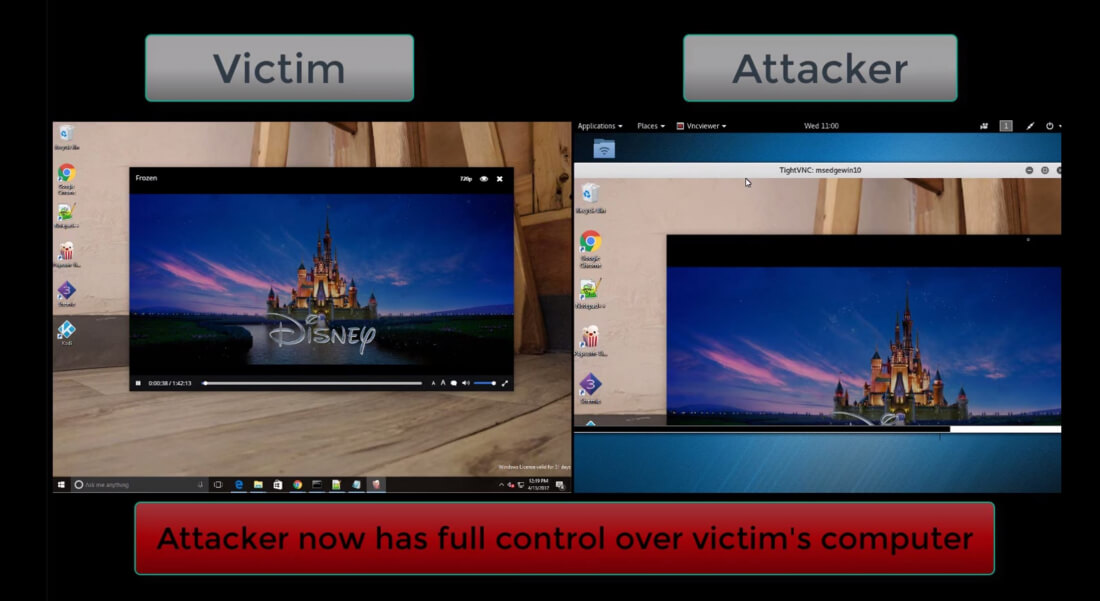
The number of ways that attackers can infect devices is incredible. One such method that has been around since at least 2003 involves inserting malicious code into the subtitle files used by media players for movies and TV shows. Now, vulnerabilities in modern players have seen a new form of the attack become popular.
Security research firm Checkpoint has discovered that popular media players including VLC, Kodi, Popcorn Time, and Stremio can all be exploited, allowing hackers to take control of "any type of device via vulnerabilities; whether it is a PC, smart TV, or a mobile device" using the subtitle files.
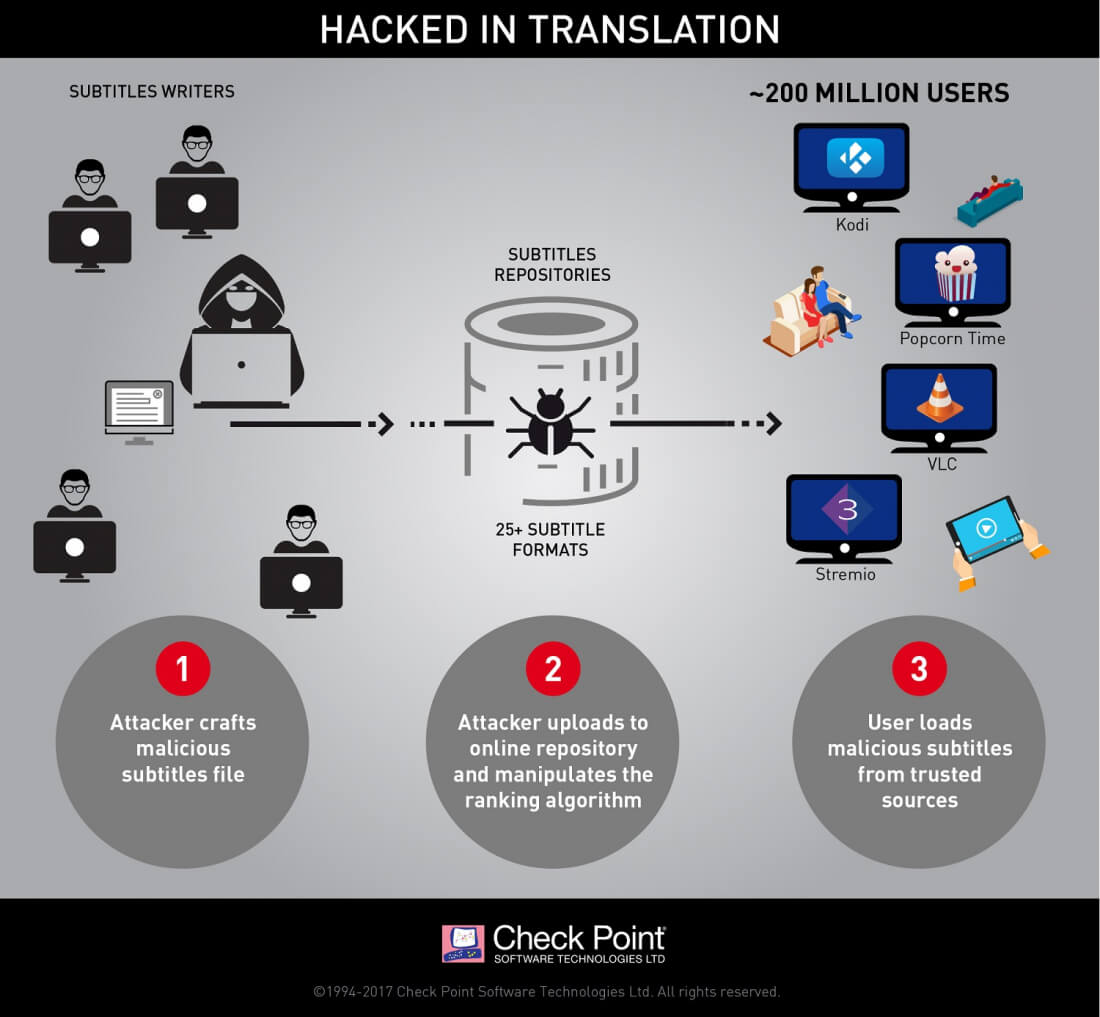
The attack relies on the insecure way various media players process subtitle files, and the wide variety of subtitle formats - the 25+ variations each come with unique features and capabilities, and players often mix multiple formats to ensure coverage and a better user experience.
Checkpoint writes that as soon as the players parse the infected files before displaying the subtitles on screen, the attackers can gain control of the device. Moreover, hackers can manipulate the ranking algorithms of online repositories, such as OpenSubtitles.org, ensuring that their malicious files are the ones automatically downloaded by the media players.
The four affected players have since released new versions of their software that include a fix for the vulnerability, so users should update them asap. But Checkpoint warns that similar security holes may exist in other streaming media software.
"To allow the developers more time to address the vulnerabilities, we've decided not to publish any further technical details at this point," the researchers said.
Check out the video below to see a demonstration of the attack in action.