter;AVGIDSFilter;c:\windows\system32\drivers\AVGIDSFilter.sys [2010-8-19 24272]
R3 AVGIDSShim;AVGIDSShim;c:\windows\system32\drivers\AVGIDSShim.sys [2010-8-19 16720]
R3 MBAMProtector;MBAMProtector;c:\windows\system32\drivers\mbam.sys [2012-1-31 20464]
S2 WinDefend;Windows Defender;c:\program files\windows defender\MsMpEng.exe [2006-11-3 13592]
S3 Adobe Version Cue CS4;Adobe Version Cue CS4;c:\program files\common files\adobe\adobe version cue cs4\server\bin\VersionCueCS4.exe [2008-8-15 284016]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;c:\program files\lavasoft\ad-aware\kernexplorer.sys [2011-12-23 15232]
.
=============== Created Last 30 ================
.
2012-02-02 22:43:52 -------- d-----w- c:\program files\Canon
2012-02-02 14:57:05 -------- d-----w- c:\documents and settings\owner\application data\AVG
2012-02-01 22:49:17 -------- d-----w- c:\documents and settings\owner\application data\WinPatrol
2012-02-01 22:48:57 -------- dc----w- c:\documents and settings\all users\application data\InstallMate
2012-02-01 22:48:57 -------- d-----w- c:\program files\BillP Studios
2012-02-01 21:31:15 388096 ----a-r- c:\documents and settings\owner\application data\microsoft\installer\{45a66726-69bc-466b-a7a4-12fcba4883d7}\HiJackThis.exe
2012-02-01 21:07:41 16432 ----a-w- c:\windows\system32\lsdelete.exe
2012-02-01 03:42:36 20464 ----a-w- c:\windows\system32\drivers\mbam.sys
2012-02-01 03:12:40 20 -c--a-w- c:\windows\system32\acaptuser32.dll
2012-02-01 03:10:45 103864 -c--a-w- c:\program files\mozilla firefox\plugins\nppdf32.dll
2012-01-31 23:22:05 -------- dc----w- C:\COMBOFIX
2012-01-28 21:52:03 2106216 ----a-w- c:\program files\mozilla firefox\D3DCompiler_43.dll
2012-01-28 21:52:03 121816 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
2012-01-28 21:52:02 1998168 ----a-w- c:\program files\mozilla firefox\d3dx9_43.dll
2012-01-28 21:52:00 97240 ----a-w- c:\program files\mozilla firefox\libEGL.dll
2012-01-28 21:52:00 486360 ----a-w- c:\program files\mozilla firefox\libGLESv2.dll
2012-01-28 21:52:00 2124760 ----a-w- c:\program files\mozilla firefox\mozjs.dll
2012-01-28 21:52:00 15832 ----a-w- c:\program files\mozilla firefox\mozalloc.dll
2012-01-28 21:51:59 814040 ----a-w- c:\program files\mozilla firefox\mozsqlite3.dll
2012-01-28 21:51:59 626688 ----a-w- c:\program files\mozilla firefox\msvcr80.dll
2012-01-28 21:51:59 548864 ----a-w- c:\program files\mozilla firefox\msvcp80.dll
2012-01-28 21:51:59 479232 ----a-w- c:\program files\mozilla firefox\msvcm80.dll
2012-01-28 21:51:59 43992 ----a-w- c:\program files\mozilla firefox\mozutils.dll
2012-01-24 23:11:54 -------- d-----w- c:\documents and settings\owner\application data\AVG2012
2012-01-24 23:10:00 -------- dc----w- c:\documents and settings\all users\application data\AVG2012
2012-01-19 13:43:50 -------- d-----w- c:\documents and settings\owner\local settings\application data\adaware
2012-01-19 13:43:45 -------- dc----w- c:\documents and settings\all users\application data\Ad-Aware Browsing Protection
2012-01-19 13:43:37 -------- d-----w- c:\program files\Toolbar Cleaner
2012-01-19 13:43:18 -------- d-----w- c:\documents and settings\owner\application data\adawaretb
2012-01-19 13:43:17 -------- d-----w- c:\program files\adawaretb
2012-01-19 13:42:51 -------- d-----w- c:\program files\Lavasoft
2012-01-19 11:45:27 -------- d-----w- c:\program files\trend micro
.
==================== Find3M ====================
.
2011-12-23 13:12:12 64512 ----a-w- c:\windows\system32\drivers\Lbd.sys
2011-11-25 21:57:19 293376 ----a-w- c:\windows\system32\winsrv.dll
2011-11-23 13:25:32 1859584 ----a-w- c:\windows\system32\win32k.sys
2011-11-18 12:35:08 60416 ----a-w- c:\windows\system32\packager.exe
2011-11-16 14:21:44 354816 ----a-w- c:\windows\system32\winhttp.dll
2011-11-16 14:21:44 152064 ----a-w- c:\windows\system32\schannel.dll
.
============= FINISH: 5:46:03.71 ===============
DDS Attach
.
UNLESS SPECIFICALLY INSTRUCTED, DO NOT POST THIS LOG.
IF REQUESTED, ZIP IT UP & ATTACH IT
.
DDS (Ver_2011-08-26.01)
.
Microsoft Windows XP Professional
Boot Device: \Device\HarddiskVolume1
Install Date: 6/20/2009 12:25:39 PM
System Uptime: 2/6/2012 12:42:20 AM (5 hours ago)
.
Motherboard: ASUSTeK Computer INC. | | 1002HA
Processor: Intel(R) Atom(TM) CPU N270 @ 1.60GHz | PBGA 437 | 1600/133mhz
.
==== Disk Partitions =========================
.
C: is FIXED (NTFS) - 90 GiB total, 20.055 GiB free.
D: is FIXED (NTFS) - 59 GiB total, 23.034 GiB free.
E: is Removable
.
==== Disabled Device Manager Items =============
.
==== System Restore Points ===================
.
