
Microsoft has released an update to fix a vulnerability discovered in its MsMpEng malware protection engine used in Windows Defender, Windows Intune Endpoint Protection, Microsoft Security Essentials, and more. The bug can allow a hacker to take over a system just by sending an email or instant message - the recipient doesn’t even have to open or read it for the attack to work, Defender just needs to scan the contents. The flaw could also be exploited by getting users to click on web browser links.
Google Project Zero researchers Tavis Ormandy and Natalie Silvanovich discovered the “crazy bad” bug over the weekend. It lets hackers booby trap files with malicious code that is automatically executed when Microsoft’s anti-malware software scans the data.
I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way. ???
— Tavis Ormandy (@taviso) May 6, 2017
"An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights,” wrote Microsoft. The company added that it hadn't seen any public exploitation of the vulnerability.
Google’s security report explains that the Malware Protection service is “enabled by default” in Windows 8, 8.1, 10, Server 2012 and a number of other versions of the software. You can see the full list below.
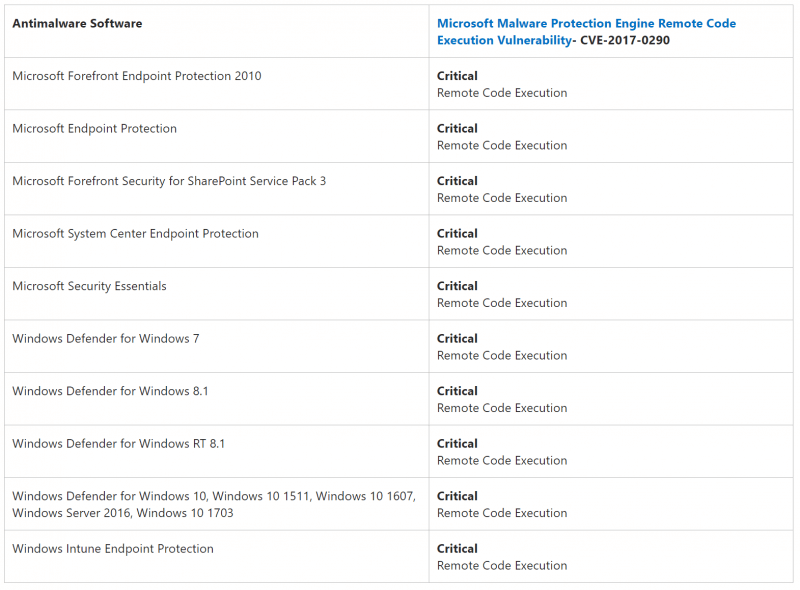
The fix was rolled out in an emergency update on Monday night, just hours before the weekly Tuesday security update. The Redmond company has been praised for the speed at which it released the patch. Ormandy says he was “blown away” by how quickly Microsoft responded.
To make sure your PC has been patched and isn’t at risk, head to ‘Windows Defender settings’ and make sure the engine number is 1.1.13704.0 or higher.