According to a report by German researchers, some 99.7% of Android devices in circulation are vulnerable to an attack that could compromise sensitive data transmitted over a wireless network connection. The hole reportedly stems from a flaw in Google's ClientLogin authentication protocol, which verifies communication between Android devices and applications.
To use ClientLogin, an app requests an authentication token (authToken) from the Google service by passing an account name and password over an HTTPS connection. The returned authToken can be used for any subsequent request to the service API and in addition to remaining valid for up to two weeks, it's not bound to any session or device-specific information.
Those attributes wouldn't be an issue if attackers couldn't obtain an authToken, but that isn't the case. The article notes that many applications can send such data over an unencrypted HTTP connection, making it easy for unsavory types to obtain the authToken with software utilities such as Wireshark, which can then be used to access your information.
"For instance, the adversary can gain full access to the calendar, contacts information, or private web albums of the respective Google user. This means that the adversary can view, modify or delete any contacts, calendar events, or private pictures. This is not limited to items currently being synced but affects all items of that user," the researchers explained.
Wireshark showing ClientLogin authToken in data API request to Picasa Web Albums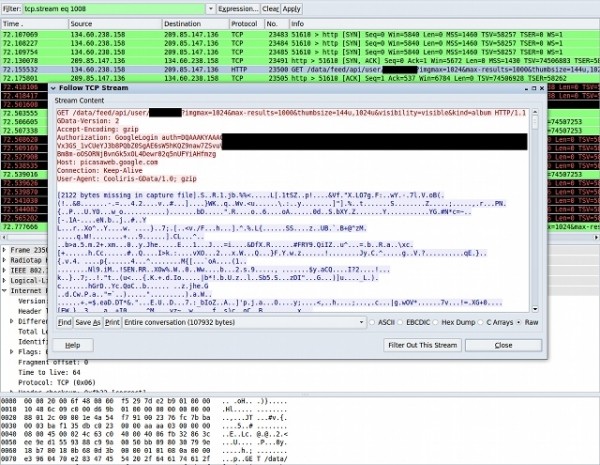
Besides stealing the compromised user's information, a hacker could also target the victim's contacts. "An adversary could perform subtle changes without the user noticing. For example, an adversary could change the stored email address of the victim's boss or business partners hoping to receive sensitive or confidential material pertaining to their business."
Because authTokens last for up to two weeks, the report noted that an attacker could collect them on a large scale with an insecure wireless access point and use them later from an entirely different location. As such, the researchers are urging Google to limit the lifetime of authTokens in addition to rejecting ClientLogin-based requests from insecure connections.
The vulnerability is present in all Android versions prior to 2.3.4 (Gingerbread), which is only available for a handful of Android devices. If you can't update to 2.3.4, the researchers recommend avoiding public Wi-Fi networks or at the very least disabling automatic synchronization and letting your device forget an open network that you previously connected to.
https://www.techspot.com/news/43838-997-of-android-phones-leak-user-account-credentials.html