A SED, or self-encrypting drive, is a type of hard drive that automatically and continuously encrypts the data in it without any user interaction. What may surprise many is that a decent potion of the drives currently in the market, including the popular Samsung 840 Pro SSD series are in fact SEDs. But since manufactures do not tout this as a major feature, it often gets lost in the large number of typically more important specifications.
Even once you purchase, install, and start using one of these SED drives, the encryption is so transparent to the user that it is unlikely they would ever realize the drive is a SED.
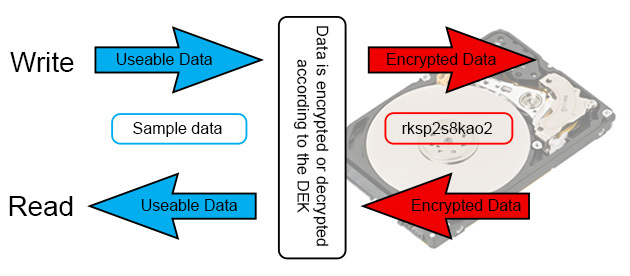
This encryption process is done through the use of a unique and random Data Encryption Key (DEK) which the drive uses to both encrypt and decrypt the data. Whenever data is written to the drive, it first gets encrypted according to the DEK. Similarly, whenever data is read from the drive, it first gets decrypted by the same DEK before being sent to the rest of the system.
Guest author Matt Bach is the head of Puget Labs and has been part of Puget Systems, a boutique builder of gaming and workstation PCs, since the early days working in various subsets of production. This article was originally published on the Puget blog.
This means that all the data on the drive is encrypted at all times. One neat trick that can be done based on this is to almost instantly and completely wipe a hard drive. All you need to do is tell the SED to generate a new DEK and all the data on the drive immediately becomes gibberish (since the key needed to decrypt the data no longer exists) and is effectively unretrievable. So if you need to quickly and securely wipe a drive before either redeployment or disposal, SEDs offer a quick and very secure way to do so.
This act is called a number of different names depending on the manufacturer, although it is most often referred to as doing a "Secure Erase".
What is SED Encryption?
While having the data encrypt and decrypt automatically on a hard drive is neat, it isn't really all that useful on its own since the hard drive will automatically decrypt the data on request. However, SEDs also allow you to set what is called an Authentication Key (AK) which acts as a password that locks the drive until the key is entered. If an Authentication Key is set up, the system will prompt for the key when it first powers on. While the number of attempts varies by the motherboard, if you put in the incorrect password after three or four attempts, the system will simply keep the drive locked and continue the boot process. If that happens, the drive becomes completely unusable until the computer is powered off and the correct key is entered.
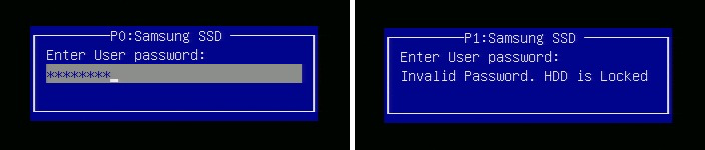
In fact, even if you remove it from the original computer and plug it into a different computer the drive will still require the AK to be entered in order for the drive to unlock. However, if you you plug it into a system that does not support SED encryption, the drive will be unusable. Since the motherboard does not have the ability to enter the Authentication Key, the drive never knows to unlock itself. The result is that the drive will remaining locked with no way to unlock it. Unless you move the drive to a system that supports SED encryption, there is no way to retrieve the data on that drive.
According to Seagate, this method of encryption has been certified by both the NIST and CSE as meeting the requirements for level 2 security for cryptographic modules.
Downsides of SED encryption
When data security is a goal, it is essential to know the limitations and drawbacks of a certain technology. SEDs are a great technology, but they are no different than anything else in that they certainly have downsides. In the case of SEDs, the main downside is that once the drive has been unlocked, it remains so until the power to the drive has been cut. In other words, if you simply reboot the computer or put it into sleep, the drive remains unlocked. It is not until you completely power off the computer that it will again require the Authentication Key to be entered.
In other words, if your laptop is stolen and it was only in sleep mode then the data on the drive is completely exposed. If you have a user password set on the OS, a thief could still simply restart the machine, boot into a live environment, and have almost full access to your data. In fact, even if you have both an OS password and a BIOS password set, the data still could be accessed by moving the drive to a different computer without cutting the power. In laptops this would be tricky (but not impossible) but on a desktop is actually rather easy with the right setup.
So if you do decide to use SED encryption, our biggest advice is to get into the habit of powering off your system when it is not in use rather than simply putting it to sleep.
A second downside to SED encryption is that it will only work in simple disk configurations. You can have multiple drives in one system with SED encryption enabled and even use software RAID, but doing something like hardware-level RAID is simply not supported.
What is needed for SED encryption to work?
Something we've found is that full support for SED is actually very poor. There are plenty of hard drive and SSD models that support SED encryption (although finding them can be difficult), but full support for SED also requires a compatible motherboard.
