Why it matters: The Wireless Emergency Alert (WEA) system is meant to allow the president to promptly broadcast alert messages to the entire connected US population in case of a nationwide emergency. It can also send out bad weather or AMBER alerts to notify citizens in a particular region or locality, thus making its operation critical. However, the system utilizes LTE networks that researchers have been able to exploit, enabling the transmission of spoofed messages that can cause wide spread of misinformation and panic among the masses.
Researchers at the University of Colorado Boulder have recently published a paper which details the flaws in 4G LTE networks that can allow sending of spoofed alerts via the Wireless Emergency Alert (WEA) system, reports TechCrunch.
The vulnerabilities in the network can be exploited using both commercially available hardware and "modified" open source software. Using four malicious portable base stations, an attack can be sent to cover a 50,000-seat stadium, which the researchers were able to successfully demonstrate with a 90 percent success rate.
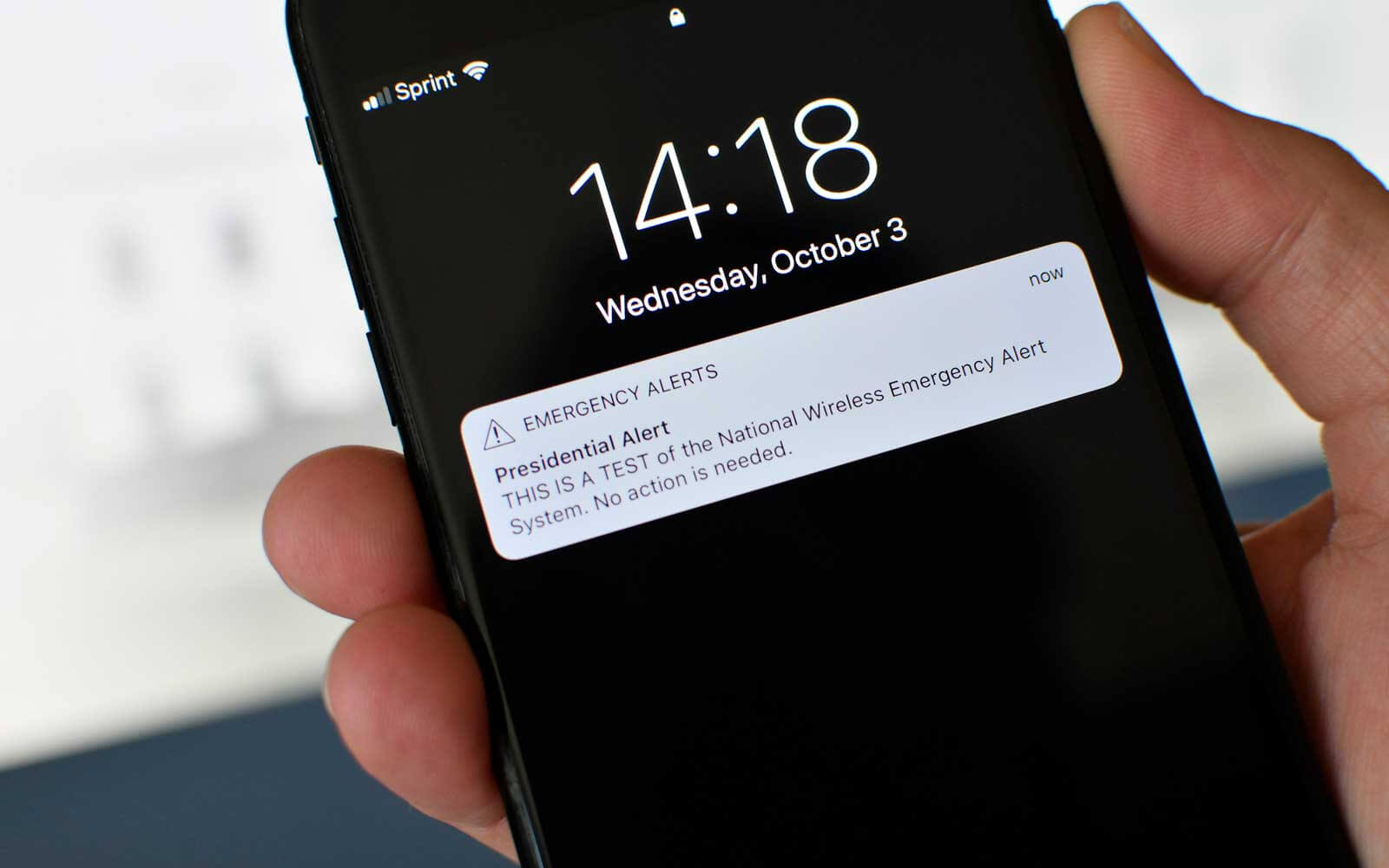
The WEA system, which began its nationwide testing last year, is able to broadcast Presidential, Imminent Threat and AMBER Alerts. While the last two can be disabled by users on both iPhone and Android phones, Presidential Alerts are mandatory and cannot be turned off.
"The true impact of such an attack would of course depend on the density of cell phones in range; fake alerts in crowded cities or stadiums could potentially result in cascades of panic."
Malicious alerts can be transmitted through WEA once the specific LTE channel it uses to broadcast them is identified. What makes things worse is that phones have no way to verify the authenticity of an alert so it can either be a genuine alarm or a human error accidentally notifying Hawaii residents of an inbound ballistic missile threat.
Fixing the vulnerabilities will "require a large collaborative effort between carriers, government stakeholders and cell phone manufacturers," the researchers say, while also discussing two potential defenses against such attacks. The first being digital signatures added to alerts for authenticity and second using secure commercial mobile alert service (CMAS) for better LTE resiliency.
Both solutions do come with their own challenges. Digital signatures would need operators and devices to agree on the key(s) to sign and validate messages, handling signatures from unknown keys and requiring signatures to fit "within the practical constraints of the network." The researchers suggest to use digital signatures for Presidential Alerts only since owing to just one originator, the key distribution would be much simpler.
Secondly, a secure CMAS would require implementation at either LTE modem firmware level or an update to the phone OS with a major disadvantage being limited access of trustworthy CMAS messages to end-users. Both measures, however, could significantly reduce the risk of a spoofing attack, according to the researchers.