RP610: 11/14/2011 8:18:47 PM - Software Distribution Service 3.0
RP611: 11/18/2011 7:49:05 AM - System Checkpoint
RP612: 11/23/2011 7:00:00 AM - System Checkpoint
RP613: 11/30/2011 7:21:53 AM - System Checkpoint
RP614: 12/1/2011 10:37:48 AM - System Checkpoint
RP615: 12/2/2011 11:48:12 AM - System Checkpoint
RP616: 12/8/2011 12:39:06 PM - System Checkpoint
RP617: 12/14/2011 9:42:23 AM - System Checkpoint
RP618: 12/15/2011 6:11:11 AM - Software Distribution Service 3.0
RP619: 12/16/2011 9:09:07 AM - System Checkpoint
RP620: 12/20/2011 8:41:23 AM - Software Distribution Service 3.0
RP621: 1/4/2012 1:14:27 PM - System Checkpoint
RP622: 1/5/2012 1:20:38 PM - System Checkpoint
RP623: 1/6/2012 1:41:32 PM - System Checkpoint
RP624: 1/19/2012 1:08:27 AM - System Checkpoint
RP625: 1/19/2012 3:00:41 AM - Software Distribution Service 3.0
RP626: 1/19/2012 7:40:52 AM - Installed Ad-Aware
RP627: 1/19/2012 7:42:48 AM - Installed Ad-Aware
RP628: 1/20/2012 1:22:24 PM - System Checkpoint
RP629: 1/24/2012 5:08:26 PM - Installed AVG 2012
RP630: 1/24/2012 5:08:44 PM - Removed AVG 2011
RP631: 1/24/2012 5:09:21 PM - Installed AVG 2012
RP632: 1/24/2012 5:16:09 PM - Removed AVG 2011
RP633: 1/28/2012 2:55:41 AM - Software Distribution Service 3.0
RP634: 1/30/2012 7:18:58 PM - System Checkpoint
RP635: 1/31/2012 4:36:50 PM - Software Distribution Service 3.0
RP636: 2/1/2012 3:21:22 PM - Software Distribution Service 3.0
RP637: 2/1/2012 3:31:13 PM - Installed HiJackThis
RP638: 2/2/2012 7:27:20 PM - System Checkpoint
RP639: 2/4/2012 9:16:29 AM - System Checkpoint
RP640: 2/5/2012 2:05:54 PM - System Checkpoint
.
==== Installed Programs ======================
.
Absolute Poker
Acrobat.com
Ad-Aware
Ad-Aware Security Toolbar
Adobe Acrobat 9 Pro Extended - English, Français, Deutsch
Adobe Acrobat 9.4.2 - CPSID_83708
Adobe After Effects CS4
Adobe After Effects CS4 Presets
Adobe After Effects CS4 Third Party Content
Adobe AIR
Adobe Anchor Service CS4
Adobe Asset Services CS4
Adobe Bridge CS4
Adobe CMaps CS4
Adobe Color - Photoshop Specific CS4
Adobe Color EU Extra Settings CS4
Adobe Color JA Extra Settings CS4
Adobe Color NA Recommended Settings CS4
Adobe Color Video Profiles AE CS4
Adobe Color Video Profiles CS CS4
Adobe Contribute CS4
Adobe Creative Suite 4 Master Collection
Adobe CS4 American English Speech Analysis Models
Adobe CSI CS4
Adobe Default Language CS4
Adobe Device Central CS4
Adobe Dreamweaver CS4
Adobe Drive CS4
Adobe Dynamiclink Support
Adobe Encore CS4
Adobe Encore CS4 Codecs
Adobe ExtendScript Toolkit CS4
Adobe Extension Manager CS4
Adobe Fireworks CS4
Adobe Flash CS4
Adobe Flash CS4 Extension - Flash Lite STI en
Adobe Flash CS4 STI-en
Adobe Flash Player 10 Plugin
Adobe Flash Player 11 ActiveX
Adobe Fonts All
Adobe Illustrator CS4
Adobe InDesign CS4
Adobe InDesign CS4 Application Feature Set Files (Roman)
Adobe InDesign CS4 Common Base Files
Adobe InDesign CS4 Icon Handler
Adobe Linguistics CS4
Adobe Media Encoder CS4
Adobe Media Encoder CS4 Additional Exporter
Adobe Media Encoder CS4 Dolby
Adobe Media Encoder CS4 Exporter
Adobe Media Encoder CS4 Importer
Adobe MotionPicture Color Files CS4
Adobe OnLocation CS4
Adobe Output Module
Adobe PDF Library Files CS4
Adobe Photoshop CS4
Adobe Photoshop CS4 Support
Adobe Premiere Pro CS4
Adobe Premiere Pro CS4 Functional Content
Adobe Premiere Pro CS4 Third Party Content
Adobe Search for Help
Adobe Service Manager Extension
Adobe Setup
Adobe SGM CS4
Adobe SING CS4
Adobe Soundbooth CS4
Adobe Soundbooth CS4 Codecs
Adobe Type Support CS4
Adobe Update Manager CS4
Adobe Version Cue CS4 Server
Adobe WinSoft Linguistics Plugin
Adobe XMP Panels CS4
AdobeColorCommonSetCMYK
AdobeColorCommonSetRGB
AoA DVD Ripper
Asus ACPI Driver
ASUSUpdate for Eee PC
AVG 2012
AVG PC Tuneup
Business Plan Pro 2007
Canon My Printer
Compatibility Pack for the 2007 Office system
Connect
DivX Setup
ETDWare PS/2-x86 7.0.4.3 WHQL
HiJackThis
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB953595)
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB958484)
hppscan3390
Intel(R) Graphics Media Accelerator Driver
Java(TM) 6 Update 17
kuler
Malwarebytes Anti-Malware version 1.60.1.1000
Microsoft .NET Framework 2.0 Service Pack 2
Microsoft .NET Framework 3.0 Service Pack 2
Microsoft .NET Framework 3.5 SP1
Microsoft Compression Client Pack 1.0 for Windows XP
Microsoft Internationalized Domain Names Mitigation APIs
Microsoft National Language Support Downlevel APIs
Microsoft Office 2003 Primary Interop Assemblies
Microsoft Office File Validation Add-In
Microsoft Office Professional Edition 2003
Microsoft Silverlight
Microsoft User-Mode Driver Framework Feature Pack 1.0
Microsoft Visual C++ 2005 ATL Update kb973923 - x86 8.0.50727.4053
Microsoft Visual C++ 2005 Redistributable
Microsoft Visual C++ 2008 Redistributable - KB2467174 - x86 9.0.30729.5570
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161
Microsoft Visual Studio 2005 Tools for Office Runtime
Mozilla Firefox 9.0.1 (x86 en-US)
MSXML 4.0 SP2 (KB954430)
MSXML 4.0 SP2 (KB973688)
MSXML 4.0 SP2 Parser and SDK
MSXML 6.0 Parser
PartitionMagic
