A hot potato: If one needed more indication that the security of Microsoft Exchange servers still looks like Swiss cheese, a threat actor known as Gelsemium has provided one. Security researchers at Kaspersky believe the group has been using stealthy malware dubbed SessionManager to attack the server infrastructure of public organizations worldwide for more than a year.

On Thursday, Kaspersky researchers published a worrying report concerning a new, hard-to-detect backdoor that targets Exchange servers used by government and medical institutions, military organizations, and NGOs in multiple countries. The malware, dubbed SessionManager, was first spotted in early 2022.
At the time, some of the malware samples observed by analysts were not getting flagged by many popular online file scanning services. Furthermore, the SessionManager infection persists in over 90 percent of the targeted organizations.
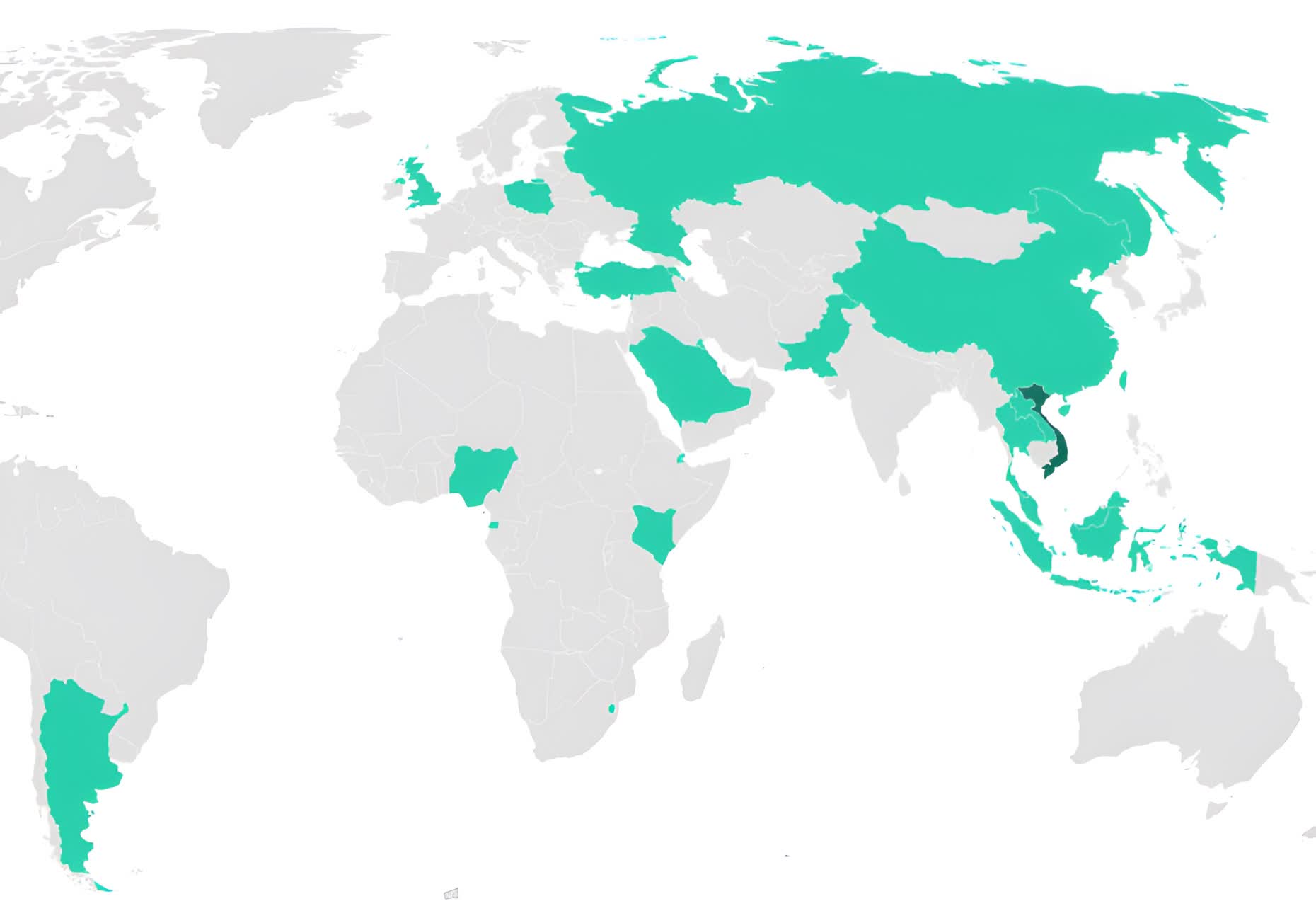
Map of organizations targeted by SessionManager campaign
The threat actors behind SessionManager have been using it for the past 15 months. Kaspersky suspects a hacking group called Gelsemium is responsible for the attacks because the hacking patterns fit the group's MO. However, analysts cannot confirm Gelsemium is the culprit.
The malware uses potent malicious native-code modules written for Microsoft's Internet Information Services (IIS) web server software. Once installed, they will respond to special HTTP requests to collect sensitive information. Attackers can also take complete control over the servers, deploy additional hacking tools, and use them for other malicious purposes.
Interestingly, the process of installing SessionManager depends on exploiting a set of vulnerabilities collectively called ProxyLogon (CVE-2021-26855). Last year, Microsoft said that well over 90 percent of Exchange servers had been patched or mitigated, but that still left many already-compromised servers at risk.
The disinfection process is quite complicated, but Kaspersky researchers have provided a few pointers on protecting your organization against threats like SessionManager. You can also consult Securelist for more relevant information on how SessionManager operates and indicators of compromise.