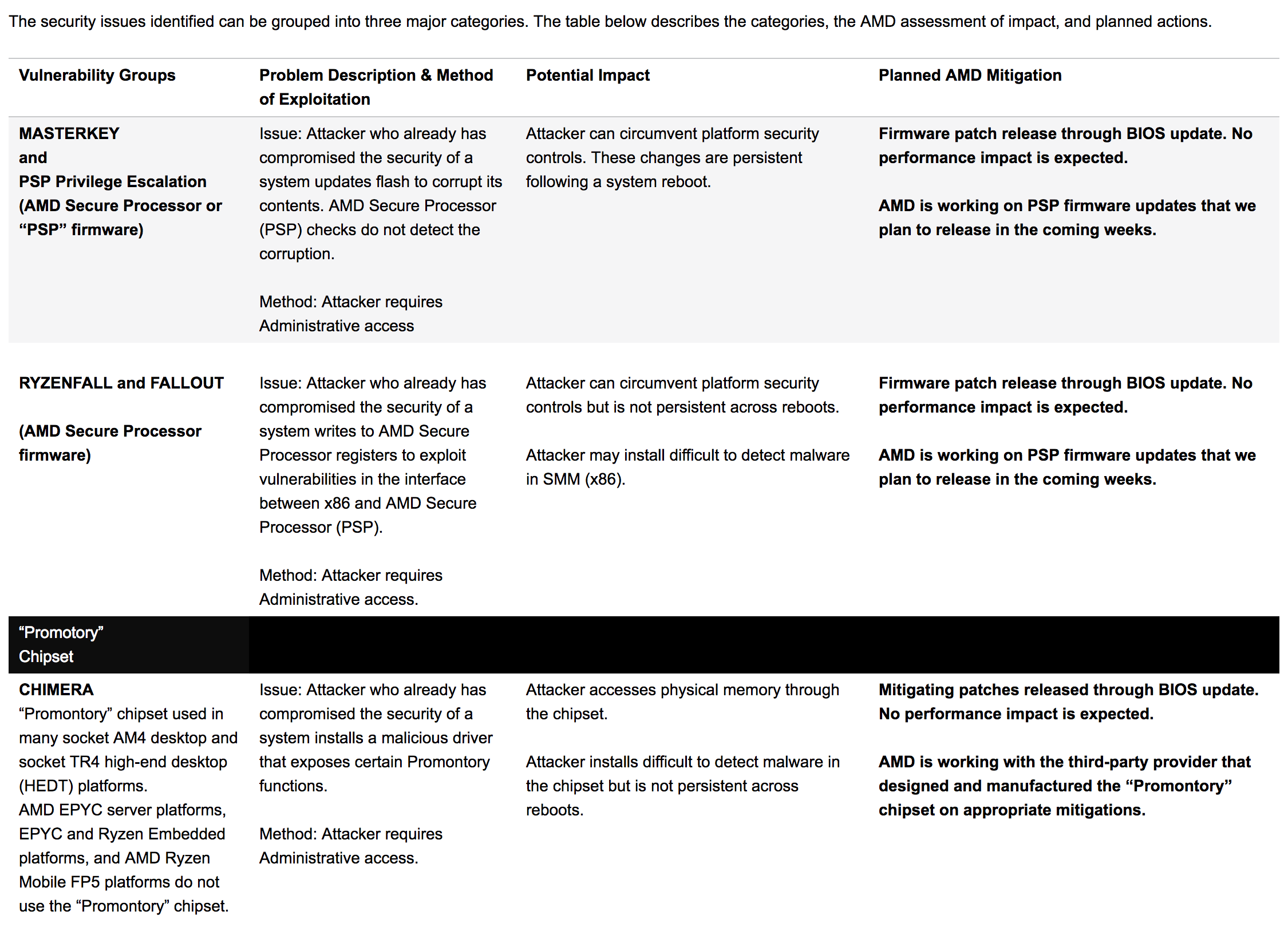
AMD on Tuesday issued its first public update regarding security vulnerabilities involving select products publicly disclosed by Israeli-based security firm CTS-Labs on March 13. In today's update, AMD said it has been working to rapidly assess the claims and develop mitigation plans where needed.
If you recall, AMD was given less than 24 hours notice prior to CTS going public with its alleged findings. The short turnaround sparked widespread criticism regarding potential motives behind the disclosure as standard practice in the security community is to give 90 days notice before going public.
Mark Papermaster, AMD's senior vice president and chief technology officer, seemingly downplayed the matter, saying the security issues are not related to its Zen CPU architecture or the Google Project Zero exploits announced in early January. Instead, they are linked to the firmware managing the embedded security control processor (AMD Secure Processor) and the chipset used in some AM4 and socket TR4 desktop platforms.
He also pointed out that all of the issues raised by CTS require administrative access to a system, "a type of access that effectively grants the user unrestricted access to the system and the right to delete, create or modify any of the folders or files on the computer, as well as change any settings."
Papermaster says that any attacker gaining unauthorized admin access "would have a wide range of attacks at their disposal well beyond the exploits identified in this research." What's more, he notes that all modern operating systems and enterprise-quality hypervisors have "many effective security controls, such as Microsoft Windows Credential Guard in the Windows environment, in place to prevent unauthorized administrative access that would need to be overcome in order to affect these security issues."
Papermaster pointed to a "useful clarification" of the difficulties associated with successfully exploiting the issues in this post from Trail of Bits.
The chipmaker said it has completed its assessment and is already working on developing and deploying mitigations. Patches through BIOS updates are expected in the coming weeks and shouldn't have an impact on performance, we're told.