PDF Settings CS4
Photoshop Camera Raw
Pixel Bender Toolkit
PlayFLV
PowerQuest PartitionMagic 8.0
QuickTime
Realtek High Definition Audio Driver
Scan
Security Update for Microsoft .NET Framework 3.5 SP1 (KB2657424)
Security Update for Windows Internet Explorer 7 (KB2183461)
Security Update for Windows Internet Explorer 7 (KB2360131)
Security Update for Windows Internet Explorer 7 (KB938127-v2)
Security Update for Windows Internet Explorer 7 (KB969897)
Security Update for Windows Internet Explorer 7 (KB972260)
Security Update for Windows Internet Explorer 8 (KB2360131)
Security Update for Windows Internet Explorer 8 (KB2416400)
Security Update for Windows Internet Explorer 8 (KB2482017)
Security Update for Windows Internet Explorer 8 (KB2497640)
Security Update for Windows Internet Explorer 8 (KB2510531)
Security Update for Windows Internet Explorer 8 (KB2530548)
Security Update for Windows Internet Explorer 8 (KB2544521)
Security Update for Windows Internet Explorer 8 (KB2559049)
Security Update for Windows Internet Explorer 8 (KB2586448)
Security Update for Windows Internet Explorer 8 (KB2618444)
Security Update for Windows Internet Explorer 8 (KB971961)
Security Update for Windows Internet Explorer 8 (KB981332)
Security Update for Windows Internet Explorer 8 (KB982381)
Security Update for Windows XP (KB923789)
Spybot - Search & Destroy
Suite Shared Configuration CS4
Super Hybrid Engine
TuneUp Utilities 2009
Update for Microsoft .NET Framework 3.5 SP1 (KB963707)
Update for Windows Internet Explorer 8 (KB2447568)
Update for Windows Internet Explorer 8 (KB976662)
VC80CRTRedist - 8.0.50727.4053
VideoLAN VLC media player 0.8.6d
Visual C++ 2008 x86 Runtime - (v9.0.30729)
Visual C++ 2008 x86 Runtime - v9.0.30729.01
Vuze
WebFldrs XP
Windows Defender
Windows Internet Explorer 7
Windows Internet Explorer 8
Windows Media Format 11 runtime
Windows Media Player 11
Windows XP Service Pack 3
WinPatrol
WinRAR archiver
Xvid 1.2.2 final uninstall
.
==== Event Viewer Messages From Past Week ========
.
2/3/2012 6:04:33 PM, error: Dhcp [1002] - The IP address lease 10.28.54.99 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 0.0.0.0 (The DHCP Server sent a DHCPNACK message).
2/3/2012 11:46:36 PM, error: Dhcp [1002] - The IP address lease 192.168.1.117 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 192.168.1.254 (The DHCP Server sent a DHCPNACK message).
2/3/2012 1:37:27 PM, error: Dhcp [1002] - The IP address lease 192.168.1.117 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 1.1.1.1 (The DHCP Server sent a DHCPNACK message).
2/2/2012 4:18:39 PM, error: Dhcp [1002] - The IP address lease 10.28.56.48 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 0.0.0.0 (The DHCP Server sent a DHCPNACK message).
1/31/2012 9:27:43 PM, error: sr [1] - The System Restore filter encountered the unexpected error '0xC0000001' while processing the file '' on the volume 'HarddiskVolume1'. It has stopped monitoring the volume.
1/31/2012 1:35:11 PM, error: Dhcp [1002] - The IP address lease 192.168.1.73 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 1.1.1.1 (The DHCP Server sent a DHCPNACK message).
1/30/2012 7:01:21 PM, error: Service Control Manager [7011] - Timeout (30000 milliseconds) waiting for a transaction response from the avgwd service.
1/30/2012 6:59:55 PM, error: Service Control Manager [7011] - Timeout (30000 milliseconds) waiting for a transaction response from the TuneUp.ProgramStatisticsSvc service.
1/30/2012 6:58:38 PM, error: Dhcp [1002] - The IP address lease 10.28.30.155 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 192.168.1.254 (The DHCP Server sent a DHCPNACK message).
.
==== End Of File ===========================
Malwarebytes
Malwarebytes Anti-Malware (Trial) 1.60.1.1000
www.malwarebytes.org
Database version: v2012.02.06.01
Windows XP Service Pack 3 x86 NTFS
Internet Explorer 8.0.6001.18702
Owner :: OWNER-EEE [administrator]
Protection: Disabled
2/6/2012 5:19:08 AM
mbam-log-2012-02-06 (05-19-08).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 180181
Time elapsed: 5 minute(s), 57 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
GMER
GMER 1.0.15.15641 - http://www.gmer.net
Rootkit quick scan 2012-02-06 05:39:34
Windows 5.1.2600 Service Pack 3 Harddisk0\DR0 -> \Device\Ide\IdeDeviceP0T0L0-3 ST9160310AS rev.0303
Running: ccyf97rv.exe; Driver: C:\DOCUME~1\Owner\LOCALS~1\Temp\ugdcypow.sys
---- Devices - GMER 1.0.15 ----
AttachedDevice \FileSystem\Ntfs \Ntfs AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
AttachedDevice \FileSystem\Fastfat \Fat fltmgr.sys (Microsoft Filesystem Filter Manager/Microsoft Corporation)
AttachedDevice \FileSystem\Fastfat \Fat AVGIDSFilter.Sys (IDS Application Activity Monitor Filter Driver./AVG Technologies CZ, s.r.o. )
AttachedDevice \Driver\Tcpip \Device\Ip avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Tcp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\Udp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
AttachedDevice \Driver\Tcpip \Device\RawIp avgtdix.sys (AVG Network connection watcher/AVG Technologies CZ, s.r.o.)
