Facepalm: Do you think your home router is secure? According to a new report, that belief might be far from accurate. It found that many popular devices are affected by hundreds of known vulnerabilities, and over a third have not received an update in the last year.

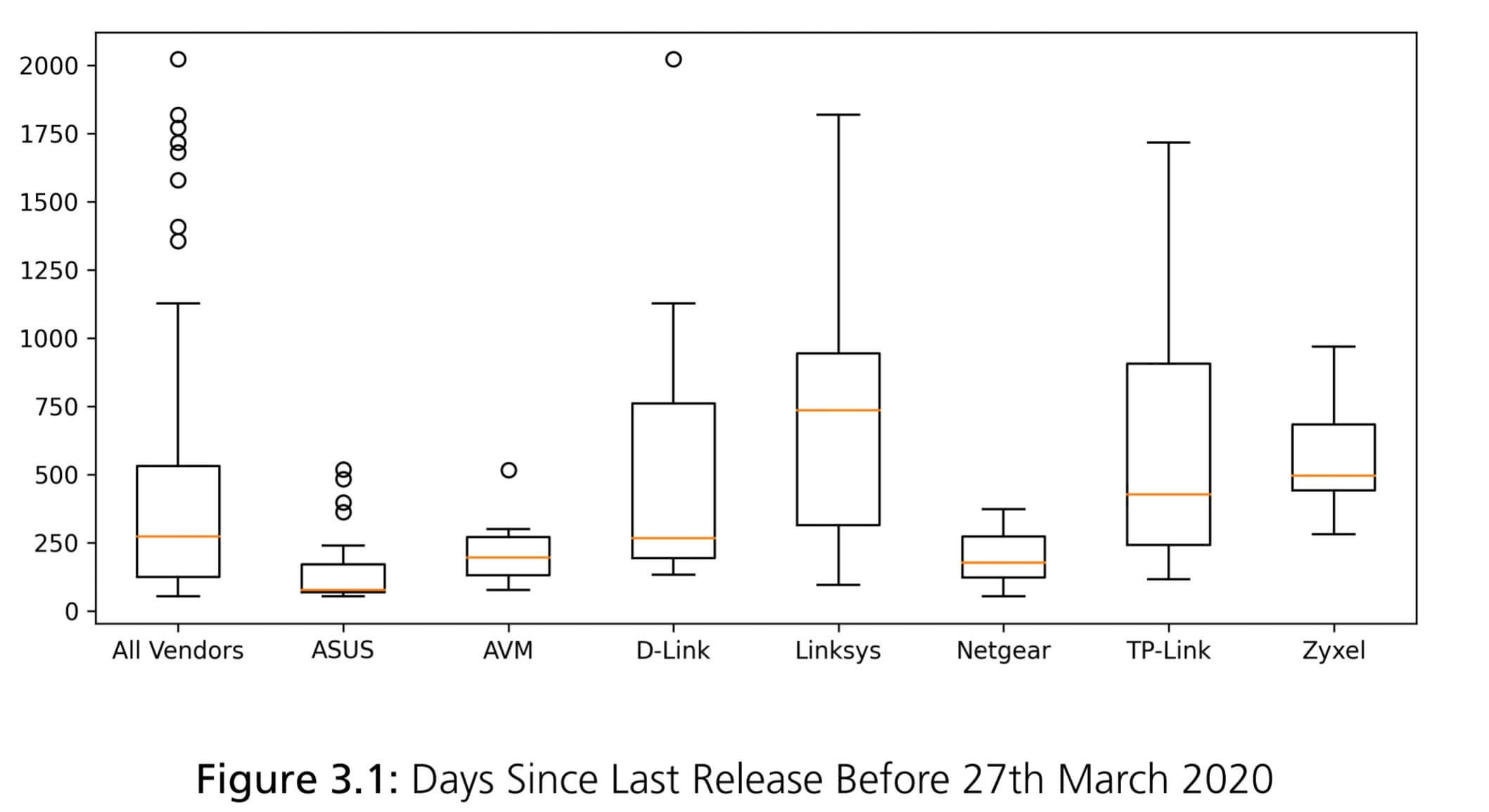
The study, carried out by Germany's Fraunhofer Institute for Communication (FKIE), involved 127 home routers from seven brands: AsusTek Computer Inc., Netgear Inc., D-Link Corp., Linksys, TP-Link Technologies Co. Ltd., Zyxel Communications Corp., and AVM Computersysteme Vertriebs GmbH. It compared the most recent firmware versions from each router with known security vulnerabilities and found not one of them was flawless.
Out of the 127 routers, 46 had not received a single security update within the last year, while 22 had not received any in the last two years. The worst case had gone 1,969 days, more than five years, without security patches. Asus, AVM, and Netgear came out top—all their devices had been updated within the last year and a half—but D-Link, Linksys, TP-Link, and Zyxel were lagging.
Despite around 90 percent of the routers using Linux, many manufacturers weren't updating the OS, with most still on kernel version 2.6 (or older), which last saw an update in February 2011. This leads to a high number of critical and high-severity CVEs affecting these devices.
Fifty of the routers were found to have hard-coded login credentials—default usernames and passwords embedded into the device—while 16 routers have well known or easily crackable credentials. Asus was the only company not storing any hard-coded credentials in its firmware images.
"Our analysis shows that there is no router without flaws and there is no vendor who does a perfect job regarding all security aspects," reads the study's conclusion. "Much more effort is needed to make home routers as secure as current desktop or server systems."
"Vendors prioritize security differently. AVM does better job than the other vendors regarding most aspects. ASUS and Netgear do a better job in some aspects than D-Link, Linksys, TP-Link and Zyxel."
Image credit: Korn