Why it matters: We expect that when we have a CT or MRI scan that the results are accurate. After all we are talking about equipment that can cost millions of dollars and radiologists with years of training and sometimes decades of experience. However, hospital security can be lax and researchers have now shown they can fake CT and MRI scans using a generative adversarial network (GAN).

Israeli researchers created malware that can alter CT and MRI scans well enough to fool radiologists into misdiagnosis. The deep-learning software can create realistic looking fake malignant tumors or can hide real growths from scans in close to real time.
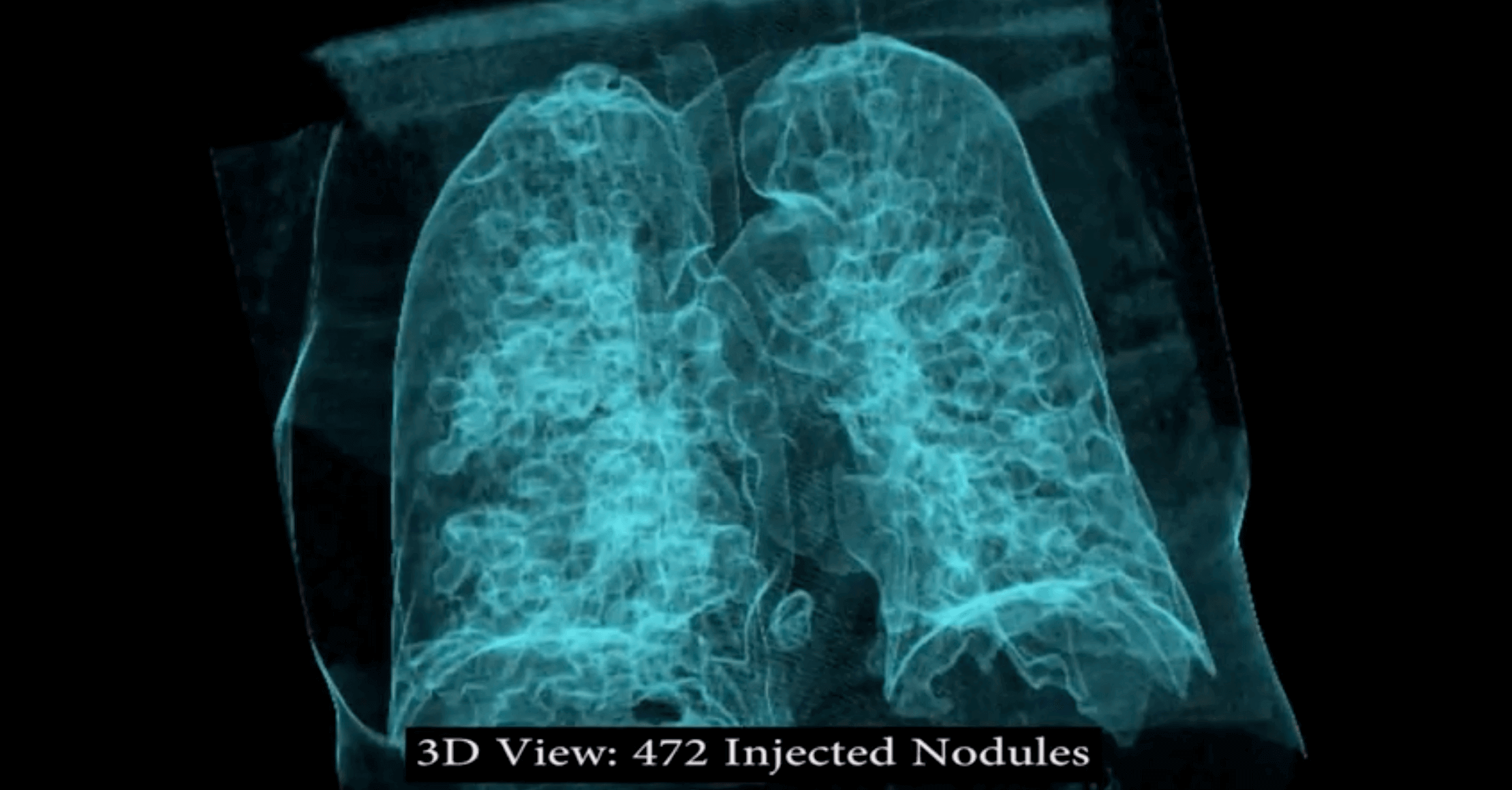
"We implement the attack using a 3D conditional GAN and show how the framework (CT-GAN) can be automated," said Yisroel Mirsky, Tom Mahler, Ilan Shelef, and Yuval Elovici in their study. "Although the body is complex and 3D medical scans are very large, CT-GAN achieves realistic results which can be executed in milliseconds. "
In a blind study, using 70 altered lung scans and three experienced radiologists, the software tricked them almost every time. In instances where they were looking at faked growths, they delivered a cancer diagnosis 99 percent of the time. In scans where the malware had removed actual tumors, the radiologist gave the all clear 94 percent of the time.

The radiologists were told that they had been tricked and were given a second chance with 20 more scans with half being altered. They were wrong 60 percent of the time with injected nodules and 87 percent of the time with removed growths.
The researchers then ran tests against software designed to detect lung cancer in images, which radiologist use to confirm their own diagnosis. It misdiagnosed faked nodules 100 percent of the time.
“I was quite shocked,” Nancy Boniel, a radiologist in Canada who participated in the study told the Washington Post. “I felt like the carpet was pulled out from under me, and I was left without the tools necessary to move forward.”
Yisroel Mirsky and his team at the Ben-Gurion University Cyber Security Research Center in Israel created the malware to highlight the lack of security protecting diagnostic equipment and other hospital systems. The software was designed specifically for this study, so it is not something that is a present danger to the health care industry. However, they do see it as a clear illustration of risks hospitals, doctors, and radiologists are not prepared for.
The researchers are concerned that such attacks could be carried out to interfere with political opponents or worse.
“An attacker may perform this act in order to stop a political candidate, sabotage research, commit insurance fraud, perform an act of terrorism, or even commit murder,” Mirsky et al. wrote in their study published by Cornell University.
They say malicious parties could pull off an attack using a man-in-the-middle device planted near the scanner. They demonstrate such an attack in their video (below) using a Raspberry Pi 3 that they picked up for about $40. Since the data transmitted from the CT or MRI scanner is not encrypted, the attackers can easily falsify scans, which are then sent back to the receiving server.
Fixing the problem would seem as simple as just encrypting data across the network. However, the FDA’s Associate Director for Science and Strategic Partnerships Suzanne Schwartz MD says it is not that simple.
“It’s going to require changes that go well beyond devices, but changes with regards to the network infrastructure,” said Schwartz. “Many hospitals don’t have the money to invest in more secure equipment, or they have 20-year-old infrastructure that doesn’t support newer technologies. This is where engaging and involving with other authorities and trying to bring the entire community together becomes really important.”
As far as the consequences to a victim of such an attack, it would take more than fake scans to put them under the knife or in chemotherapy. However, there are plenty of side effects that could create trouble for patients.
“There are a couple of steps before we just take someone to surgery [or administer chemo],” said UC San Diego emergency room physician Christian Dameff. “But there is still harm to the patient regardless. There is the emotional distress [from learning you may have cancer], and there are all sorts of insurance implications.”
The security of diagnostic equipment is clearly something that the industry must address, but the solutions are not a simple fix.
https://www.techspot.com/news/79529-researchers-fake-cancerous-nodes-ct-scans-machine-learning.html