---- EOF - GMER 1.0.15 ----
DDS Notepad
.
DDS (Ver_2011-08-26.01) - NTFSx86
Internet Explorer: 8.0.6001.18702 BrowserJavaVersion: 1.6.0_17
Run by Owner at 5:44:05 on 2012-02-06
Microsoft Windows XP Professional 5.1.2600.3.1252.1.1033.18.2039.966 [GMT -6:00]
.
AV: AVG Anti-Virus Free Edition 2012 *Enabled/Updated* {17DDD097-36FF-435F-9E1B-52D74245D6BF}
AV: Lavasoft Ad-Watch Live! Anti-Virus *Disabled/Updated* {A1C4F2E0-7FDE-4917-AFAE-013EFC3EDE33}
.
============== Running Processes ===============
.
C:\PROGRA~1\AVG\AVG2012\avgrsx.exe
C:\Program Files\AVG\AVG2012\avgcsrvx.exe
C:\WINDOWS\system32\svchost.exe -k DcomLaunch
svchost.exe
C:\WINDOWS\System32\svchost.exe -k netsvcs
svchost.exe
C:\WINDOWS\system32\spoolsv.exe
C:\WINDOWS\Explorer.EXE
C:\Program Files\AVG\AVG2012\avgwdsvc.exe
C:\Program Files\Java\jre6\bin\jqs.exe
C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe
C:\Program Files\EeePC\ACPI\AsAcpiSvr.exe
C:\Program Files\Elantech\ETDCtrl.exe
C:\Program Files\AVG\AVG2012\avgtray.exe
C:\Documents and Settings\All Users\Application Data\Ad-Aware Browsing Protection\adawarebp.exe
C:\Program Files\BillP Studios\WinPatrol\winpatrol.exe
C:\WINDOWS\system32\ctfmon.exe
C:\WINDOWS\system32\svchost.exe -k imgsvc
C:\Program Files\ASUS\EeePC\Super Hybrid Engine\SuperHybridEngine.exe
C:\WINDOWS\System32\TUProgSt.exe
C:\Program Files\AVG\AVG2012\avgnsx.exe
C:\Program Files\AVG\AVG2012\avgemcx.exe
C:\WINDOWS\system32\igfxext.exe
C:\WINDOWS\system32\igfxsrvc.exe
C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe
C:\Program Files\Common Files\Macrovision Shared\FLEXnet Publisher\FNPLicensingService.exe
C:\Program Files\Adobe\Acrobat 9.0\Acrobat\AcroTray.exe
C:\Program Files\Lavasoft\Ad-Aware\AAWService.exe
C:\Program Files\Lavasoft\Ad-Aware\AAWTray.exe
C:\Program Files\Malwarebytes' Anti-Malware\mbamgui.exe
C:\Program Files\internet explorer\iexplore.exe
C:\Program Files\internet explorer\iexplore.exe
C:\Program Files\AVG\AVG2012\AVGIDSAgent.exe
C:\Program Files\internet explorer\iexplore.exe
.
============== Pseudo HJT Report ===============
.
uStart Page = hxxp://www.google.com/?rlz=1V1IPYX
uURLSearchHooks: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
BHO: ContributeBHO Class: {074c1dc5-9320-4a9a-947d-c042949c6216} - c:\program files\adobe\/Adobe Contribute CS4/contributeieplugin.dll
BHO: Adobe PDF Link Helper: {18df081c-e8ad-4283-a596-fa578c2ebdc3} - c:\program files\common files\adobe\acrobat\activex\AcroIEHelperShim.dll
BHO: AVG Safe Search: {3ca2f312-6f6e-4b53-a66e-4e65e497c8c0} - c:\program files\avg\avg2012\avgssie.dll
BHO: Spybot-S&D IE Protection: {53707962-6f74-2d53-2644-206d7942484f} - c:\progra~1\spybot~1\SDHelper.dll
BHO: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
BHO: Adobe PDF Conversion Toolbar Helper: {ae7cd045-e861-484f-8273-0445ee161910} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
BHO: Java(tm) Plug-In 2 SSV Helper: {dbc80044-a445-435b-bc74-9c25c1c588a9} - c:\program files\java\jre6\bin\jp2ssv.dll
BHO: JQSIEStartDetectorImpl Class: {e7e6f031-17ce-4c07-bc86-eabfe594f69c} - c:\program files\java\jre6\lib\deploy\jqs\ie\jqs_plugin.dll
BHO: SmartSelect Class: {f4971ee7-daa0-4053-9964-665d8ee6a077} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
TB: Adobe PDF: {47833539-d0c5-4125-9fa8-0819e2eaac93} - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll
TB: Contribute Toolbar: {517bdde4-e3a7-4570-b21e-2b52b6139fc7} - c:\program files\adobe\/Adobe Contribute CS4/contributeieplugin.dll
TB: Ad-Aware Security Toolbar: {6c97a91e-4524-4019-86af-2aa2d567bf5c} - c:\program files\adawaretb\adawareDx.dll
uRun: [ctfmon.exe] c:\windows\system32\ctfmon.exe
mRun: [AsusACPIServer] c:\program files\eeepc\acpi\AsAcpiSvr.exe
mRun: [ETDWare] c:\program files\elantech\ETDCtrl.exe
mRun: [AVG_TRAY] "c:\program files\avg\avg2012\avgtray.exe"
mRun: [Ad-Aware Browsing Protection] "c:\documents and settings\all users\application data\ad-aware browsing protection\adawarebp.exe"
