Dasvidania Tovarish: Infostealers are a dangerous class of malware built to infiltrate systems and extract sensitive personal or corporate data. Lumma Stealer ranks among the worst offenders, prompting Microsoft and global law enforcement to go after its alleged mastermind.
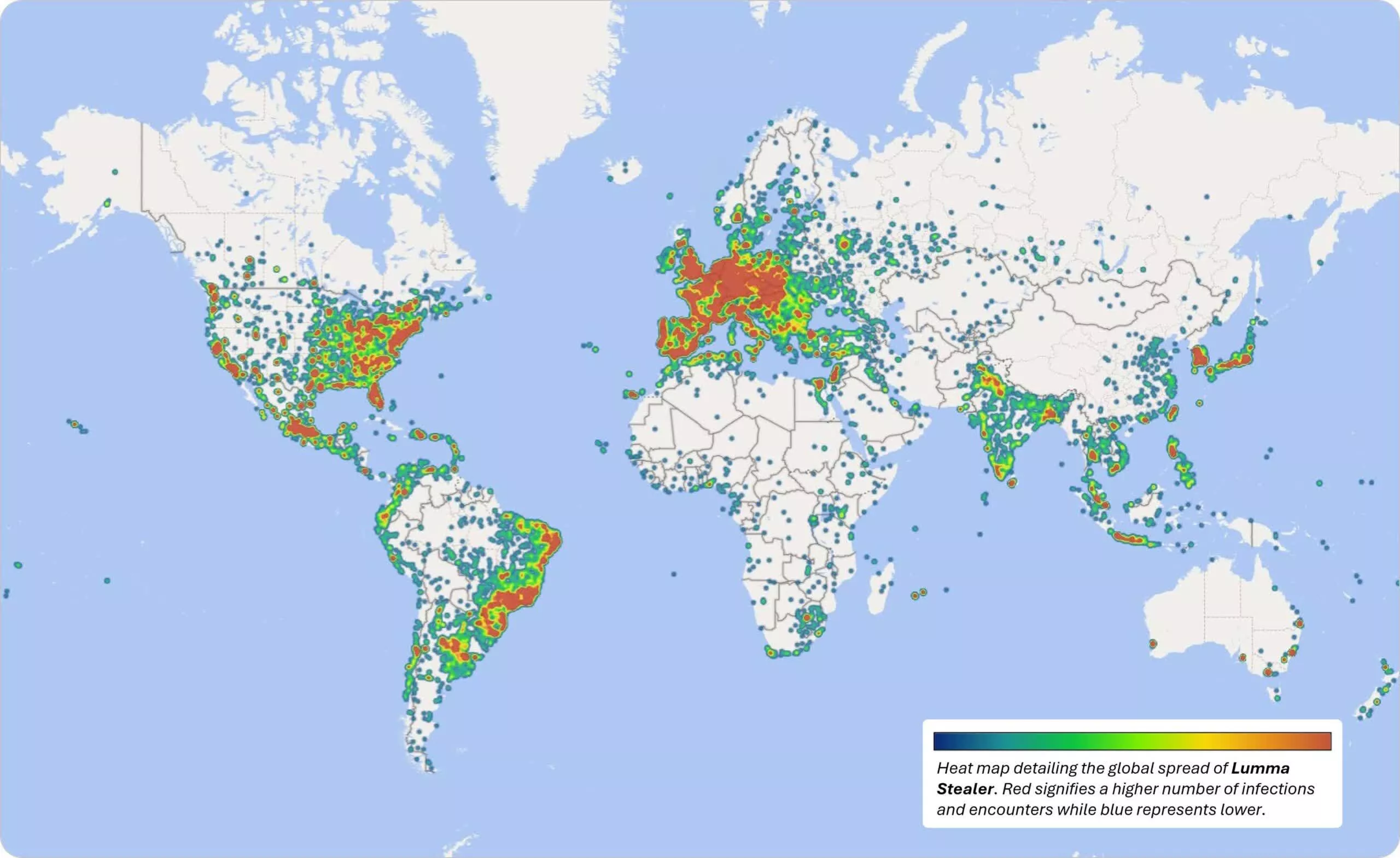
Microsoft says its Digital Crimes Unit (DCU) successfully disrupted the server infrastructure behind Lumma Stealer, a malware-as-a-service (MaaS) operation that infected hundreds of thousands of Windows PCs. Cybercriminals worldwide used LummaC2 to steal passwords and credit cards, drain crypto wallets, disrupt critical services, and more.
Microsoft's DCU worked with a federal court in Georgia, the Department of Justice, Europol, and Japan's Cybercrime Control Center to dismantle Lumma's infrastructure. Redmond blocked roughly 2,300 malicious domains that served as the backbone of the operation.
Microsoft identified more than 394,000 Windows systems infected by Lumma malware between March 16 and May 16. The seized domains now redirect to Microsoft-controlled sinkholes, which protect users while providing analysts with fresh insights into the malicious operation. With its infrastructure dismantled, the Lumma enterprise has effectively shut down.
The malware ring has "rented" Lumma on underground markets since 2022. The malware evolved to offer increasingly advanced features to its criminal customers. Microsoft analysts claim LummaC2 can siphon browser credentials and cookies, locate locally stored cryptocurrency wallets and extensions, and target VPNs along with various internet applications.
Furthermore, Lumma collects various document types (PDF, DOCX, RTF) from the local user profile and steals metadata about the infected machine for further exploitation. The malware spreads through multiple channels, including phishing emails, malvertising, drive-by downloads from compromised sites, and fake Captcha challenges. Other malware specimens can also drop Lumma as an additional threat.
Microsoft identified the primary developer behind Lumma as a Russian hacker known online as "Shamel." In a recent interview with a cybersecurity researcher, the hacker claimed to have around 400 active customers. That is likely no longer the case, as Windows Defender and other Microsoft endpoint security tools now reliably detect the all-but-defunct malware. Third-party antivirus programs probably flagged it well before authorities dismantled the operation.
"Disrupting the tools cybercriminals frequently use can create a significant and lasting impact on cybercrime, as rebuilding malicious infrastructure and sourcing new exploit tools takes time and costs money," Redmond said.