Ransomware is on the rise with nearly 50% of businesses across the United States, Canada, United Kingdom, and Germany reportedly experiencing an attack last year alone, according to a study sponsored by Malwarebytes. The survey included 540 CIOs, CISOs and IT directors from companies with an average of 5,400 employees in these countries.
This type of attack encrypts or locks files away before demanding payment in return for a key to decrypt them and return the PC to normal. The most heavily targeted industries for ransomware are healthcare and financial services.
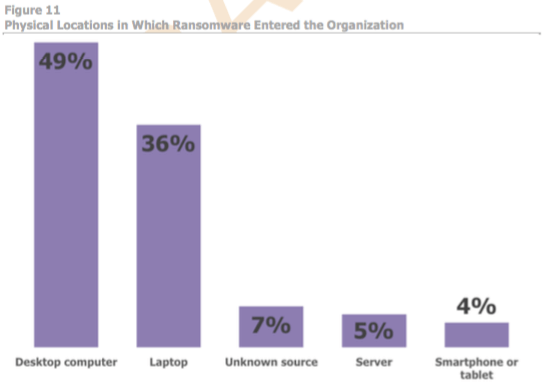
Among organizations that have experienced a ransomware attack, roughly one-half have encountered the attack through a desktop computer, followed by laptops as the second most common ingress point. Mobile devices and servers are not common entry points.
As you would expect, email links and attachments are the primary method used by criminals to target organizations, making up nearly 60 percent of all infections.
An average user hit with ransomware may be asked to pay up $500 to $1,000, according to Malwarebytes, but when an enterprise gets hit the sum is $10,000 and up. The study found that ransom demands in excess of $10,000 are most common in Germany (48%), but much less common in the United Kingdom (22%), the United States (18%) and Canada (14%).
Many are apparently giving in to demands for payment as the cost of keeping operations closed is far higher -- as much as 40% pay up. Curiously, organizations in the United States were found to be far less likely to pay the ransom. Only 3% admitted to paying up versus 75% of ransomware victims in Canada, 22% in Germany and 58% in the UK.
Among organizations that chose not to pay the ransom after becoming infected with ransomware, more than one-quarter lost files as a result. You can check out the complete report here for other interesting tidbits on this growing pain for IT departments everywhere.
https://www.techspot.com/news/65837-ransomware-attacks-rise-us-firms-less-likely-pay.html