mRun: [WinPatrol] c:\program files\billp studios\winpatrol\winpatrol.exe -expressboot
dRun: [DWQueuedReporting] "c:\progra~1\common~1\micros~1\dw\dwtrig20.exe" -t
dRunOnce: [adaware] reg.exe delete "HKCU\Software\AppDataLow\Software\adaware" /f
dRunOnce: [adaware_XP] reg.exe delete "HKCU\Software\adaware" /f
StartupFolder: c:\docume~1\alluse~1\startm~1\programs\startup\superh~1.lnk - c:\program files\asus\eeepc\super hybrid engine\SuperHybridEngine.exe
IE: Append Link Target to Existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Append to existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert link target to Adobe PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
IE: Convert link target to existing PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Convert to Adobe PDF - c:\program files\common files\adobe\acrobat\activex\AcroIEFavClient.dll/AcroIECapture.html
IE: E&xport to Microsoft Excel - c:\progra~1\micros~2\office11\EXCEL.EXE/3000
IE: {e2e2dd38-d088-4134-82b7-f2ba38496583} - %windir%\Network Diagnostic\xpnetdiag.exe
IE: {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - {53707962-6F74-2D53-2644-206D7942484F} - c:\progra~1\spybot~1\SDHelper.dll
DPF: {02BCC737-B171-4746-94C9-0D8A0B2C0089} - hxxp://office.microsoft.com/sites/production/ieawsdc32.cab
DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} - hxxp://update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1245530025921
DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {CAFEEFAC-0016-0000-0017-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} - hxxp://java.sun.com/update/1.6.0/jinstall-1_6_0_17-windows-i586.cab
DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} - hxxp://fpdownload2.macromedia.com/get/shockwave/cabs/flash/swflash.cab
DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} - hxxp://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab
TCP: DhcpNameServer = 192.168.1.254
TCP: Interfaces\{3DA55623-8632-41CD-96BF-1DD0F84320C8} : DhcpNameServer = 192.168.1.254
Handler: linkscanner - {F274614C-63F8-47D5-A4D1-FBDDE494F8D1} - c:\program files\avg\avg2012\avgpp.dll
Notify: igfxcui - igfxdev.dll
AppInit_DLLs: acaptuser32.dll
SSODL: WPDShServiceObj - {AAA288BA-9A4C-45B0-95D7-94D524869DB5} - c:\windows\system32\WPDShServiceObj.dll
SEH: Microsoft AntiMalware ShellExecuteHook: {091eb208-39dd-417d-a5dd-7e2c2d8fb9cb} - c:\progra~1\wifd1f~1\MpShHook.dll
Hosts: 127.0.0.1 www.spywareinfo.com
.
================= FIREFOX ===================
.
FF - ProfilePath - c:\documents and settings\owner\application data\mozilla\firefox\profiles\ooi0b1pb.default\
FF - prefs.js: browser.search.selectedEngine - Google
FF - prefs.js: browser.startup.homepage - hxxp://www.google.com/?rlz=1V1IPYX
FF - prefs.js: keyword.URL - hxxp://search.search-star.net/?sid=10101040100&s=
FF - plugin: c:\program files\divx\divx plus web player\npdivx32.dll
FF - plugin: c:\program files\microsoft silverlight\4.0.60831.0\npctrlui.dll
FF - Ext: Default: {972ce4c6-7e08-4474-a285-3208198ce6fd} - c:\program files\mozilla firefox\extensions\{972ce4c6-7e08-4474-a285-3208198ce6fd}
FF - Ext: Java Quick Starter: jqs@sun.com - c:\program files\java\jre6\lib\deploy\jqs\ff
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\microsoft.net\framework\v3.5\windows presentation foundation\DotNetAssistantExtension
FF - Ext: AVG Safe Search: {1E73965B-8B48-48be-9C8D-68B920ABC1C4} - c:\program files\avg\avg2012\Firefox4
FF - Ext: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - %profile%\extensions\{20a82645-c095-46ed-80e3-08825760534b}
FF - Ext: Ad-Aware Security Toolbar: {87934c42-161d-45bc-8cef-ef18abe2a30c} - %profile%\extensions\{87934c42-161d-45bc-8cef-ef18abe2a30c}
.
---- FIREFOX POLICIES ----
FF - user.js: browser.search.selectedEngine - Google
FF - user.js: browser.search.order.1 - Google
FF - user.js: keyword.URL - hxxp://search.search-star.net/?sid=10101040100&s=
.
============= SERVICES / DRIVERS ===============
.
