Earlier we had reported on a major hardware flaw that could be exploited to compromise systems based on Intel processors released over the last decade. As many of the details of these flaws were being held under embargo, we didn't learn all the details until later.
There are two major flaws that affect all modern computers based on processors from Intel, AMD and ARM. The flaws have received the names Meltdown and Spectre, and both potentially allow hackers to steal personal data from computers, including mobile devices and cloud servers, without leaving a trace. Both holes could be exploited to get access to data stored in the memory of other running programs. A practical example would be your passwords stored in a password manager or browser, your personal emails, or business-critical documents.
If that isn’t bad enough, patching the issue might slow down the performance of a CPU by up to 35 percent (a realistic worst-case scenario). At the moment we're running preliminary tests on Windows 10 covering storage, gaming and applications to see what the immediate effects are to the average user.
Update, we've run some benchmarks: With an emergency fix for Windows 10 already out, we've conducted a set of tests to measure the impact this update has on performance for desktop users, if any at all.
Update #2: Following up to our initial testing, we're looking deeper into the matter by testing a patched desktop system for both Meltdown (OS-level patch) and Spectre (firmware/BIOS update).
The flaws were discovered last year by Google’s Project Zero team, when they demonstrated that malicious code could take advantage of “speculative execution,” a technique used by most modern CPUs to optimize performance. Since then the company put forth efforts to disclose and collaborate with manufacturers across the industry, secure Google’s systems, as well as work on mitigating action.
The coordinated disclosure date for the flaws was January 9, 2018, but because of premature reports and growing speculation and risk of exploitation, the information was revealed sooner and patches are just being made available for some platforms.
Distinct attacks, same risk -- Who is affected?
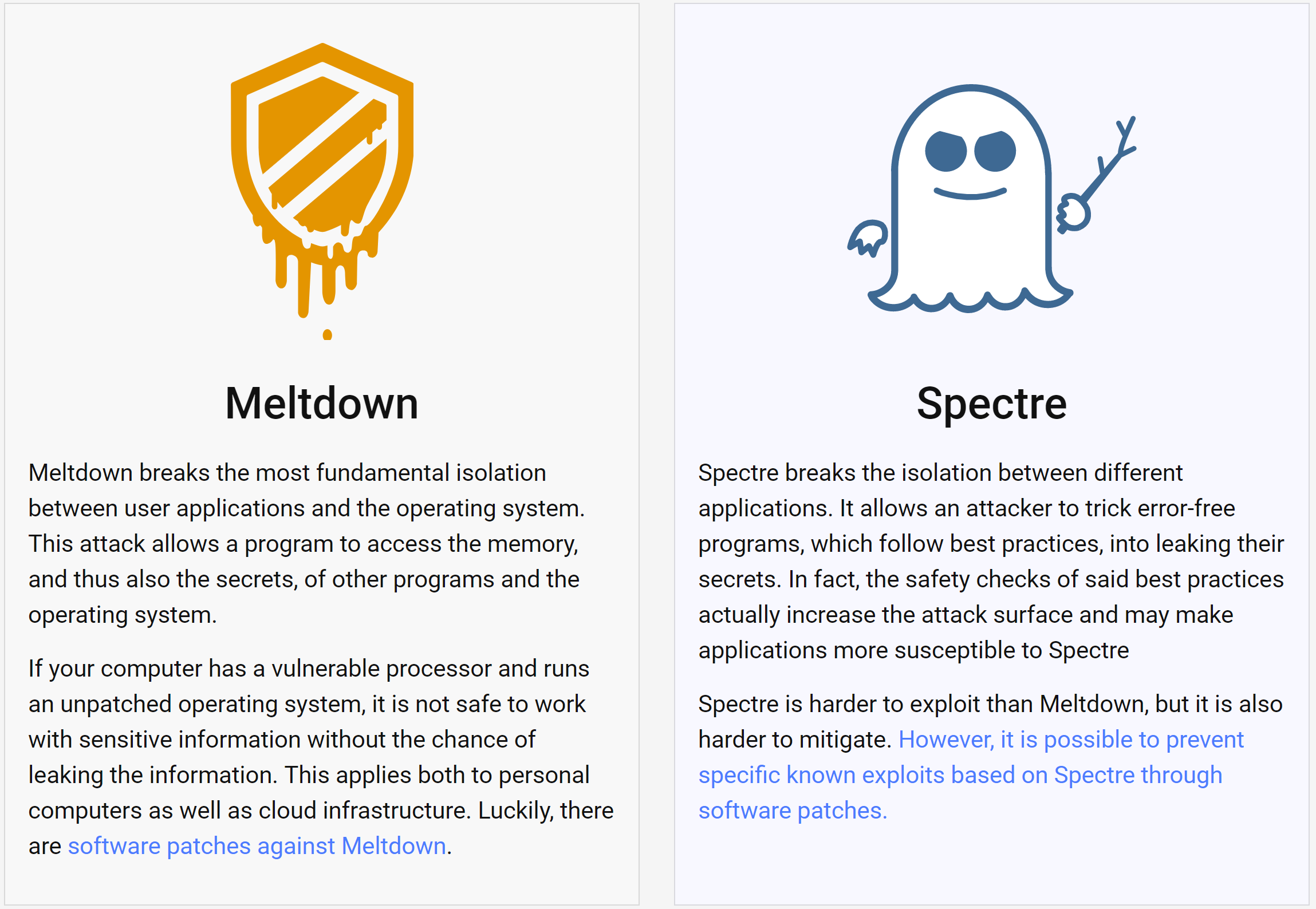
Meltdown and Spectre are distinct attacks but both pose the same kind of risk. An informational website with whitepapers on both flaws has been made public today.
