What just happened? Earlier this week, Cloudflare engineers identified one of the largest distributed denial-of-service (DDOS) attacks ever attempted. The attack, made against an unidentified cryptocurrency platform, was identified and mitigated in under 20 seconds. The individuals behind the act flooded the network with more than 15 million requests.
In addition to the attack's size, the use of HTTPS rather than typical HTTP requests further complicated the issue—the secure protocol results in more resource overhead due to the compute-intensive nature of the secure HTTPS request. According to Cloudflare, the botnet responsible for carrying out the attack represented 6,000 bots from 112 countries around the world.

The attack is believed to have leveraged servers from hosting providers running vulnerable Java-based applications. Those servers were likely unpatched or not updated and susceptible to CVE-2022-21449, Psychic Signatures in Java. The vulnerability allows attackers to use the elliptic curve digital signature algorithm (ECDSA) to forge SSL certificates and other authentication-based information in order to obtain unwanted access.
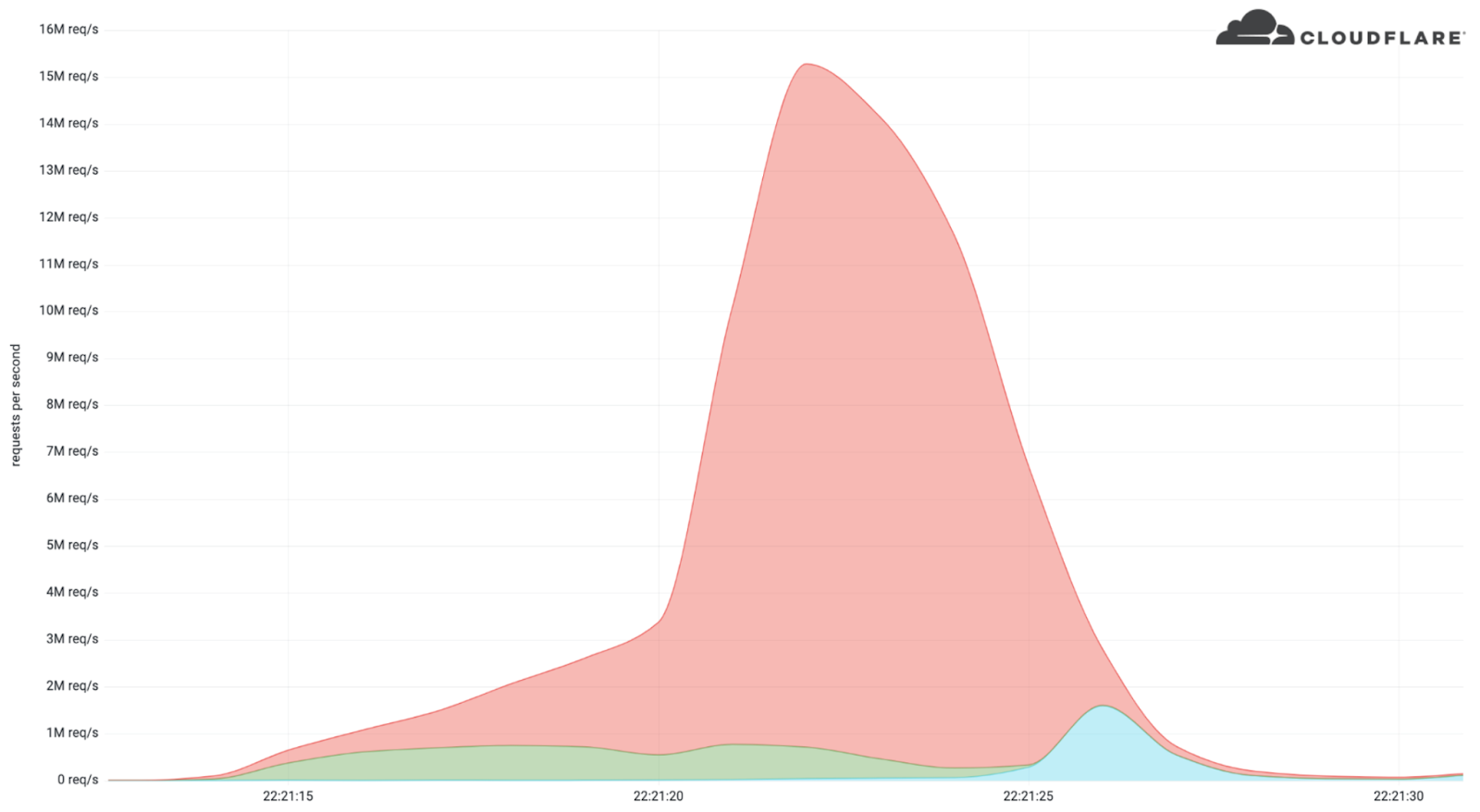
The sharp spike in Cloudflare's traffic analytics shows just how quickly the attack was able to ramp up. At 22:21:15 the platform recorded between 500,000 and 1 million requests. Within five seconds, that number grew to almost 3 million requests. At this point the attack's intensity escalated, generating approximately 15.3 million requests within the next five seconds. Several seconds later, Cloudflare was able to mitigate the attack, bringing traffic patterns back to expected levels.