R0 AVGIDSEH;AVGIDSEH;c:\windows\system32\drivers\AVGIDSEH.sys [2010-9-13 23120]
R0 Avgrkx86;AVG Anti-Rootkit Driver;c:\windows\system32\drivers\avgrkx86.sys [2010-9-7 32592]
R0 Lbd;Lbd;c:\windows\system32\drivers\Lbd.sys [2009-9-2 64512]
R1 Avgldx86;AVG AVI Loader Driver;c:\windows\system32\drivers\avgldx86.sys [2010-9-7 230608]
R1 Avgmfx86;AVG Mini-Filter Resident Anti-Virus Shield;c:\windows\system32\drivers\avgmfx86.sys [2010-9-7 40016]
R1 Avgtdix;AVG TDI Driver;c:\windows\system32\drivers\avgtdix.sys [2010-11-9 295248]
R2 AVGIDSAgent;AVGIDSAgent;c:\program files\avg\avg2012\AVGIDSAgent.exe [2011-10-12 4433248]
R2 avgwd;AVG WatchDog;c:\program files\avg\avg2012\avgwdsvc.exe [2011-8-2 192776]
R2 Lavasoft Ad-Aware Service;Lavasoft Ad-Aware Service;c:\program files\lavasoft\ad-aware\AAWService.exe [2011-12-23 2152152]
R2 MBAMService;MBAMService;c:\program files\malwarebytes' anti-malware\mbamservice.exe [2012-1-31 652360]
R3 AVGIDSDriver;AVGIDSDriver;c:\windows\system32\drivers\AVGIDSDriver.sys [2010-8-19 134608]
R3 AVGIDSFilter;AVGIDSFilter;c:\windows\system32\drivers\AVGIDSFilter.sys [2010-8-19 24272]
R3 AVGIDSShim;AVGIDSShim;c:\windows\system32\drivers\AVGIDSShim.sys [2010-8-19 16720]
R3 MBAMProtector;MBAMProtector;c:\windows\system32\drivers\mbam.sys [2012-1-31 20464]
S2 WinDefend;Windows Defender;c:\program files\windows defender\MsMpEng.exe [2006-11-3 13592]
S3 Adobe Version Cue CS4;Adobe Version Cue CS4;c:\program files\common files\adobe\adobe version cue cs4\server\bin\VersionCueCS4.exe [2008-8-15 284016]
S3 Lavasoft Kernexplorer;Lavasoft helper driver;c:\program files\lavasoft\ad-aware\kernexplorer.sys [2011-12-23 15232]
.
=============== Created Last 30 ================
.
2012-02-02 22:43:52 -------- d-----w- c:\program files\Canon
2012-02-02 14:57:05 -------- d-----w- c:\documents and settings\owner\application data\AVG
2012-02-01 22:49:17 -------- d-----w- c:\documents and settings\owner\application data\WinPatrol
2012-02-01 22:48:57 -------- dc----w- c:\documents and settings\all users\application data\InstallMate
2012-02-01 22:48:57 -------- d-----w- c:\program files\BillP Studios
2012-02-01 21:31:15 388096 ----a-r- c:\documents and settings\owner\application data\microsoft\installer\{45a66726-69bc-466b-a7a4-12fcba4883d7}\HiJackThis.exe
2012-02-01 21:07:41 16432 ----a-w- c:\windows\system32\lsdelete.exe
2012-02-01 03:42:36 20464 ----a-w- c:\windows\system32\drivers\mbam.sys
2012-02-01 03:12:40 20 -c--a-w- c:\windows\system32\acaptuser32.dll
2012-02-01 03:10:45 103864 -c--a-w- c:\program files\mozilla firefox\plugins\nppdf32.dll
2012-01-31 23:22:05 -------- dc----w- C:\COMBOFIX
2012-01-28 21:52:03 2106216 ----a-w- c:\program files\mozilla firefox\D3DCompiler_43.dll
2012-01-28 21:52:03 121816 ----a-w- c:\program files\mozilla firefox\components\browsercomps.dll
2012-01-28 21:52:02 1998168 ----a-w- c:\program files\mozilla firefox\d3dx9_43.dll
2012-01-28 21:52:00 97240 ----a-w- c:\program files\mozilla firefox\libEGL.dll
2012-01-28 21:52:00 486360 ----a-w- c:\program files\mozilla firefox\libGLESv2.dll
2012-01-28 21:52:00 2124760 ----a-w- c:\program files\mozilla firefox\mozjs.dll
2012-01-28 21:52:00 15832 ----a-w- c:\program files\mozilla firefox\mozalloc.dll
2012-01-28 21:51:59 814040 ----a-w- c:\program files\mozilla firefox\mozsqlite3.dll
2012-01-28 21:51:59 626688 ----a-w- c:\program files\mozilla firefox\msvcr80.dll
2012-01-28 21:51:59 548864 ----a-w- c:\program files\mozilla firefox\msvcp80.dll
2012-01-28 21:51:59 479232 ----a-w- c:\program files\mozilla firefox\msvcm80.dll
2012-01-28 21:51:59 43992 ----a-w- c:\program files\mozilla firefox\mozutils.dll
2012-01-24 23:11:54 -------- d-----w- c:\documents and settings\owner\application data\AVG2012
2012-01-24 23:10:00 -------- dc----w- c:\documents and settings\all users\application data\AVG2012
2012-01-19 13:43:50 -------- d-----w- c:\documents and settings\owner\local settings\application data\adaware
2012-01-19 13:43:45 -------- dc----w- c:\documents and settings\all users\application data\Ad-Aware Browsing Protection
2012-01-19 13:43:37 -------- d-----w- c:\program files\Toolbar Cleaner
2012-01-19 13:43:18 -------- d-----w- c:\documents and settings\owner\application data\adawaretb
2012-01-19 13:43:17 -------- d-----w- c:\program files\adawaretb
2012-01-19 13:42:51 -------- d-----w- c:\program files\Lavasoft
2012-01-19 11:45:27 -------- d-----w- c:\program files\trend micro
.
==================== Find3M ====================
.
2011-12-23 13:12:12 64512 ----a-w- c:\windows\system32\drivers\Lbd.sys
2011-11-25 21:57:19 293376 ----a-w- c:\windows\system32\winsrv.dll
2011-11-23 13:25:32 1859584 ----a-w- c:\windows\system32\win32k.sys
2011-11-18 12:35:08 60416 ----a-w- c:\windows\system32\packager.exe
2011-11-16 14:21:44 354816 ----a-w- c:\windows\system32\winhttp.dll
2011-11-16 14:21:44 152064 ----a-w- c:\windows\system32\schannel.dll
.
============= FINISH: 5:46:03.71 ===============
DDS Attach
.
UNLESS SPECIFICALLY INSTRUCTED, DO NOT POST THIS LOG.
IF REQUESTED, ZIP IT UP & ATTACH IT
.
DDS (Ver_2011-08-26.01)
.