Some features of SED (like the automatic encryption and decryption of data and Secure Erase) will work regardless of the motherboard. But if you want to use SED encryption by setting an Authentication Key, you need a motherboard that supports doing so.
Many laptops have the ability to use an Authentication Key without any need for a custom BIOS. However, they often lack the ability to set the AK though the BIOS. Of course, this doesn't mean that every laptop will support SED encryption, but in our experience laptops in general are much more likely to support it than desktop or server motherboards.
While talking with Asus, Super Micro, and Samsung, we have discovered that most desktop and server motherboards do fully support SEDs, but the ability to use an Authentication Key is expressly disabled. The reason for this appears to be that manufactures are afraid that a user may accidentally lock their hard drive and not remember what they used for the Authentication Key. So rather than risk having an angry customer that accidentally locked their drives, they leave that specific feature of SEDs disabled. That said, we've had success with getting custom BIOS files from the manufacturer that unlocked the ability to use Authentication Keys.
Managing SED encryption passwords
On a motherboard that fully supports SED encryption, there is a chance that there is an option in the BIOS setup to set, change, or remove the SED Authentication Key on your SED drive. However, we have found that many motherboards that support SED do not have this capability built into the BIOS. In those cases, you could use software like Winmagic to manage the SED encryption key, or you can go through a series of steps using a Linux live environment to manage the SED Authentication Key without the need for paid software.
You can follow the directions from Ubuntu on how to create a LiveCD that should include everything you will need. Once your system has booted into the Linux live environment, there are three combinations of steps you must go through in order to either set, remove, or change the SED encryption password.
- No matter what you want to do, you must first locate the drive that you want to manage the SED encryption password on and unfreeze it.
- Next, if you want to change the SED encryption password or remove SED encryption entirely, you need to disable SED encryption.
- Finally, you need to enable SED encryption with a new password if you are either changing the SED encryption password or setting a new SED encryption password.
Locating and unfreezing the drive
Open a terminal from the unity toolbar or with the hotkey combination "ctrl+T"
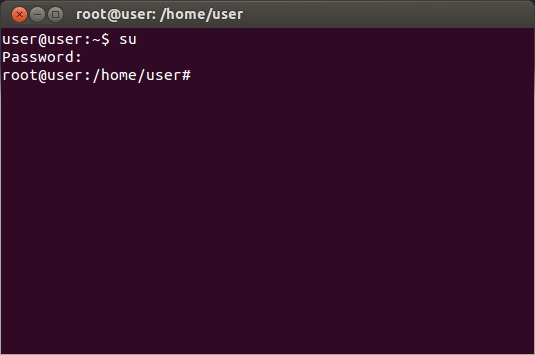
Enable root privileges by entering the command 'su'. You will be prompted for a password.
Enter the command "lsblk" which will output a list of the drives that are in the system. Locate the name of the drive (sda, sdb, etc.) that you want to change the encryption password or disable SED encryption on.
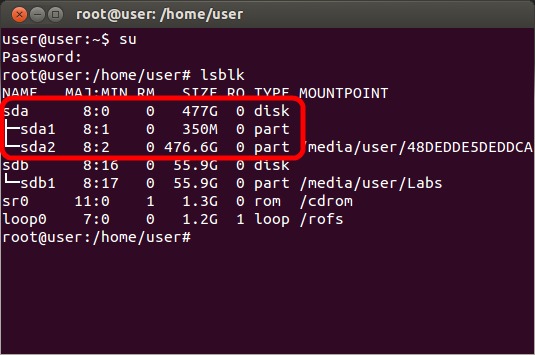
Enter the command "hdparm -I /dev/X" where X is the drive name (sda, sdb, etc.) to check the current status of the drive. Be sure to use "-I" which is an uppercase i, not a one or lowercase L. Check to make sure that there is a line that says "enabled". If that line instead says "not enabled", then SED encryption is not currently enabled on that drive. Either SED encryption was never configured, or you are using the incorrect hard drive name (sda, sdb, etc.)
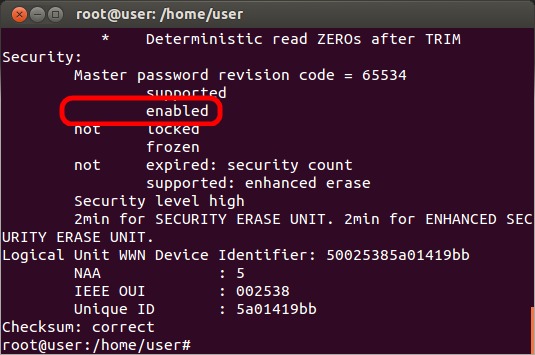
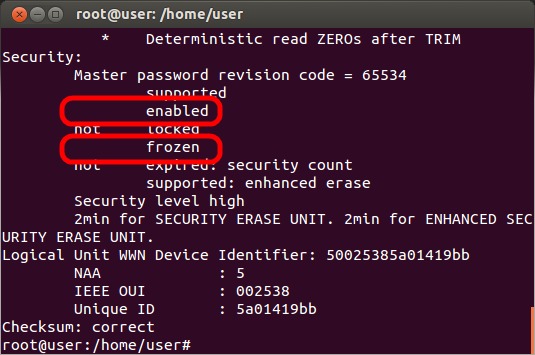
Typically, the drive will be marked as frozen (indicated by a line that says "frozen") and will need to be unfrozen before continuing. To unfreeze the drive, put the system to sleep by clicking on the gear icon at the top-right of the screen and selecting "Suspend". After ~10 seconds, hit the power button to wake the system up.
