In brief: AMD along with security researchers at the Dresden Technical University have disclosed a vulnerability in some AMD processors similar to the Meltdown and Spectre vulnerabilities for Intel CPUs that were first disclosed three years ago. AMD has already outlined multiple mitigation techniques to fight these vulnerabilities.
TU Dresden researchers Saidgani Musaev and Christof Fetzer notified AMD of the exploit in Zen+ and Zen 2 processors which they call "Transient Execution of Non-Canonical Accesses," directly comparing them to Spectre and Meltdown. AMD's security bulletin refers to the vulnerability with the name CVE-2020-12965.
AMD says the main risk is that this could cause processors to leak data they aren't supposed to. "When combined with specific software sequences, AMD CPUs may transiently execute non-canonical loads and store using only the lower 48 address bits potentially resulting in data leakage," it writes.
Musaev and Fetzer outlined the vulnerability in a research paper. AMD followed this up with its own review which it published on the bulletin. On the same page AMD also has a document outlining its mitigation techniques. "There are a variety of techniques software can use for managing processor speculation, each with different properties and trade-offs," AMD writes.
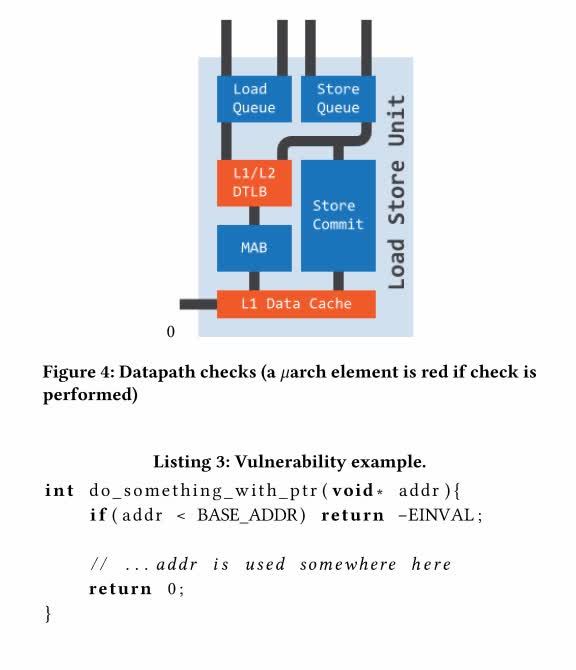
AMD recommends developers review their code running on the affected processors and insert an LFENCE, or use one of the solutions outlined in the document. AMD says its later and future processors have more security features to defend against these kinds of vulnerabilities like SMEP, SMAP, and IBC.
Meltdown and Spectre are hardware-level flaws for Intel CPUs that were disclosed in 2018 before being patched. If exploited, Meltdown could expose memory that should've been inaccessible, while Spectre could be used to execute malicious code. Patching the vulnerabilities initially caused hits to performance that were eventually mitigated.
In March of last year another vulnerability in Intel processors similarly based on a hardware flaw was found, called Load Value Injection (LVI). Like Meltdown, it can be exploited to leak data that should be protected.
Image credit Technical University of Dresden