Microsoft Windows XP Professional
Boot Device: \Device\HarddiskVolume1
Install Date: 6/20/2009 12:25:39 PM
System Uptime: 2/6/2012 12:42:20 AM (5 hours ago)
.
Motherboard: ASUSTeK Computer INC. | | 1002HA
Processor: Intel(R) Atom(TM) CPU N270 @ 1.60GHz | PBGA 437 | 1600/133mhz
.
==== Disk Partitions =========================
.
C: is FIXED (NTFS) - 90 GiB total, 20.055 GiB free.
D: is FIXED (NTFS) - 59 GiB total, 23.034 GiB free.
E: is Removable
.
==== Disabled Device Manager Items =============
.
==== System Restore Points ===================
.
RP610: 11/14/2011 8:18:47 PM - Software Distribution Service 3.0
RP611: 11/18/2011 7:49:05 AM - System Checkpoint
RP612: 11/23/2011 7:00:00 AM - System Checkpoint
RP613: 11/30/2011 7:21:53 AM - System Checkpoint
RP614: 12/1/2011 10:37:48 AM - System Checkpoint
RP615: 12/2/2011 11:48:12 AM - System Checkpoint
RP616: 12/8/2011 12:39:06 PM - System Checkpoint
RP617: 12/14/2011 9:42:23 AM - System Checkpoint
RP618: 12/15/2011 6:11:11 AM - Software Distribution Service 3.0
RP619: 12/16/2011 9:09:07 AM - System Checkpoint
RP620: 12/20/2011 8:41:23 AM - Software Distribution Service 3.0
RP621: 1/4/2012 1:14:27 PM - System Checkpoint
RP622: 1/5/2012 1:20:38 PM - System Checkpoint
RP623: 1/6/2012 1:41:32 PM - System Checkpoint
RP624: 1/19/2012 1:08:27 AM - System Checkpoint
RP625: 1/19/2012 3:00:41 AM - Software Distribution Service 3.0
RP626: 1/19/2012 7:40:52 AM - Installed Ad-Aware
RP627: 1/19/2012 7:42:48 AM - Installed Ad-Aware
RP628: 1/20/2012 1:22:24 PM - System Checkpoint
RP629: 1/24/2012 5:08:26 PM - Installed AVG 2012
RP630: 1/24/2012 5:08:44 PM - Removed AVG 2011
RP631: 1/24/2012 5:09:21 PM - Installed AVG 2012
RP632: 1/24/2012 5:16:09 PM - Removed AVG 2011
RP633: 1/28/2012 2:55:41 AM - Software Distribution Service 3.0
RP634: 1/30/2012 7:18:58 PM - System Checkpoint
RP635: 1/31/2012 4:36:50 PM - Software Distribution Service 3.0
RP636: 2/1/2012 3:21:22 PM - Software Distribution Service 3.0
RP637: 2/1/2012 3:31:13 PM - Installed HiJackThis
RP638: 2/2/2012 7:27:20 PM - System Checkpoint
RP639: 2/4/2012 9:16:29 AM - System Checkpoint
RP640: 2/5/2012 2:05:54 PM - System Checkpoint
.
==== Installed Programs ======================
.
Absolute Poker
Acrobat.com
Ad-Aware
Ad-Aware Security Toolbar
Adobe Acrobat 9 Pro Extended - English, Français, Deutsch
Adobe Acrobat 9.4.2 - CPSID_83708
Adobe After Effects CS4
Adobe After Effects CS4 Presets
Adobe After Effects CS4 Third Party Content
Adobe AIR
Adobe Anchor Service CS4
Adobe Asset Services CS4
Adobe Bridge CS4
Adobe CMaps CS4
Adobe Color - Photoshop Specific CS4
Adobe Color EU Extra Settings CS4
Adobe Color JA Extra Settings CS4
Adobe Color NA Recommended Settings CS4
Adobe Color Video Profiles AE CS4
Adobe Color Video Profiles CS CS4
Adobe Contribute CS4
Adobe Creative Suite 4 Master Collection
Adobe CS4 American English Speech Analysis Models
Adobe CSI CS4
Adobe Default Language CS4
Adobe Device Central CS4
Adobe Dreamweaver CS4
Adobe Drive CS4
Adobe Dynamiclink Support
Adobe Encore CS4
Adobe Encore CS4 Codecs
Adobe ExtendScript Toolkit CS4
Adobe Extension Manager CS4
Adobe Fireworks CS4
Adobe Flash CS4
Adobe Flash CS4 Extension - Flash Lite STI en
Adobe Flash CS4 STI-en
Adobe Flash Player 10 Plugin
Adobe Flash Player 11 ActiveX
Adobe Fonts All
Adobe Illustrator CS4
Adobe InDesign CS4
Adobe InDesign CS4 Application Feature Set Files (Roman)
Adobe InDesign CS4 Common Base Files
Adobe InDesign CS4 Icon Handler
Adobe Linguistics CS4
Adobe Media Encoder CS4
Adobe Media Encoder CS4 Additional Exporter
Adobe Media Encoder CS4 Dolby
Adobe Media Encoder CS4 Exporter
Adobe Media Encoder CS4 Importer
Adobe MotionPicture Color Files CS4
Adobe OnLocation CS4
Adobe Output Module
Adobe PDF Library Files CS4
Adobe Photoshop CS4
Adobe Photoshop CS4 Support
Adobe Premiere Pro CS4
Adobe Premiere Pro CS4 Functional Content
Adobe Premiere Pro CS4 Third Party Content
Adobe Search for Help
Adobe Service Manager Extension
Adobe Setup
Adobe SGM CS4
Adobe SING CS4
Adobe Soundbooth CS4
Adobe Soundbooth CS4 Codecs
Adobe Type Support CS4
Adobe Update Manager CS4
Adobe Version Cue CS4 Server
Adobe WinSoft Linguistics Plugin
Adobe XMP Panels CS4
AdobeColorCommonSetCMYK
AdobeColorCommonSetRGB
AoA DVD Ripper
Asus ACPI Driver
ASUSUpdate for Eee PC
AVG 2012
AVG PC Tuneup
Business Plan Pro 2007
Canon My Printer
Compatibility Pack for the 2007 Office system
Connect
DivX Setup
ETDWare PS/2-x86 7.0.4.3 WHQL
HiJackThis
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB953595)
Hotfix for Microsoft .NET Framework 3.5 SP1 (KB958484)
hppscan3390
Intel(R) Graphics Media Accelerator Driver
Java(TM) 6 Update 17
kuler
Malwarebytes Anti-Malware version 1.60.1.1000
