In brief: Antivirus software typically relies on a combination of machine learning algorithms and frequently-updated malware definitions to protect our computers from outside threats. However, no antivirus software is perfect, and they will occasionally miss newer or heavily-disguised threats. That's why researchers from the Institute of Computer Science and Random Systems have sought to explore new methods of detecting hostile programs that don't rely on software solutions at all.

Instead, the team -- comprised of four members -- is taking advantage of electromagnetic pulses to detect harmful software; even when the target is obfuscated. Their approach is unorthodox, to say the least, but also fairly accurate based on their initial tests.
The technology the team developed uses a Raspberry Pi to connect with an infected or potentially-infected device. The Pi interfaces with an H-field probe and an oscilloscope: the former is what detects the magnetic waves emitting from a device and the latter visualizes them for a malware analyst to view.
According to the researchers, different varieties of malware give off specific electromagnetic waves. Since everything seems to give off such waves these days, it wasn't enough to just set up the system and analyze the oscilloscope's output. The Pi-based malware detector had to be trained on a variety of threats to improve its detection accuracy and root out false positives.
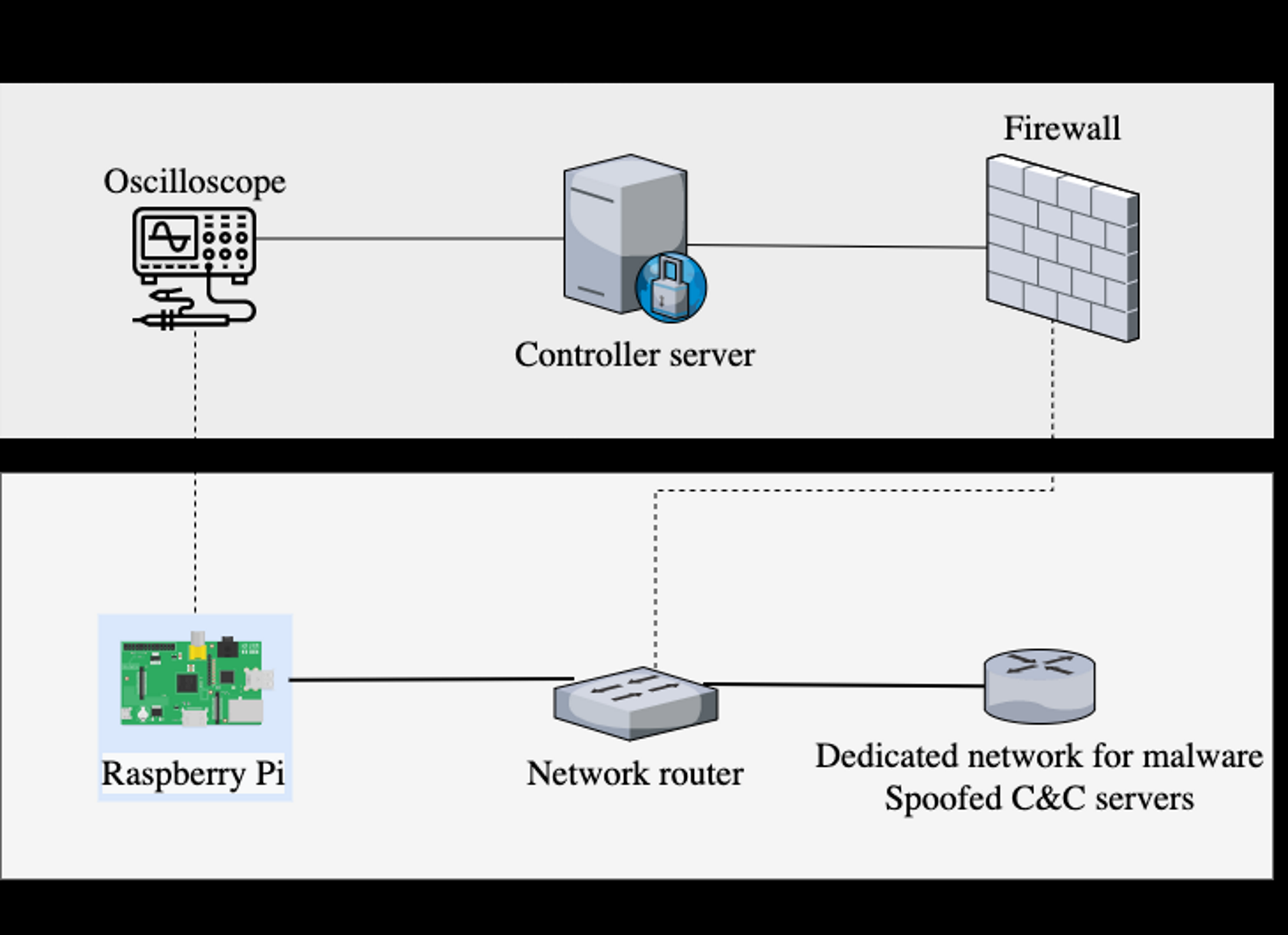
During the researchers' experiments, the Pi was able to predict three "generic malware types" and one "benign" class (non-harmful malware that might be more of an annoyance than anything) with an accuracy of about 99.82 percent. It doesn't matter, the team notes, what sort of obfuscation techniques the software in question might be using on the software side because their device doesn't rely on software; it operates at a higher level.
This research is still in its early stages, and this tech isn't going to be widely available to the public anytime soon. However, the potential for good is obvious: malware creators will undoubtedly find it difficult, if not impossible, to completely hide the electromagnetic traces their programs leave behind.
We can see a future in which this tech is used to feed antivirus databases and allow programs like Malwarebytes and Windows Defender to stay ahead of the curve and better protect their users. That would be ideal, anyway -- malware creators are nothing if not crafty, so perhaps they'll find some way around this detection system in the future.
https://www.techspot.com/news/92935-raspberry-pi-based-device-uses-electromagnetic-waves-detect.html