The big picture: PDF encryption, as you can imagine, is commonly used in the world of business to protect trade secrets, confidential images and even health records. Some even send e-mail messages as encrypted PDF attachments for increased security. These methods are generally considered secure as the password to decrypt them can be sent over a secondary channel, like a text message, via voice call or presumably, even by good ole snail mail.
Researchers from Ruhr-University Bochum and Munster University have discovered what they are calling "severe weaknesses" in the Portable Document Format (PDF) encryption standard that can reportedly lead to the ability to capture full plaintext in an active-attacker scenario.
In other words, the researchers found that it is possible to acquire the contents of an encrypted PDF without having the requisite encryption keys.
It's all a bit technical if you aren't up to speed on this sort of thing but according to the researchers, the problems - dubbed PDFex - can be summarized as such:
- Even without knowing the corresponding password, the attacker possessing an encrypted PDF file can manipulate parts of it.
- More precisely, the PDF specification allows the mixing of ciphertexts with plaintexts. In combination with further PDF features which allow the loading of external resources via HTTP, the attacker can run direct exfiltration attacks once a victim opens the file.
- PDF encryption uses the Cipher Block Chaining (CBC) encryption mode with no integrity checks, which implies ciphertext malleability.
- This allows us to create self-exfiltrating ciphertext parts using CBC malleability gadgets. We use this technique not only to modify existing plaintext but to construct entirely new encrypted objects.
This is just a basic breakdown of the issue. For a full rundown of the technical details of the attack, head over and check out this blog post.
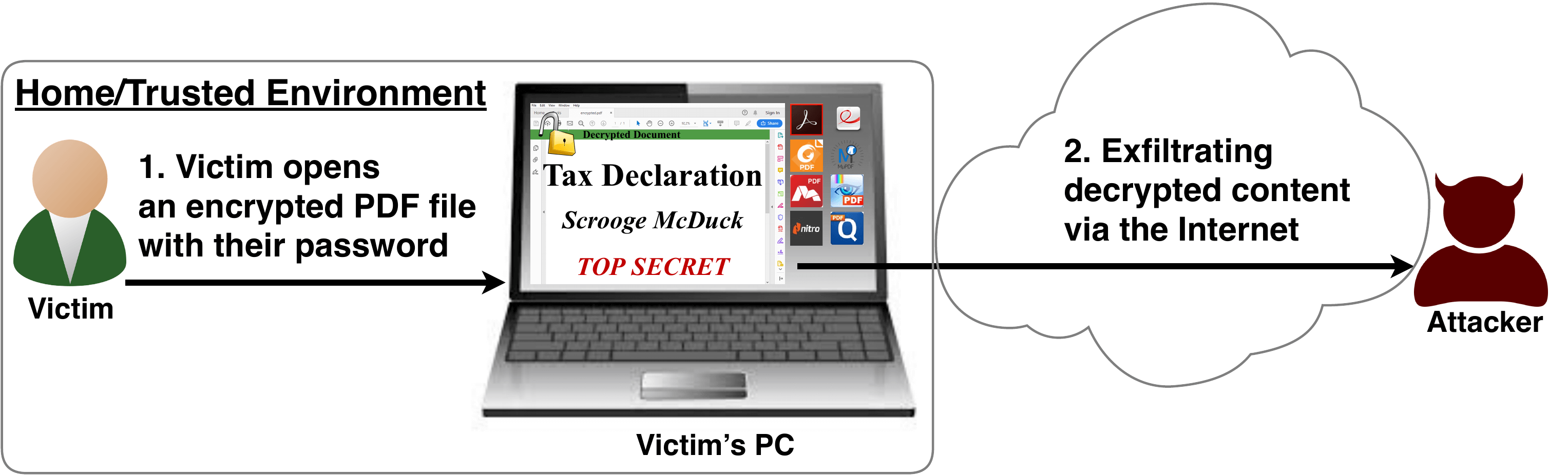
In testing, the researchers identified two standard compliant attacks that can break the confidentiality of encrypted PDF files. When testing 27 of the top PDF viewers, all were vulnerable to at least one of the attacks including software like Foxit Reader, Adobe Acrobat, Chrome and Firefox.
The researchers conclude that these issues must be fixed in future PDF specifications and will be presenting their findings at next month's ACM Conference on Computer and Communications Security.
Masthead credit: PDF by Jane Kelly
