Kali Linux is an open-source, Debian-based Linux distribution geared towards various information security tasks, such as Penetration Testing, Security Research, Computer Forensics and Reverse Engineering.
Because Kali Linux is multi-platform, it gives you a strong, stable, known baseline to operate from regardless of where you use it: desktops, servers, virtual machines, live environments, cloud or containers.
Why is Kali Linux popular among hackers and IT security professionals?
Kali Linux is widely used in the cybersecurity community due to its focus on penetration testing, digital forensics, reverse engineering, and security research. It comes pre-installed with hundreds of tools tailored for ethical hacking. Its mainstream visibility was boosted by popular media like the TV series Mr. Robot, but its utility, reliability, and backing by Offensive Security are what make it a standard in the field.
How many tools does Kali Linux include?
Kali Linux includes over 600 pre-installed tools used for various aspects of cybersecurity. These tools cover everything from network scanning and traffic analysis to password cracking and web application testing. Some of the most well-known tools in Kali Linux are nmap for port scanning, Wireshark for packet analysis, John the Ripper for password cracking, Aircrack-ng for wireless network testing, and Burp Suite and OWASP ZAP for web application security assessments.
How secure is Kali Linux?
Kali Linux is developed with a strong emphasis on security and integrity. Only a small group of trusted developers can commit packages, and each package is signed to ensure authenticity. The distribution also uses a custom kernel that is patched for features such as packet injection, which is essential for wireless network assessments.
Is Kali Linux portable?
Kali Linux is highly portable. It can be installed directly onto a hard drive for regular use, or it can be run in live mode from a USB or CD without installation. It also supports virtualized environments such as VirtualBox and VMware, allowing users to run it within other operating systems. In addition, Kali Linux can be used on Arm-based devices like the Raspberry Pi, through the Windows Subsystem for Linux (WSL), or in cloud environments such as AWS and Azure.
What Linux distribution is Kali Linux based on?
Kali Linux is based on Debian Testing. This foundation gives Kali Linux a stable and widely supported base while allowing it to include newer tools and packages optimized for security research.
What version of Kali Linux should I download?
If you have a 64-bit system and want to install Kali permanently, the standard 64-bit ISO is recommended. For temporary use or testing, the live version allows you to run Kali without installation.
Virtual machine images are ideal for users who prefer to run Kali in a controlled environment, and Arm images are available for devices like the Raspberry Pi. For Android-based penetration testing, Kali NetHunter is the appropriate version. If you're using Windows 10 or 11, Kali Linux can also run through the Windows Subsystem for Linux.
Can I use Kali Linux as my daily OS?
While technically possible, using Kali Linux as a daily driver is generally discouraged. Kali is optimized for security testing, not for general-purpose computing. It may lack certain conveniences and stability found in mainstream distributions, and using it for everyday tasks could pose security risks if not properly managed.
What's New
Kali Linux 2025.2 Release (Kali Menu Refresh, BloodHound CE & CARsenal)
We're almost half way through 2025 already, and we've got a lot to share with you in this release, Kali 2025.2.
The summary of the changelog since the 2025.1 release from March is:
- Desktop Updates - Kali-Menu refresh, GNOME 48 & KDE 6.3 updates
- BloodHound Community Edition - Major upgrade with full set of ingestors
- Kali NetHunter Smartwatch Wi-Fi Injection - TicWatch Pro 3 now able to de-authenticate and capture WPA2 handshakes
- Kali NetHunter CARsenal - Car hacking tool set!
- New Tools - 13 new shinny tools added (and various updates)
Kali Menu Refresh
We've completely reworked the Kali Menu! It's now reorganized to follow the MITRE ATT&CK framework structure – which means that finding the right tool for your task should now be a lot more intuitive for red and blue teams alike.
Previously the Kali menu structure followed what was in BackTrack… which followed WHAX before it. The previous structure was an in-house item, before MITRE was a thing. When our menu was first created, there wasn't as much design planning done, which we suffered for later. It meant that over time, scaling and adding new tools became difficult for us. The knock on effect was that this made it harder for you, the end-users, to discover new tools as similar tools with overlapping functions were in different places or missing entries. Yes, seasoned professionals may not use the menu to start up items, using shortcuts such as super key and typing the tool name, or via a terminal window. We see the menu as a way to discover tools.