Microsoft .NET Framework 2.0 Service Pack 2
Microsoft .NET Framework 3.0 Service Pack 2
Microsoft .NET Framework 3.5 SP1
Microsoft Compression Client Pack 1.0 for Windows XP
Microsoft Internationalized Domain Names Mitigation APIs
Microsoft National Language Support Downlevel APIs
Microsoft Office 2003 Primary Interop Assemblies
Microsoft Office File Validation Add-In
Microsoft Office Professional Edition 2003
Microsoft Silverlight
Microsoft User-Mode Driver Framework Feature Pack 1.0
Microsoft Visual C++ 2005 ATL Update kb973923 - x86 8.0.50727.4053
Microsoft Visual C++ 2005 Redistributable
Microsoft Visual C++ 2008 Redistributable - KB2467174 - x86 9.0.30729.5570
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.4148
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161
Microsoft Visual Studio 2005 Tools for Office Runtime
Mozilla Firefox 9.0.1 (x86 en-US)
MSXML 4.0 SP2 (KB954430)
MSXML 4.0 SP2 (KB973688)
MSXML 4.0 SP2 Parser and SDK
MSXML 6.0 Parser
PartitionMagic
PDF Settings CS4
Photoshop Camera Raw
Pixel Bender Toolkit
PlayFLV
PowerQuest PartitionMagic 8.0
QuickTime
Realtek High Definition Audio Driver
Scan
Security Update for Microsoft .NET Framework 3.5 SP1 (KB2657424)
Security Update for Windows Internet Explorer 7 (KB2183461)
Security Update for Windows Internet Explorer 7 (KB2360131)
Security Update for Windows Internet Explorer 7 (KB938127-v2)
Security Update for Windows Internet Explorer 7 (KB969897)
Security Update for Windows Internet Explorer 7 (KB972260)
Security Update for Windows Internet Explorer 8 (KB2360131)
Security Update for Windows Internet Explorer 8 (KB2416400)
Security Update for Windows Internet Explorer 8 (KB2482017)
Security Update for Windows Internet Explorer 8 (KB2497640)
Security Update for Windows Internet Explorer 8 (KB2510531)
Security Update for Windows Internet Explorer 8 (KB2530548)
Security Update for Windows Internet Explorer 8 (KB2544521)
Security Update for Windows Internet Explorer 8 (KB2559049)
Security Update for Windows Internet Explorer 8 (KB2586448)
Security Update for Windows Internet Explorer 8 (KB2618444)
Security Update for Windows Internet Explorer 8 (KB971961)
Security Update for Windows Internet Explorer 8 (KB981332)
Security Update for Windows Internet Explorer 8 (KB982381)
Security Update for Windows XP (KB923789)
Spybot - Search & Destroy
Suite Shared Configuration CS4
Super Hybrid Engine
TuneUp Utilities 2009
Update for Microsoft .NET Framework 3.5 SP1 (KB963707)
Update for Windows Internet Explorer 8 (KB2447568)
Update for Windows Internet Explorer 8 (KB976662)
VC80CRTRedist - 8.0.50727.4053
VideoLAN VLC media player 0.8.6d
Visual C++ 2008 x86 Runtime - (v9.0.30729)
Visual C++ 2008 x86 Runtime - v9.0.30729.01
Vuze
WebFldrs XP
Windows Defender
Windows Internet Explorer 7
Windows Internet Explorer 8
Windows Media Format 11 runtime
Windows Media Player 11
Windows XP Service Pack 3
WinPatrol
WinRAR archiver
Xvid 1.2.2 final uninstall
.
==== Event Viewer Messages From Past Week ========
.
2/3/2012 6:04:33 PM, error: Dhcp [1002] - The IP address lease 10.28.54.99 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 0.0.0.0 (The DHCP Server sent a DHCPNACK message).
2/3/2012 11:46:36 PM, error: Dhcp [1002] - The IP address lease 192.168.1.117 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 192.168.1.254 (The DHCP Server sent a DHCPNACK message).
2/3/2012 1:37:27 PM, error: Dhcp [1002] - The IP address lease 192.168.1.117 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 1.1.1.1 (The DHCP Server sent a DHCPNACK message).
2/2/2012 4:18:39 PM, error: Dhcp [1002] - The IP address lease 10.28.56.48 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 0.0.0.0 (The DHCP Server sent a DHCPNACK message).
1/31/2012 9:27:43 PM, error: sr [1] - The System Restore filter encountered the unexpected error '0xC0000001' while processing the file '' on the volume 'HarddiskVolume1'. It has stopped monitoring the volume.
1/31/2012 1:35:11 PM, error: Dhcp [1002] - The IP address lease 192.168.1.73 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 1.1.1.1 (The DHCP Server sent a DHCPNACK message).
1/30/2012 7:01:21 PM, error: Service Control Manager [7011] - Timeout (30000 milliseconds) waiting for a transaction response from the avgwd service.
1/30/2012 6:59:55 PM, error: Service Control Manager [7011] - Timeout (30000 milliseconds) waiting for a transaction response from the TuneUp.ProgramStatisticsSvc service.
1/30/2012 6:58:38 PM, error: Dhcp [1002] - The IP address lease 10.28.30.155 for the Network Card with network address 00224360D6F1 has been denied by the DHCP server 192.168.1.254 (The DHCP Server sent a DHCPNACK message).
.
==== End Of File ===========================