The Duqu and Stuxnet malware heralded in a new era in cyber warfare, and brought cyber-espionage to the forefront of security experts minds. In many ways this has also resulted in the general public becoming increasingly sensitive to the almost never-ending barrage of virus and malware related threats.
Now leading security experts are announcing the latest threat, codenamed Flame, which targets the Middle East once again. Analysts say it's one of the most comprehensive and complex forms of malware ever analyzed, and has been written with intelligence gathering as its primary function.
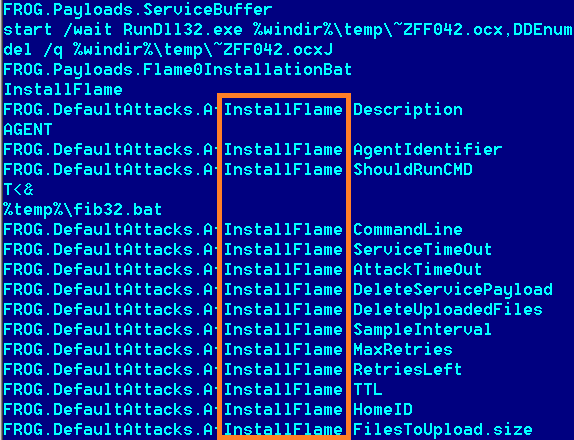
"Flame is a sophisticated attack toolkit, which is a lot more complex than Duqu. It is a backdoor, a Trojan, and it has worm-like features, allowing it to replicate in a local network and on removable media if it is commanded so by its master," said Alexander Gostev, a Kaspersky Lab Expert on their official blog.
The malware is approximately 20MB in size, and has around 3,000 lines of code across 20 different modules. Kaspersky says it has been in the wild since at least February 2010, but other reports claim it could be up to five years. Once a system is infected it begins a complex set of operations which include sniffing out network traffic, taking screenshots, recording audio conversations, intercepting key strokes and other intelligence gathering functions.
Flame compresses all intelligence gathered and is designed to regularly send it to the operators at the command servers via "a covert" SSL channel, which like many aspects of the complex malware is still being investigated. Even more alarmingly, the operators can then choose to upload other modules to expand the malware's functionality further.
It appears to be targeting Iran and Israel with the highest frequency so far, with infections also confirmed in several other countries in the Middle East. Analysis has so far excluded it as the work of hacktivist or cybercriminal entities, leading Kaspersky to confirm it's definitely the work of a sponsored nation state.
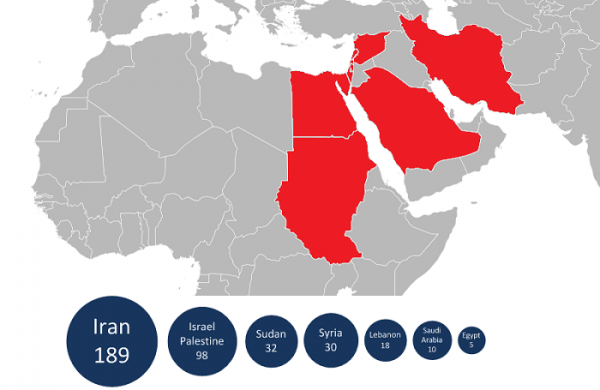
"In addition, the geography of the targets (certain states are in the Middle East) and also the complexity of the threat leaves no doubt about it being a nation state that sponsored the research that went into it," Gostev said. He did note that no information had been found in the code that would suggest any specific government was to blame, but other sources claim the origin as either Israel or the USA.
Iran is certain it originated from Israel. "Its encryption has a special pattern which you only see coming from Israel," said Kamran Napelian, an official with Iran's Computer Emergency Response Team when speaking with the NY Times. "Unfortunately, they are very powerful in the field of I.T."
While the malware is a serious threat it does appear to have been used to target specific infrastructure and as such poses little risk to internet users at this point. Whether this changes depends solely on whether Flame's code is leaked and subsequently reverse-engineered by cybercriminals.