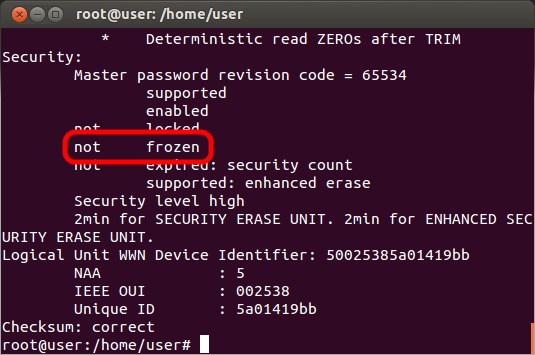
Repeat the "hdparm -I /dev/X" command to verify that the drive is now marked as "not frozen". If it is still frozen, you will need to physically disconnect the drive for a few seconds while the system is in the live environment then repeat the command.
Disable the current SED encryption
After following the steps to locate and unfreeze the drive, run the command "hdparm --security-disable PASSWORD /dev/X" where PASSWORD is the current SED password and X is the drive name (sda, sdb, etc) to remove the current SED encryption. If you wish to leave SED disabled, then the process is complete. If you want to reset SED with a new password, read on.
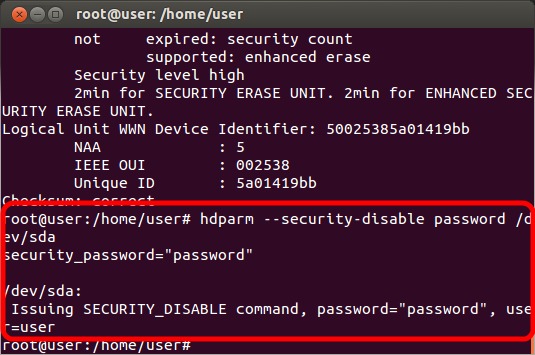
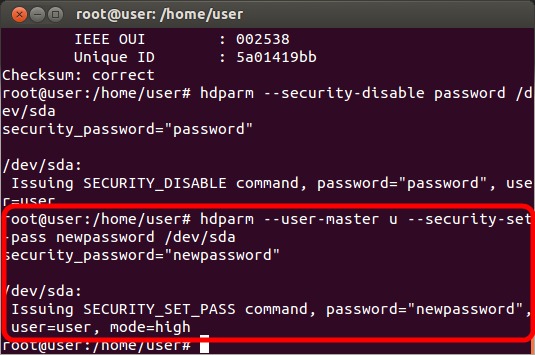
Enable SED encryption with a new password
After following the steps to locate and unfreeze the drive then to disable SED encryption, next enter the command "hdparm --user-master u --security-set-pass PASSWORD /dev/X" where PASSWORD is the password you want to use and X is the drive name (sda, sdb, etc.) to re-enable SED encryption with a new password.
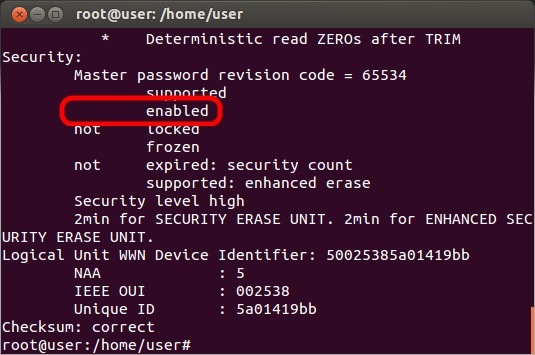
Enter the command "hdparm -I /dev/X" again and look for the line "enabled" (instead of "not enabled") to ensure that SED is enabled. At this point you should completely power off your system (not a standard reboot) to ensure that the SED password is set properly.
Conclusion
After working with SED encryption and seeing how well it works, we are actually very surprised at how little support it has on modern motherboards. In fact, many motherboard manufacturers actively disable SED encryption and require a custom BIOS in order to make it active. Other motherboards, however, do support SED encryption although the ability to manage the password is not available from the BIOS. In those cases, you can still use SED encryption but you need to go though an unwieldy process involving a Linux live environment.
Overall, we have found that SED encryption is great as long as you do your homework and know that it will work on your system. Self-encrypting drives have their downsides (largely that it only requires the password to be entered when the machine is first turned on), but it is easy to use and effective for a very wide range of applications.
If you are interested in encrypting your data, we highly recommend checking out SED encryption before considering options like Bitlocker or other software-based encryption.
Do you use hard drive encryption in your computer, either SED encryption or something else? Let us know about your experience in the comments below!
Header image via Shutterstock
