What just happened? Microsoft’s vision of a password-free future starts now. From today, users can elect to remove the password from their Microsoft account and sign in using one of several passwordless methods including Windows Hello, the Microsoft Authenticator mobile app, a security key or via a verification code sent to your e-mail or phone.

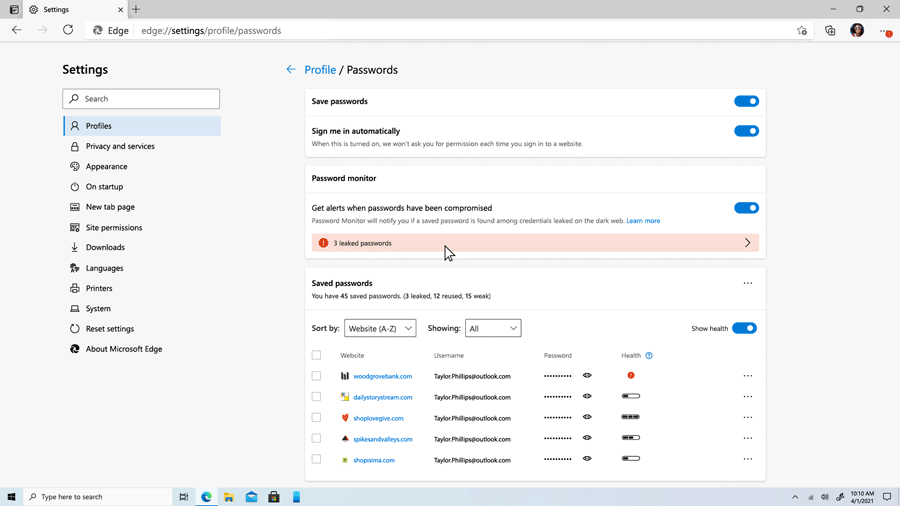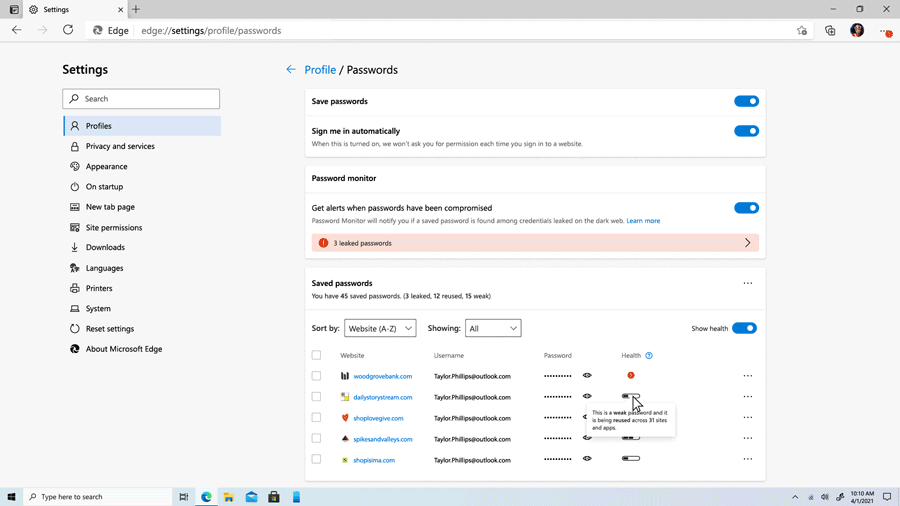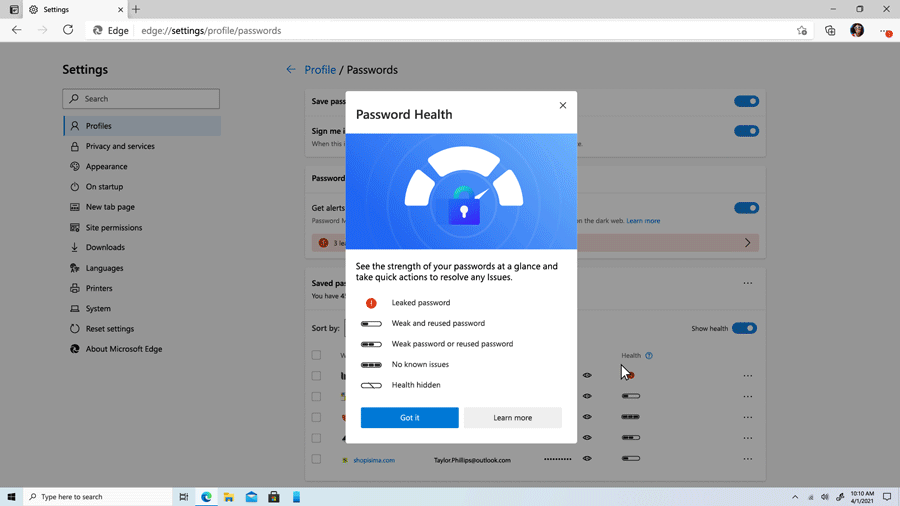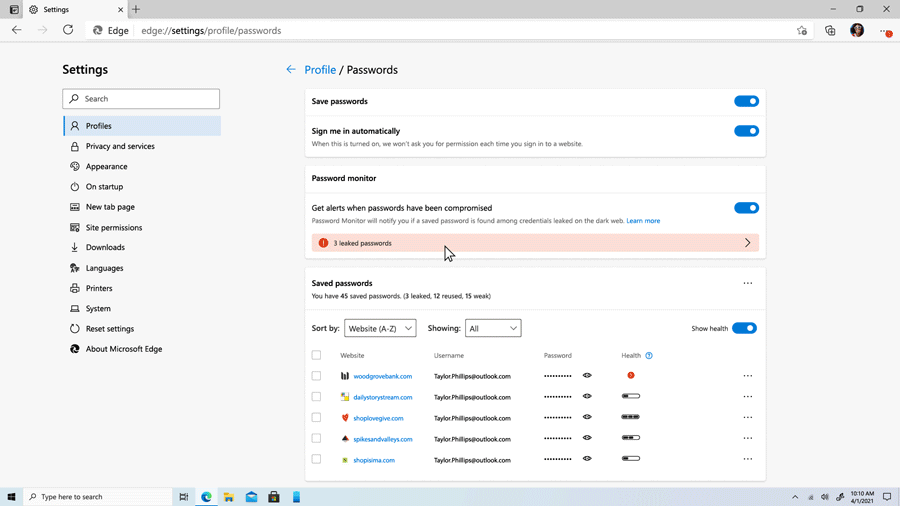
Liat Ben-Zur, a corporate vice president at Microsoft, said they’re aware of the fact that the world isn’t ready to ditch passwords just yet. As such, Microsoft has tools in place to meet users where they are in their passwordless journey. For example, Microsoft Edge has a built-in password manager, a password generator and a password health dashboard to help users create and maintain strong passwords.
Those interested in taking a stroll down Microsoft’s passwordless path are encouraged to check out this blog post for more information on how to get started. It’s simple really, just sign in to your Microsoft account, then select Advanced Security Options -> Additional Security Options -> Passwordless Account and turn it on. Then just follow the on-screen prompts to finish setup and you should be good to go.
If you find that passworldess isn't for you, you can always revert back to using a password with your account.
Vasu Jakkal, CVP of security, compliance and identity and Microsoft, said nearly 100 percent of their employees now use passwordless options to log into their corporate accounts.
Microsoft is also hosting a digital event called Your Passwordless Future Starts Now on October 13, 2021, to help educate attendees on how Microsoft is allowing users in organizations to ditch their passwords.
Masthead credit Paulius Dragunas
https://www.techspot.com/news/91265-microsoft-adds-passwordless-option-account-access.html