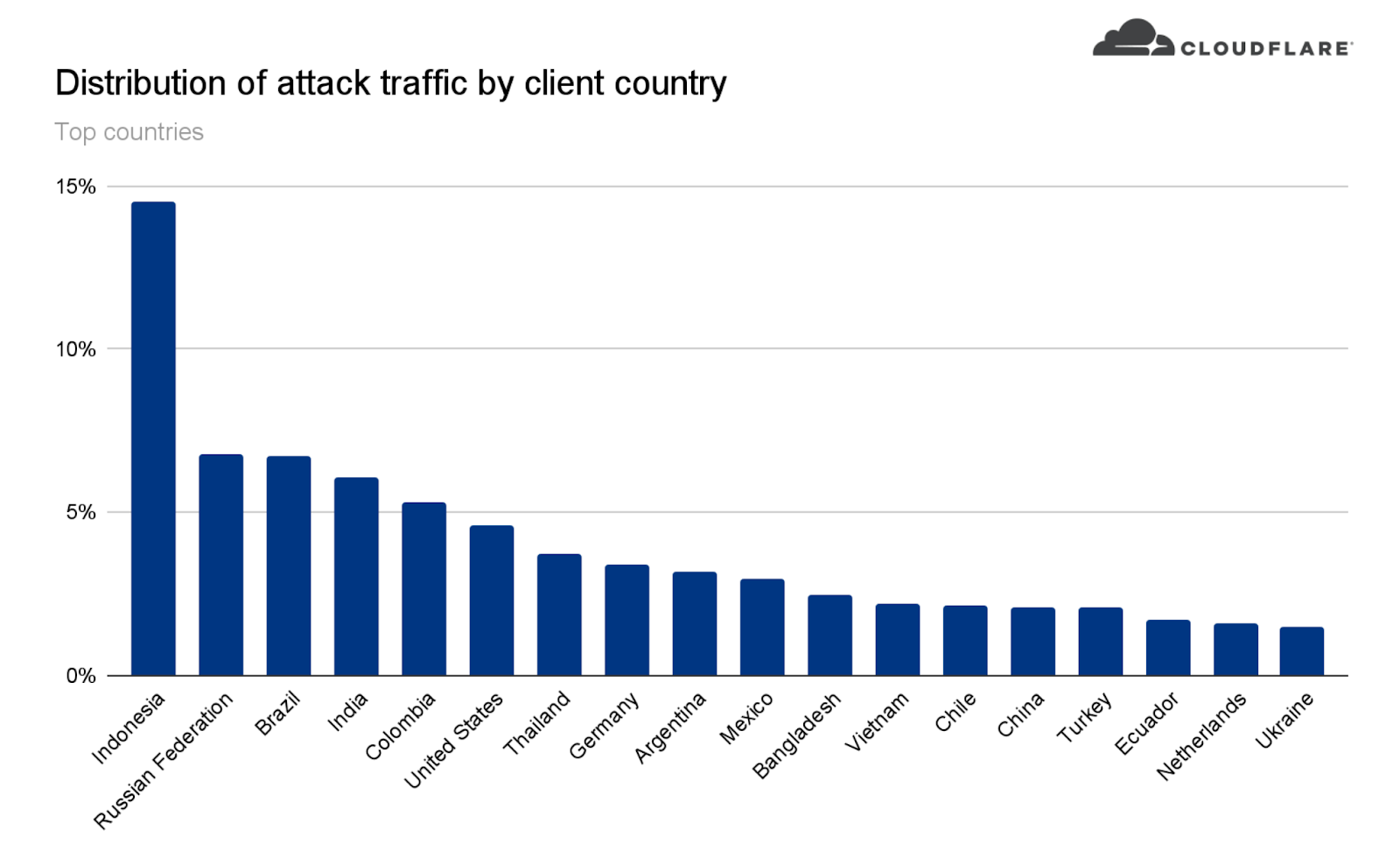
According to Cloudflare's data, almost 15% of the attacks originated in Indonesia. The Russian Federation, Brazil, India, Columbia, and United States each accounted for approximately 5% of the origination points. Cloudflare engineers and security experts concluded that the attacks originated from more than 1,300 different networks across the entire 112 countries identified. They were also surprised to find that unlike other attacks, many of these attacks originated from data centers rather than typical ISP-based residential networks.
Oracle has since released a critical patch update advisory to help users mitigate any potential vulnerability. Administrators of potentially vulnerable systems should review this information to ensure any Java-related risks are minimized.
The size of the attack, as well as the resources applied and power required to execute the HTTPS-based attack, are clear signs that hackers are continuing to strengthen their weapons in what seems to be a never-ending arms race. Staying up-to-date on the latest security patches and recommendations can help to minimize the possibility of falling victim to these and similar attacks in the future.
Image credit: Traffic pattern and location breakdown from Cloudflare
https://www.techspot.com/news/94416-cloudflare-mitigated-one-most-powerful-ddos-attacks-ever.html