So far Meltdown has only been proofed on Intel processors.
More technically, every Intel processor which implements out-of-order execution is potentially affected, which is effectively every processor since 1995 (except Intel Itanium and Intel Atom before 2013). We successfully tested Meltdown on Intel processor generations released as early as 2011. Currently, we have only verified Meltdown on Intel processors. At the moment, it is unclear whether ARM and AMD processors are also affected by Meltdown.
Spectre is harder to exploit but also harder to secure against. Researchers have verified it to work across Intel, AMD, and ARM processors. In their words "as it is not easy to fix, it will haunt us for quite some time."
Almost every system is affected by Spectre: Desktops, Laptops, Cloud Servers, as well as Smartphones. More specifically, all modern processors capable of keeping many instructions in flight are potentially vulnerable.
Get Patched
Because these flaws cannot be fixed with a firmware or microcode update alone, an OS-level fix is also required for the affected operating systems. The immediate solution comes in the form of a kernel Page Table Isolation (PTI), which separates the kernel’s memory from user processes. But this solution increases the kernel’s overhead, potentially causing the system to slow down depending on the task and processor model.
Early indications suggest that these patches mostly deal with Meltdown exploits and not Spectre, which again, is harder to exploit and to fix. In order to protect against all instances of Spectre, application-level fixes are to be expected.
Windows
Microsoft has released an emergency patch this evening for Windows 10 that is being applied automatically. Windows 7 and Windows 8 have also received a patch that you can apply manually now, while automatic updates are rolling out ahead of next Patch Tuesday.
In addition to the patch, Microsoft is warning that some third-party antivirus will create a conflict with the fix and the OS update won't be applied to those systems until the antivirus supports these changes.
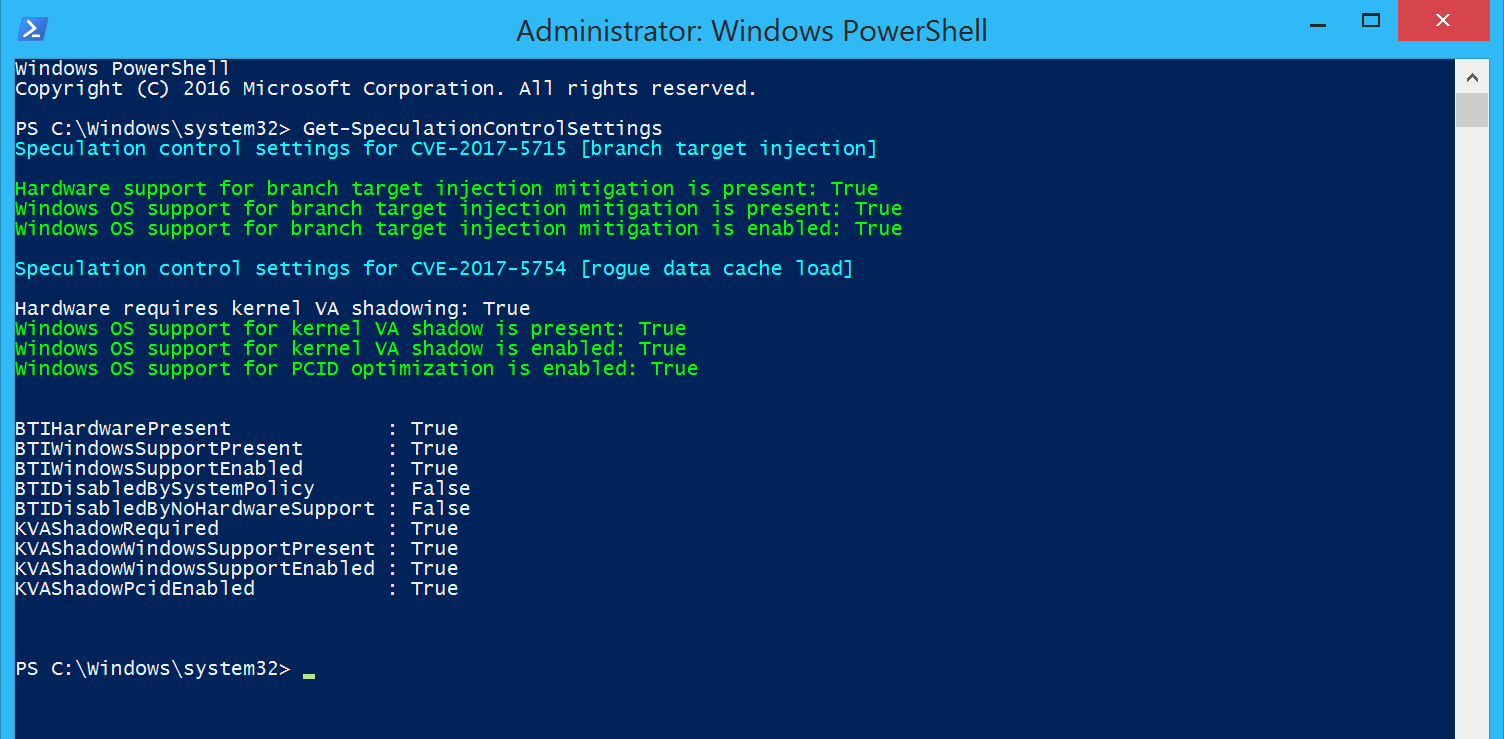
Users should expect additional hardware/firmware updates from OEMs and motherboard manufacturers in the short term to complement Microsoft's patch. There is a PowerShell verification script which can be used to test and confirm whether protections have been enabled properly.
macOS
Apple has confirmed that all of its iPhones, iPads, and Mac devices are affected by the recently discovered chip flaws. The company has already released OS updates to protect users from the Meltdown attack, and a patch for Spectre will arrive "in the coming days.”
Apple released mitigations in iOS 11.2, macOS 10.13.2, and tvOS 11.2 to help defend against Meltdown, adding that these updates do not slow down the devices. As the Apple Watch doesn’t use Intel chips, it is not affected.
Linux
Linux kernel developers have a set of patches named kernel page-table isolation (KPTI) released in kernel 4.15 (currently in RC). More information here and here. Redhat users should see this.
