In brief: Security researchers have uncovered yet another malware campaign designed to fool people who are looking to cheat in online games. Players who want to gain an unfair advantage over their opponents in Valorant may be greeted by a different tool that’s designed to steal their sensitive information.

Cheaters in popular multiplayer games are nothing new, and the pandemic saw their numbers rise considerably as more people have turned to gaming as a source of entertainment. Companies have been trying to fix this growing problem with improved anti-cheat technologies, but most efforts have been undermined by source code leaks as well as an army of motivated cheat developers who are quick to adapt to any new developments in this space.
Valorant’s anti-cheat software has been a big source of controversy for using kernel level drivers to thwart cheaters, but it’s also led to fewer of them for that particular title. That said, some people are desperate enough to scour the web for anything that might give them an unfair edge over other players, so malicious actors are feeding the demand with malware campaigns.
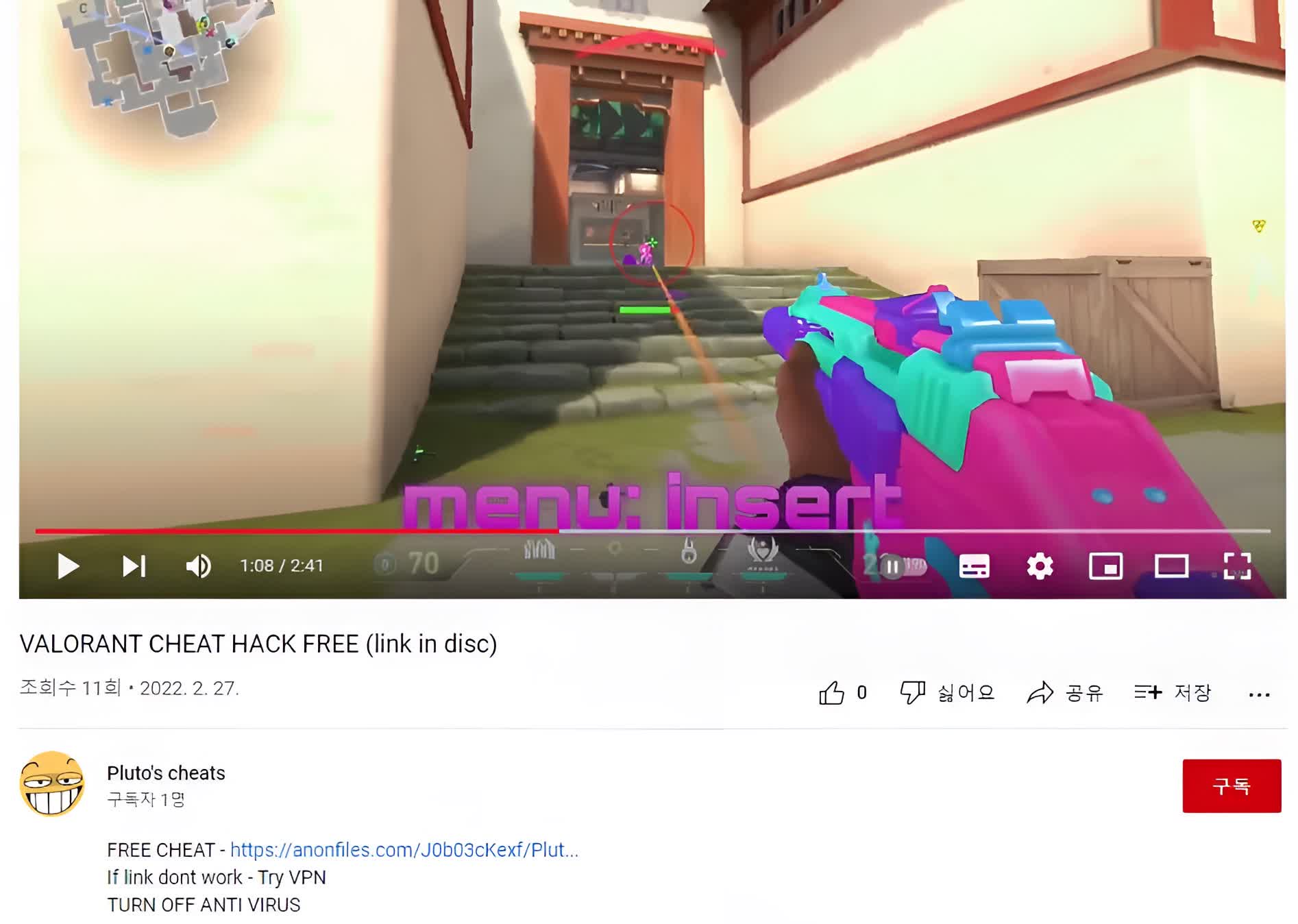
Video promoting fake cheat software
According to Korean security researchers at ASEC, some Valorant players are now being deceived into downloading and running software that is promoted on YouTube as a game hack, but in reality is just a delivery system for a powerful information stealer called RedLine. The malicious actors are able to do this quite often as they can easily bypass content submission reviews and create a new account whenever one is reported and blocked.
As with all cheat software, people who download the supposed Valorant cheats are asked to disable their anti-virus software and use elevated privileges in order to allow smooth installation and operation of those cheats. However, this is also what malware needs to install itself silently on a system without the need for complicated exploits.
RedLine is one of the most widely deployed info stealers out there, and once installed it will export a wide range of sensitive data including passwords, credit card information, browser cookies, bookmarks, browser history and cryptocurrency wallets as well as account credentials for things like Steam, Discord, and more. The stolen information gets packaged as a zip file and shuttled to a Discord server.
Social engineering campaigns for malware such as this are becoming increasingly common. Last year, cheating software for Call of Duty: Warzone was found to contain malware known as “dropper,” which can take control of a player’s system and install additional malware. It should go without saying that you shouldn’t ruin other players’ fun in an online game, but these types of malware campaigns serve as a reminder that cheating is not without risk, regardless of what the cheat makers will tell you about their offerings.
https://www.techspot.com/news/93762-fake-valorant-cheats-promoted-youtube-carry-redline-malware.html