PSA: Hackers can steal your username and password for a website using an embedded iframe. It's a weakness for all password managers, and most have addressed the flaw in various ways, including issuing warnings when users are on a login page with an iframe or not trusting subdomains. Bitwarden is the sole exception, having determined in 2018 that the threat was not significant enough to address.

Update (March 17): A Bitwarden spokesperson contacted TechSpot to inform us that it is taking measures to mitigate the autofill vulnerability. The company did not explain why it waited five years to address the issue but did say it merged the fix request on GitHub and that the patch would be ready next week.
The company said it would make two specific changes.
First, if a user enables the autofill on page load setting, Bitwarden will only fill in iframes from trusted domains, such as the same domain as the website or a specific URL the user has proactively added to their item. Second, if the user tries to fill in an untrusted iframe using manual autofill, Bitwarden displays an alert to the URI/URL they are trying to autofill and allows them to either cancel or proceed.
So essentially, Bitwarden will implement process breaks and warnings like other password managers.
The original story follows below:
In its support pages regarding "Auto-fill," Bitwarden advises users to turn off their browsers' password autofill functions because they interfere with its password management solution. It also mentions it is a good idea because "experts generally agree that built-in [browser] password managers are more vulnerable than dedicated solutions like Bitwarden," which is generally true.
Unfortunately, its password filler might not be much better than your browser's. Security researchers at Flashpoint discovered that Bitwarden's autofill extension handles websites with embedded iframes in an unsafe manner. A basic understanding of iframes is needed to understand this vulnerability.
Website developers use the inline frame element, or iframe, to embed part of another webpage into their site. For example, TechSpot uses iframes to embed YouTube videos into its articles. It can also be used to embed web forms. Generally, iframes are safe to use as long as the embedded material from the external website has not been compromised, and this is where managers have a problem.
Password extensions autofill credentials on any webpage users have saved their credentials by design. However, the extension will perform this function in an iframe without performing a "Same-origin Policy" check. So if a page has a malicious iframe from a different domain, the manager will unknowingly hand over your credentials for them to be sent to a hacker's server. They can even fill out the login form pre-emptively without user interaction. In Bitwarden's this is a setting called "Auto-fill on page load."
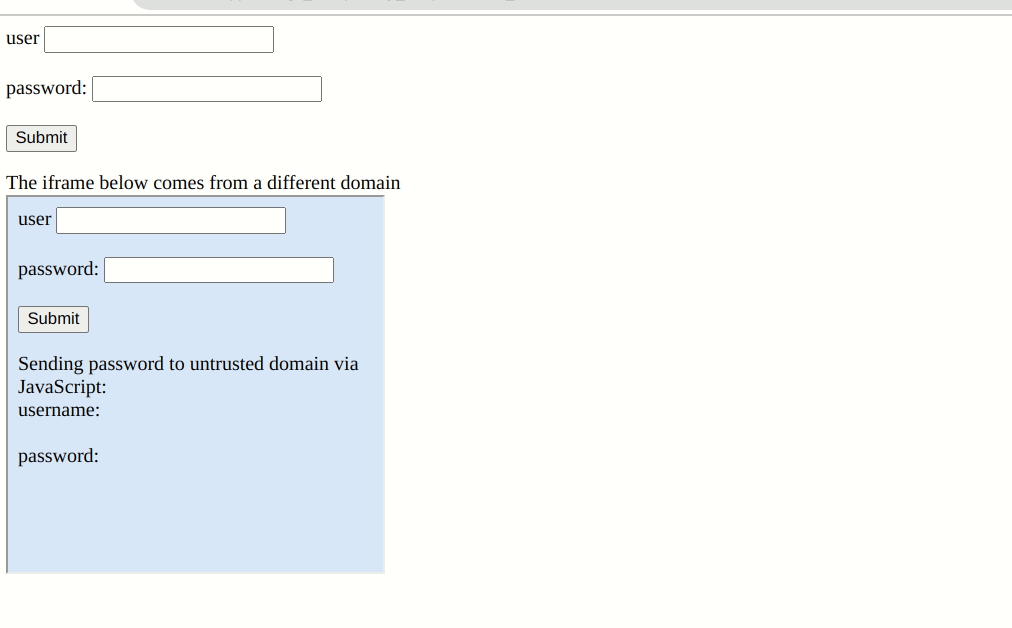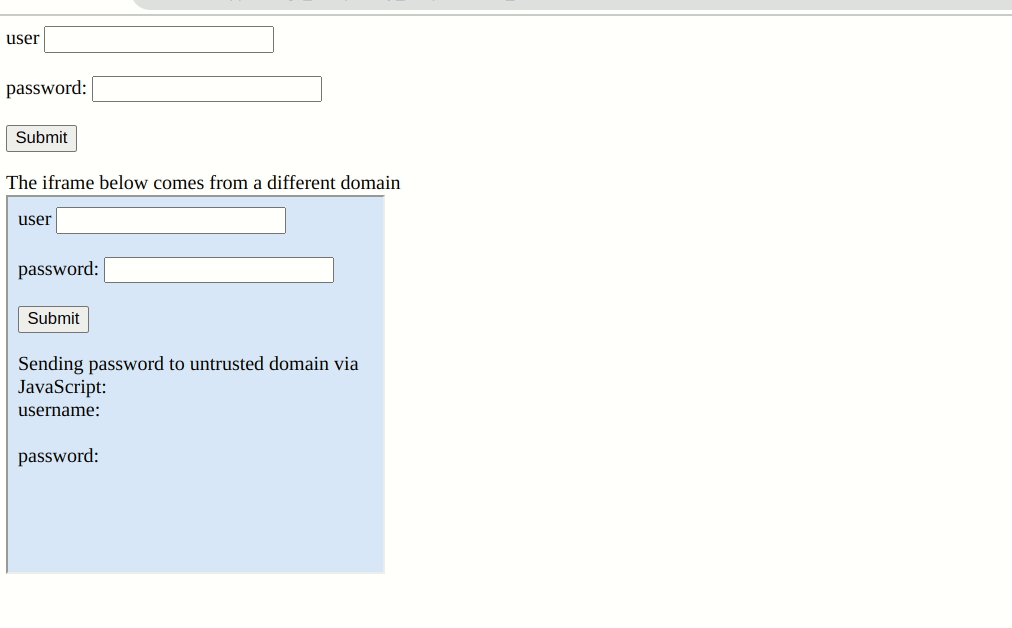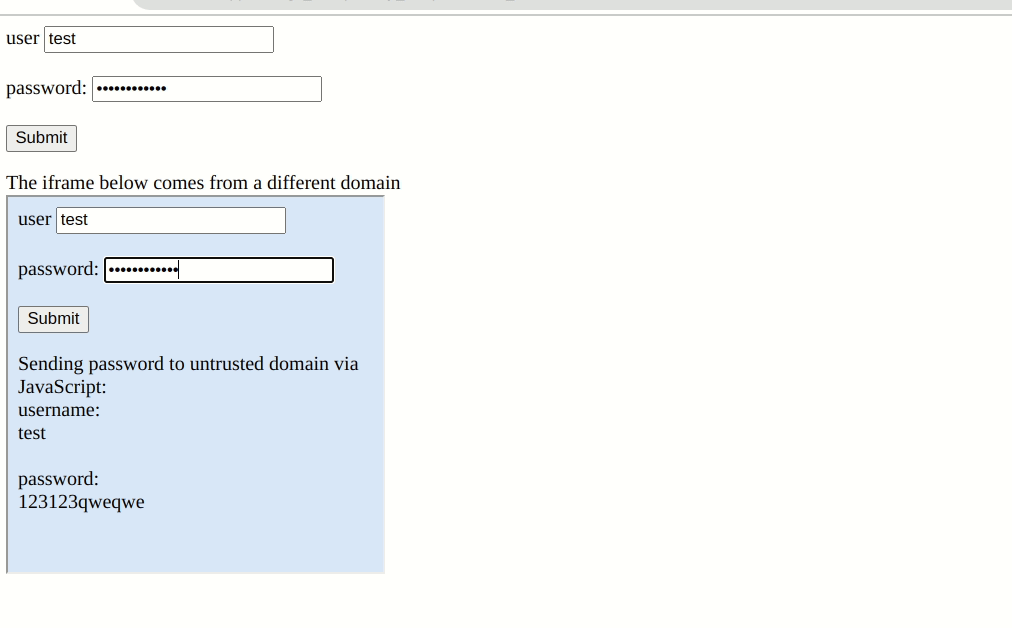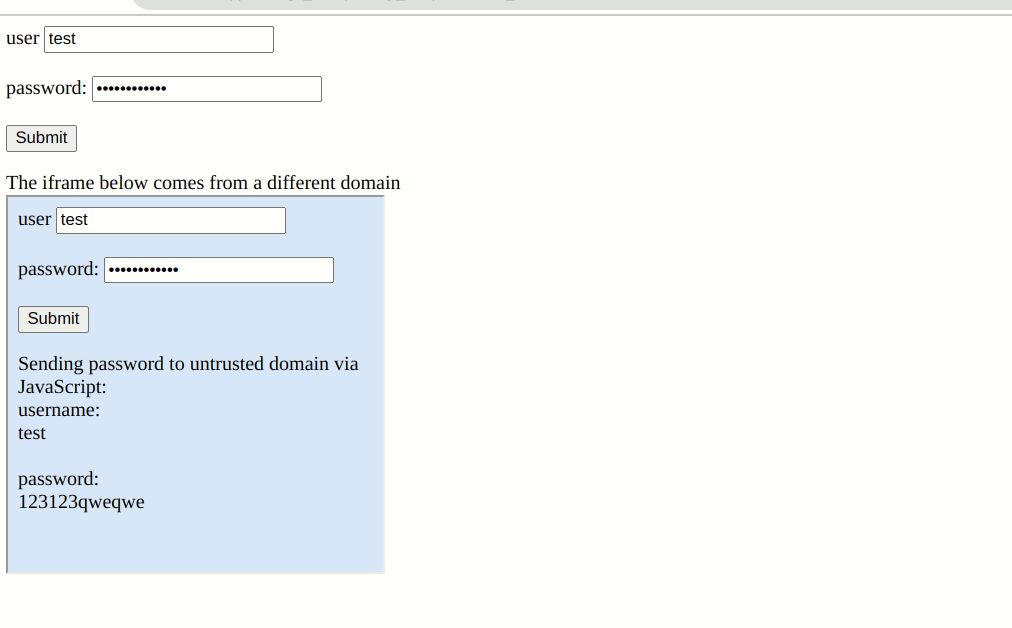
Proof of concept showing Bitwarden autofilling the legitimate and "malicious" iframe fields simultaneously.