Android
Google says that devices with the latest security update are protected.
Cloud Services
Companies that use virtualized environments are the biggest potential targets for those looking to exploit the vulnerability. Microsoft Azure, Amazon AWS, and Google Cloud Platform are all implementing fixes and say have already mitigated some of the risk. Expect scheduled downtime of several cloud services in the coming days.
What Intel, AMD and ARM are saying...
As the biggest PC chip maker and the most exposed to Meltdown, Intel is receiving most of the heat after the disclosure of the flaws. Here is part of their official statement:
Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.
Intel is committed to product and customer security and is working closely with many other technology companies, including AMD, ARM Holdings and several operating system vendors, to develop an industry-wide approach to resolve this issue promptly and constructively. Intel has begun providing software and firmware updates to mitigate these exploits. Contrary to some reports, any performance impacts are workload-dependent, and, for the average computer user, should not be significant and will be mitigated over time.
Intel's stock took a small hit this week, but making matters even more uncomfortable, Intel CEO Brian Krzanich sold off $24 million worth of stock and options in the company in late November. Intel was already aware of the chip vulnerability then.
AMD has been somewhat rejoicing, although they seem to be least or not affected by Meltdown. Spectre does affect AMD processors:
AMD processors are not subject to the types of attacks that the kernel page table isolation feature protects against. The AMD microarchitecture does not allow memory references, including speculative references, that access higher privileged data when running in a lesser privileged mode when that access would result in a page fault.
---
Due to differences in AMD's architecture, we believe there is a near zero risk to AMD processors at this time. We expect the security research to be published later today and will provide further updates at that time.
Finally, this is what ARM said:
"ARM (has) been working together with Intel and AMD to address a side-channel analysis method which exploits speculative execution techniques used in certain high-end processors, including some of our Cortex-A processors. This method requires malware running locally and could result in data being accessed from privileged memory. Please note that our Cortex-M processors, which are pervasive in low-power, connected IoT devices, are not impacted."
Editor's Note: We've added more details and have kept fine-tuning this report as more information becomes available.
Further follow-up coverage can be found here. With an emergency fix for Windows 10 already out, we've conducted a set of tests to measure the impact this update has on performance for desktop users.
https://www.techspot.com/news/72576-massive-cpu-flaws-get-name-meltdown-spectre-what.html