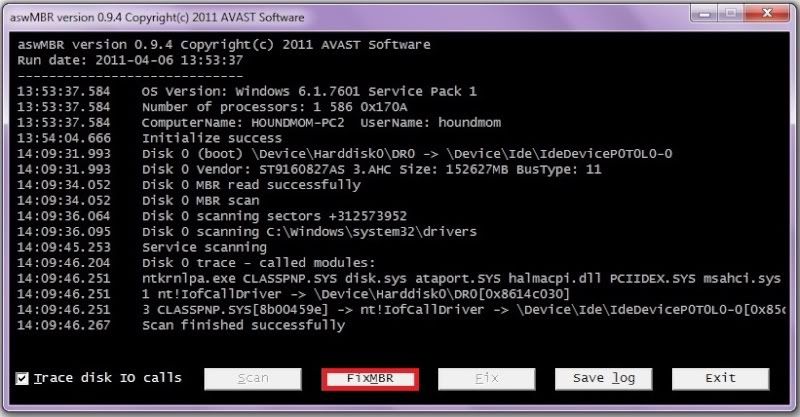
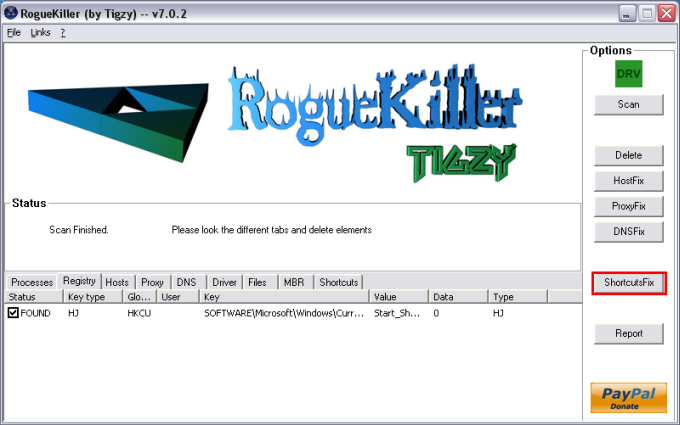
..and here is the other log you requested.
aswMBR version 0.9.9.1665 Copyright(c) 2011 AVAST Software
Run date: 2012-08-15 12:47:39
-----------------------------
12:47:39.429 OS Version: Windows x64 6.1.7601 Service Pack 1
12:47:39.429 Number of processors: 2 586 0x603
12:47:39.429 ComputerName: UER-HP UserName: Uer
12:47:42.079 Initialize success
12:58:16.333 AVAST engine defs: 12081503
12:59:23.638 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\00000064
12:59:23.648 Disk 0 Vendor: Hitachi_ JP4O Size: 953869MB BusType: 11
12:59:23.688 Disk 0 MBR read successfully
12:59:23.688 Disk 0 MBR scan
12:59:23.698 Disk 0 unknown MBR code
12:59:23.708 Disk 0 Partition 1 80 (A) 07 HPFS/NTFS NTFS 100 MB offset 2048
12:59:23.718 Disk 0 Partition 2 00 07 HPFS/NTFS NTFS 941412 MB offset 206848
12:59:23.758 Disk 0 Partition 3 00 07 HPFS/NTFS NTFS 12355 MB offset 1928218624
12:59:23.818 Disk 0 scanning C:\Windows\system32\drivers
12:59:32.738 Service scanning
12:59:54.794 Modules scanning
12:59:54.824 Disk 0 trace - called modules:
12:59:54.844 ntoskrnl.exe CLASSPNP.SYS disk.sys amdxata.sys storport.sys hal.dll amdsata.sys
12:59:54.854 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0xfffffa80076fc060]
12:59:55.064 3 CLASSPNP.SYS[fffff8800277943f] -> nt!IofCallDriver -> [0xfffffa800763ab80]
12:59:55.074 5 amdxata.sys[fffff8800167e7a8] -> nt!IofCallDriver -> \Device\00000064[0xfffffa80076367d0]
12:59:57.184 AVAST engine scan C:\Windows
13:00:02.110 AVAST engine scan C:\Windows\system32
13:02:56.131 AVAST engine scan C:\Windows\system32\drivers
13:03:08.963 AVAST engine scan C:\Users\Uer
13:11:00.037 AVAST engine scan C:\ProgramData
13:13:04.712 Scan finished successfully
13:13:13.788 Disk 0 MBR has been saved successfully to "C:\Users\Uer\Desktop\MBR.dat"
13:13:13.798 The log file has been saved successfully to "C:\Users\Uer\Desktop\aswMBR.txt"
aswMBR version 0.9.9.1665 Copyright(c) 2011 AVAST Software
Run date: 2012-08-15 12:47:39
-----------------------------
12:47:39.429 OS Version: Windows x64 6.1.7601 Service Pack 1
12:47:39.429 Number of processors: 2 586 0x603
12:47:39.429 ComputerName: UER-HP UserName: Uer
12:47:42.079 Initialize success
12:58:16.333 AVAST engine defs: 12081503
12:59:23.638 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\00000064
12:59:23.648 Disk 0 Vendor: Hitachi_ JP4O Size: 953869MB BusType: 11
12:59:23.688 Disk 0 MBR read successfully
12:59:23.688 Disk 0 MBR scan
12:59:23.698 Disk 0 unknown MBR code
12:59:23.708 Disk 0 Partition 1 80 (A) 07 HPFS/NTFS NTFS 100 MB offset 2048
12:59:23.718 Disk 0 Partition 2 00 07 HPFS/NTFS NTFS 941412 MB offset 206848
12:59:23.758 Disk 0 Partition 3 00 07 HPFS/NTFS NTFS 12355 MB offset 1928218624
12:59:23.818 Disk 0 scanning C:\Windows\system32\drivers
12:59:32.738 Service scanning
12:59:54.794 Modules scanning
12:59:54.824 Disk 0 trace - called modules:
12:59:54.844 ntoskrnl.exe CLASSPNP.SYS disk.sys amdxata.sys storport.sys hal.dll amdsata.sys
12:59:54.854 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0xfffffa80076fc060]
12:59:55.064 3 CLASSPNP.SYS[fffff8800277943f] -> nt!IofCallDriver -> [0xfffffa800763ab80]
12:59:55.074 5 amdxata.sys[fffff8800167e7a8] -> nt!IofCallDriver -> \Device\00000064[0xfffffa80076367d0]
12:59:57.184 AVAST engine scan C:\Windows
13:00:02.110 AVAST engine scan C:\Windows\system32
13:02:56.131 AVAST engine scan C:\Windows\system32\drivers
13:03:08.963 AVAST engine scan C:\Users\Uer
13:11:00.037 AVAST engine scan C:\ProgramData
13:13:04.712 Scan finished successfully
13:13:13.788 Disk 0 MBR has been saved successfully to "C:\Users\Uer\Desktop\MBR.dat"
13:13:13.798 The log file has been saved successfully to "C:\Users\Uer\Desktop\aswMBR.txt"