Cisco has announced in their 2017 Midyear Cybersecurity Report that malicious software attacks may leave more lasting effects than the recent widespread ransomware epidemic and massive distributed denial of service (DDoS) attacks.
Permanent physical damage as a result of cyber attacks is a real world consequence of modern malicious software. Infamous malware package Stuxnet showcased the abilities of software to cause serious and irreversible damage in the real world almost a decade ago by crippling Iranian nuclear facilities.
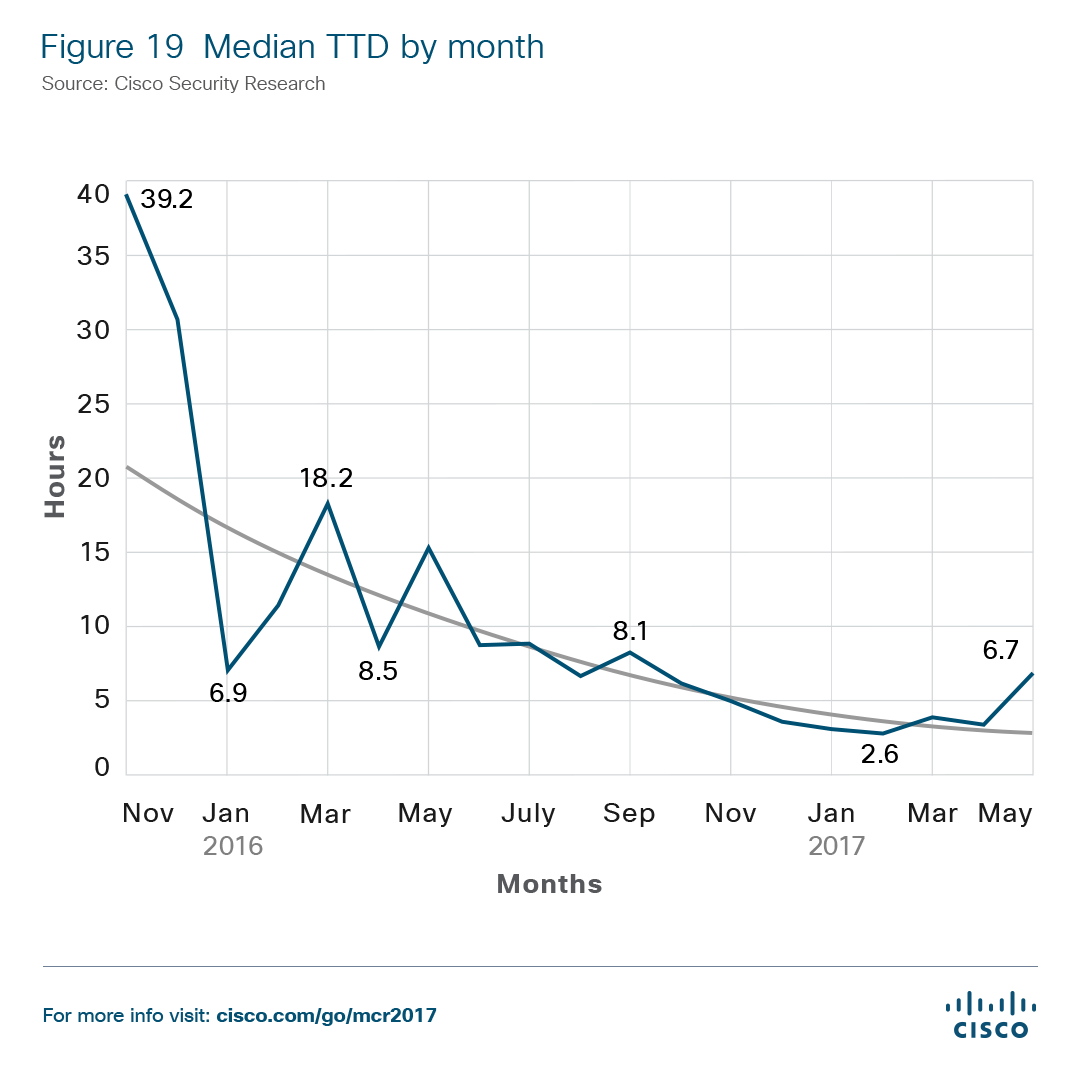
As the threat landscape changes, Cisco is warning that there will be a rise in destruction of service (DeOS) attacks that can permanently disable hardware. Flashing or corrupting the firmware on internet connected devices has been observed as a fast growing trend. Even though the median time to detection for intrusions and infections has dropped to less than eight hours, the fact that software might not be able to fix damages should be highly concerning.
Although destructive malware might be on the rise, the use of exploit kits is steadily declining in favor of more sophisticated social engineering attempts to compromise email. Between 2013 and 2016, business email compromises generated $5.3 billion for hackers.
Cisco reports that user interaction in order to install or execute malware is occurring more often than ever before. Using dialog boxes, word documents with linked embedded objects, and password protected archive files, users are being manipulated into willfully running malicious files. Antivirus and anti-malware software can only be effective if the user leaves it running and does not ignore warnings.
The most valuable thing that cyber criminals are after is data. Spyware is being disguised as seemingly functional software in order to steal individual and business information. Knowledge of infrastructure also allows for more precise attacks to be made in the future. Examples of recently found spyware include free VPNs designed to collect user data and DNS changers masquerading as a legitimate means to bypass geofencing on popular websites. Potentially unwanted programs were found on over 20% of Cisco's sample group comprised of 300 companies.
While implementing security measures on PCs is common practice, internet of things devices are also garnering the attention of IT professionals. Botnets run off of IoT devices were used to extort businesses by threatening DDoS attacks if a ransom were not paid. As a greater number of common devices are beginning to support internet connections, this attack vector is likely to continue to grow at an alarming rate.
No matter how fast intrusion detection systems and antivirus software are developed, it is assured that attackers will always try to remain one step ahead. The key takeaway should be that having regularly checked active security measures in place as well as a backup plan for when critical systems are down is essential for both consumers and enterprise users.