Most password managers have checks in place to at least warn users of potential dangers. However, Bitwarden does not prevent or warn that an iframe from a different domain is potentially stealing credentials. It assumes that all iframes on a login page are safe. It said as much in a 2018 security report, but more on that later.
Of course, this could only happen if the trusted website is already compromised, right? According to Flashpoint, that's not necessarily true.
Obviously, if hackers have gained enough of a foothold to embed an iframe on a legitimate website, users have bigger problems than this weakness on their hands. There is little that any password management extension could do in that scenario. However, some legitimate websites use forms from another domain, embedding them with an iframe. If hackers can compromise the secondary source, they have a proxy for stealing information from the trusted website.
Flashpoint admits this is a rare scenario and confirmed that with a spot-check of several sites using iframes on their login pages. However, there is another problem. Bitwarden's default URI (Uniform Resource Identifier) matching is set to "Base domain." So the extension will provide password autofill as long as the top-level and second-level domains match.
The problem is that several hosting services allow users to host "arbitrary content" under a subdomain making it relatively easy to spoof a login page.
Flashpoint uses iCloud as an example of a login page that uses an external iframe from apple.com to allow users to authenticate with their Apple credentials.
"As an example, should a company have a login page at https://logins.company.tld and allow users to serve content under https://[clientname].company.tld, these users are able to steal credentials from the Bitwarden extensions," said Flashpoint. "In our research, we confirmed that a couple of major websites provide this exact environment. If a user with a Bitwarden browser extension visits a specially crafted page hosted in these web services, an attacker is able to steal the credentials stored for the respective domain."
Oddly, when Flashpoint contacted Bitwarden about this weakness to coordinate disclosure, the company pointed out that it has known about it since 2018.
"Since Bitwarden does not check each iframe's URL, it is possible for a website to have a malicious iframe embedded, which Bitwarden will autofill with the 'top-level' website credentials," the company's 2018 Security Assessment Report reads. "Unfortunately, there are legitimate cases where websites will include iframe login forms from a separate domain than their 'parent' website's domain. No action is planned at this time."
In other words, Bitwarden is aware of the problem but deems the risk acceptable enough not to do anything about it, even if it were as simple as having the extension issue a warning when there is an iframe on a page. Flashpoint found this inexplicable since all of Bitwarden's competitors have some form of mitigation for this exploit.
The researchers created a proof of concept using the flaw as an attack vector and a "working exploit" they implemented privately on a "prominent hosting environment." They hope that developers at Bitwarden will change their minds about the issue since nobody had created such exploits in 2018 when the company initially assessed the weakness. Until Bitwarden addresses the vulnerability, you can do a couple of things to mitigate it without switching password managers.
First, turn off the extension's "Auto-fill on page load" setting. You will have to trigger the autofill feature manually all the time. However, it gives you some breathing room to inspect the login page without immediately handing your credentials over to an iframe. That is actually good advice for any password manager extension featuring preemptive autofill.
Second, use that pause to be sure you are on a trusted domain and that the page is what it seems. Look at the URL to ensure you are on the correct domain or subdomain and that nothing appears suspicious. For instance, something like "login.wellsfargo.com" is probably legit, whereas "credx257.wellsfargo.com" likely isn't.
These steps will still not protect you from sites that use compromised external web forms, but Flashpoint noted that those scenarios are rare. It's no reason to give up using a password manager, even Bitwarden. Managers are well-suited to help you keep your credentials straight. It's always better to have tons of solid hard-to-remember passwords unique to every website than to reuse weak ones.