Security researchers in the days following the CCleaner malware disclosure have made an alarming, albeit not entirely surprising, discovery.
According to Cisco Talos and Avast, this wasn't your run-of-the-mill hack but rather, a seemingly sophisticated attack that targeted nearly two dozen large technology and telecommunication companies in the US, Germany, Japan, Taiwan and the UK.
Analysis of the hackers' command-and-control server reveals that it was an APT (Advanced Persistent Threat) designed to deliver a second-stage payload to select users. Server logs indicates that at least 20 machines across eight organizations were indeed served the secondary payload although as Avast notes, the logs only cover a period of about four days.
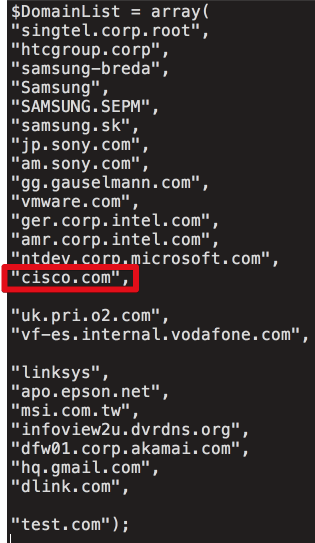
The actual number of systems that received the secondary payload is likely in the order of hundreds, Avast indicates.
High-profile targets included Intel, Microsoft, Sony, Akami, Epson, MSI, Cisco, Linksys, Samsung and HTC, among others. According to Talos, the specific targets indicate a "very focused" attacker seeking valuable intellectual property.
It was disclosed earlier this week that a signed version of CCleaner, a staple in the toolbox of many PC repair technicians and IT professionals, had been leveraged to delivery malware to unsuspecting victims. At the time, it seemed no different than any other malware attack but of course, we now know it was a watering hole attack.
Talos also recommends that, if possible, impacted users should restore from a backup or reimage systems to ensure the threat is removed.
