In context: Moveit, Progress Software's enterprise-level managed file transfer application has had a bad month. Only a few weeks ago, known Russian-linked threat actors and ransomware groups actively exploited two vulnerabilities, impacting private, corporate, and government customers.
Progress Software's latest issue tracked as CVE-2023-35708 is a SQL injection vulnerability that hackers can exploit to gain escalated privileges and unauthorized access to Moveit's database. In this case, attackers can submit a crafted payload to a Moveit Transfer application endpoint, providing them with unauthorized access to its database content.
The new security hole joins two similar, previously reported issues, CVE-2023-34362 and CVE-2023-35036. According to Progress Software's advisory, any versions released before 2021.0.8 (13.0.8), 2021.1.6 (13.1.6), 2022.0.6 (14.0.6), 2022.1.7 (14.1.7), 2023.0.3 (15.0.3) are at risk.
ICYMI: @CISAgov & @FBI are working closely to address risks posed by the #MOVEit vulnerability & urge orgs to apply mitigations detailed in our joint advisory: https://t.co/4sCMsJ4mj9. Any org observing unusual activity should immediately notify CISA or FBI so we can assist. pic.twitter.com/Exs4W4eeWs
– Jen Easterlyð¡ï¸Â (@CISAJen) June 16, 2023
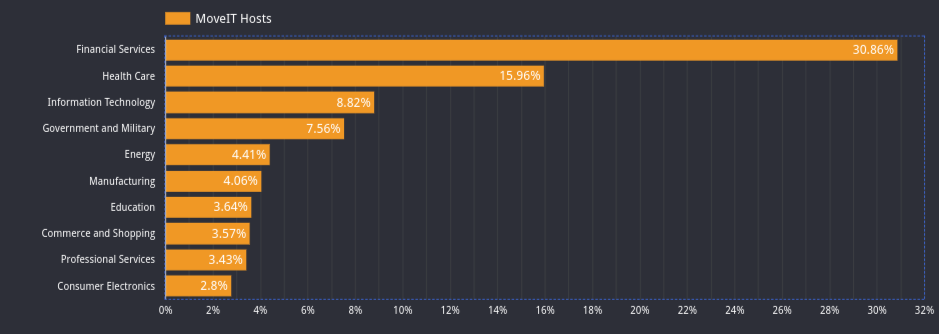
The number of current Moveit hosts and users is far from insignificant. According to a report from censys.io, more than 3,000 hosts are running the managed file transfer solution. More than 30 percent of the hosts running the software are in the financial services industry. More than 15 percent of customers are from the healthcare industry, almost 9 percent work in information technology, and over 7.5 percent are from government and military installations. Twenty-nine percent of the organizations observed in the report employ more than 10,000 individuals.
Progress Software recommends that users and hosts patch the product and mitigate the vulnerabilities immediately. The announcement provides several remediation paths for users and administrators to ensure they are no longer susceptible to the identified exploits. Users who have not applied the May 2023 patch should follow the mitigation steps in the Moveit Transfer Critical Vulnerability article. That page contains the latest patches, including the fix for the June 9 (CVE-2023-35036) vulnerability and the original vulnerability from May 31 (CVE-2023-34362). Once complete, proceed to the Immediate Mitigation Steps and apply the June 15 patch as outlined. You will then be up to date for the vulnerabilities announced on May 31, June 9, and June 15.
Researchers believe the Clop ransomware gang has been aware of the vulnerability since 2021. According to Cybersecurity and Infrastructure Security Agency Director Jen Easterly, the attacks have thus far mainly been opportunistic and had no significant impact on federal civilian agencies. Easterly also said, "...we are not aware of Clop actors threatening to extort or release any data stolen from U.S. government agencies."
Image credit: censys.io
