The big picture: Despite the growing efforts of law enforcement and investigators, ransomware remains one of the most dangerous threats on the internet. The number of victims is increasing, and new groups appear highly motivated to achieve their malicious objectives.
September saw a record number of ransomware operations, as indicated in a recently released report by NCC Group. The company's latest "monthly cyber threat intelligence report" focuses on emerging developments in the threat landscape, particularly in the realm of ransomware attacks and cybercrime groups engaged in well-established digital extortion activities.
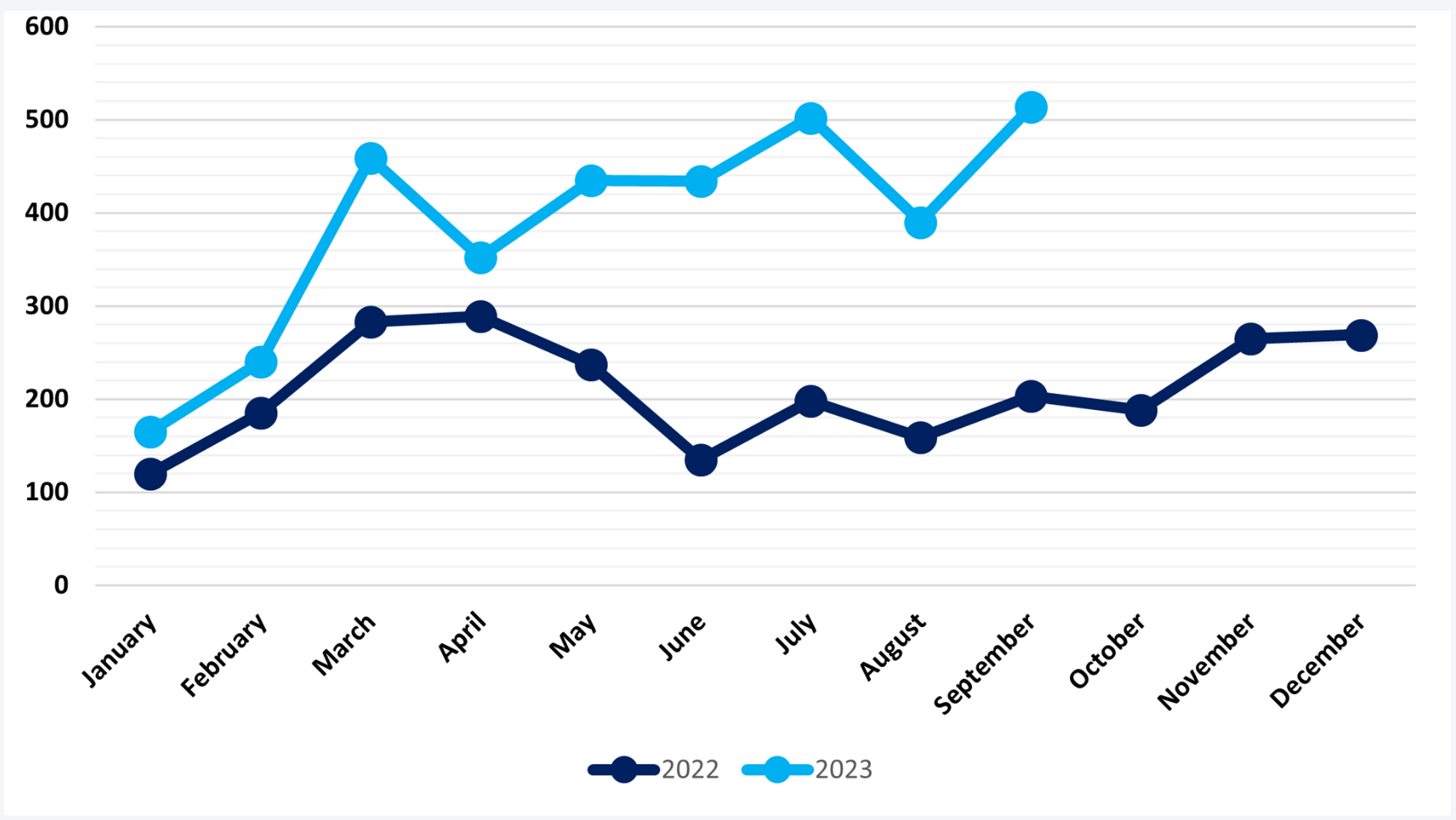
In September 2023, ransomware groups carried out 514 attacks, marking a 32 percent increase compared to the previous month. While August 2023 was a relatively quiet month for ransomware, the number of attacks still exceeded the typical rates for the summer period. In comparison to 2022, ransomware incidents increased 153 percent.
In NCC Group's previous "Threat Pulse" report, an estimate suggested that we might see a total of 4,000 attacks by year's end. The new report reveals that the number of incidents has already reached 3,500, making it highly likely to exceed 4,000 before 2024.
The top five most active groups involved in ransomware threats in September 2023 are all new actors. According to NCC Group, this indicates that these new cybercriminals are eager to kick off their malicious activities "with a bang." The record-setting ransomware crews include LockBit 3.0 (79 attacks), LostTrust (53), BlackCat (47), and RansomedVC (44).
NCC Group is dedicating a significant effort to analyze RansomedVC, a recently established cybercrime operation that began to emerge in August 2023 within the underground forums. The individuals behind RansomedVC describe themselves as "penetration testers" and have introduced a novel approach to extortion tactics, revolving around fabricated reports of GDPR fines related to network vulnerabilities.
The RansomedVC operation is still relatively new, as per NCC Group's assessment, which means that there's limited information available about this group. The underground forum, launched in early August, was overseen by two administrators known as "Admin" and "Yuna." They implemented a credit system to incentivize members to leak undisclosed data. Notably, RansomedVC is the group that claimed responsibility for breaching all of Sony's networks in September.
NCC Group's report also highlights the most targeted sectors in ransomware incidents, with "industrials" (construction, engineering, services) accounting for 40 percent of all attacks, followed by consumer cyclicals (retail, media, hotels) at 18 percent, and technology at 10 percent.