The final nail in the coffin in the setup was the fact that it was manually managed. Yes, all those entries were previously created by-hand (which also may explain a few things). As a result, we had stopped adding new tools to the menu… until now.
Now, we have created a new system and automated many aspects, making it easier for us to manage, and easier for you to discover items. Win win. Over time, we hope to start to add this to kali.org/tools/.
Currently Kali Purple still follows NIST CSF (National Institute of Standards and Technology Critical Infrastructure Cybersecurity), rather than MITRE D3FEND.
This is a big change, and we want your feedback! Think something should be renamed, moved, or see a tool that's missing? Help us improve the menu by editing the structure directly – it's all open and managed through a simple YAML file.
GNOME 48
GNOME has been bumped up to version 48, and brings with it:
- Notification Stacking
- Performance Improvements
- Dynamic triple buffering
- Enhanced Image Viewer
- Digital Wellbeing
- Preserve Battery Health
- HDR (High Dynamic Range) Support
- Updated Text Editor
As with previous GNOME updates in Kali, we've given all our themes a fresh coat of paint – everything's been tuned to look sharp and feel smooth. The document reader evince has been replaced with the new papers app. If you're rocking Kali with GNOME, this update is definitely worth the reboot. Want the full scoop? Check out the official GNOME 48 release notes.
New GNOME VPN IP Extension
Just like we did for Xfce back in Kali 2024.1, we've now brought the VPN IP indicator to GNOME too!
It shows the IP address of your current VPN connection right in the panel – and with a simple click, it copies it straight to your clipboard. Handy, right?
Huge thanks to @Sarthak Priyadarshi who not only came up with the idea, but also provided all of the coding to make it happen. Community contributions like this make Kali better for everyone!
KDE Plasma 6.3
KDE Plasma fans, rejoice – we've included Plasma 6.3, and it's packed with polish:
- Huge overhaul of fractional scaling
- Accurate screen colors when using the Night Light
- More accurate CPU usage in system sonitor
- Info Center provides more information, like GPUs data or batteries' cycle counts
- More customization features
Whether you're into tiling window madness or prefer a traditional desktop setup, Plasma 6.3 brings both flexibility and style. You can read more about all the new changes for Plasma desktop in their official release post.
New Community Wallpapers
There are also new changes in the Community Wallpapers package (pkg), including 2 new backgrounds provided by @Onix32032044 and 1 background provided by @Arszilla.
To access these wallpapers, simply install the kali-community-wallpapers package, which also offers many other stunning backgrounds created by our community contributors.
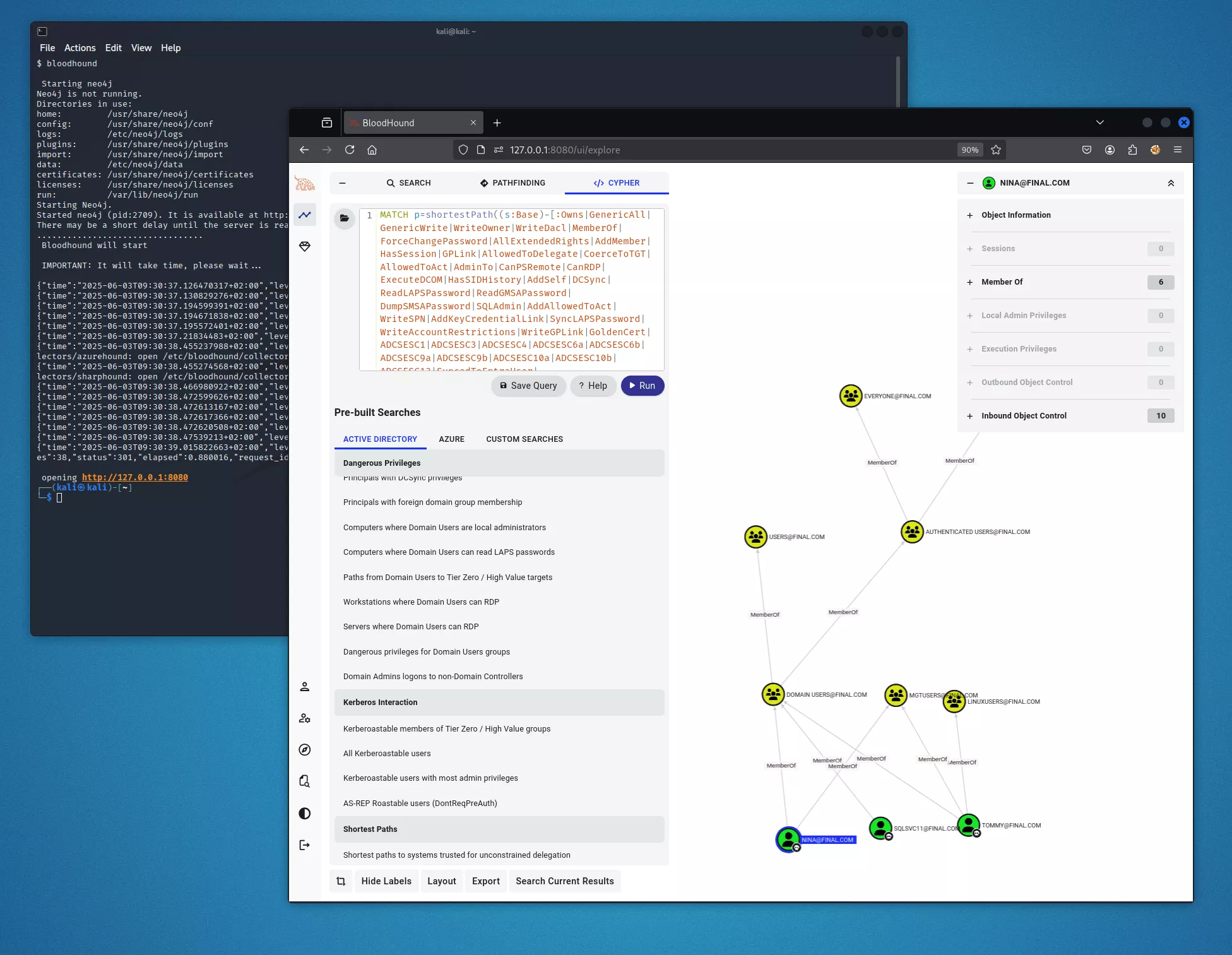
BloodHound Community Edition
If you're doing Active Directory recon, this upgrade is a game changer. BloodHound just got a major upgrade – we've bumped it up to the latest version: BloodHound Community Edition (CE). With this update, we're also shipping the full set of ingestors to support it:
- azurehound
- bloodhound-ce-python
- sharphound
So what's new in BloodHound CE? Expect a smoother interface, better performance, and new capabilities for mapping complex Active Directory environments.
You can check our guide about how to configure a new installation of Bloodhound-CE in Kali here.
New Tools in Kali
It would not be a Kali release if there were not any new tools added! A quick run down of what has been added (to the network repositories):
- azurehound - BloodHound data collector for Microsoft Azure
- binwalk3 - Firmware Analysis Tool
- bloodhound-ce-python - Python based ingestor for BloodHound CE
- bopscrk - Generate smart and powerful wordlists
- chisel-common-binaries - Prebuilt binaries for chisel
- crlfuzz - Fast tool to scan CRLF vulnerability written in Go (Submitted by @Arszilla)
- donut-shellcode - Generates position-independent shellcode from memory and runs them
- gitxray - Scan GitHub repositories and contributors to collect data (Submitted by @weirdlantern)
- ldeep - In-depth LDAP enumeration utility
- ligolo-ng-common-binaries - Prebuilt binaries for Advanced ligolo-ng
- rubeus - Raw Kerberos interaction and abuses
- sharphound - BloodHound CE collector
- tinja - CLI tool for testing web pages for template injection
There has also been numerous new libraries as well as packages updates as well, such as PowerShell and code-oss.