Renowned developer and hacker Samy Kamkar has demonstrated a technique that allows virtually anyone to hijack a password-protected computer – even if it’s locked – using a $5 Raspberry Pi Zero and some custom software.
PoisonTrap, as the tricky device is called, emulates an Ethernet-over-USB device once plugged into a computer, thus tricking the machine into thinking a wired Internet connection is suddenly available. The computer then sends a DHCP request asking for an IP address, which PoisonTrap gladly provides.
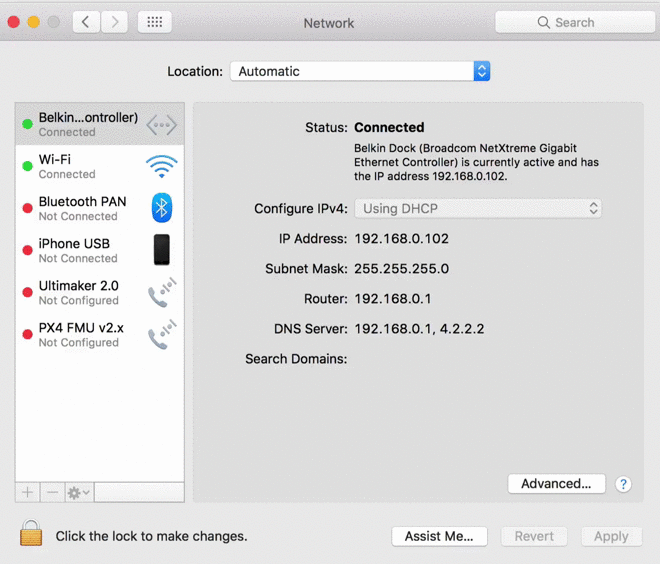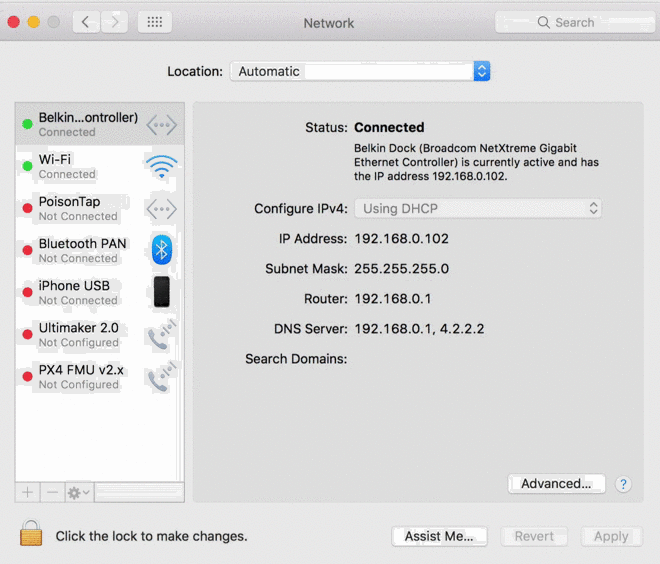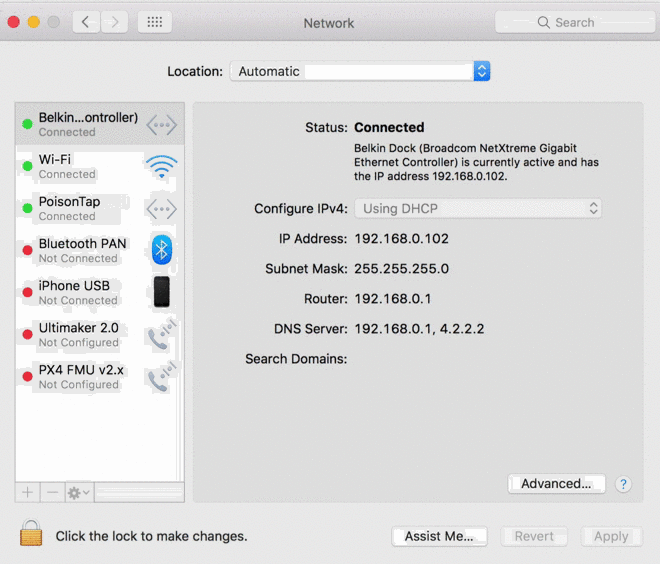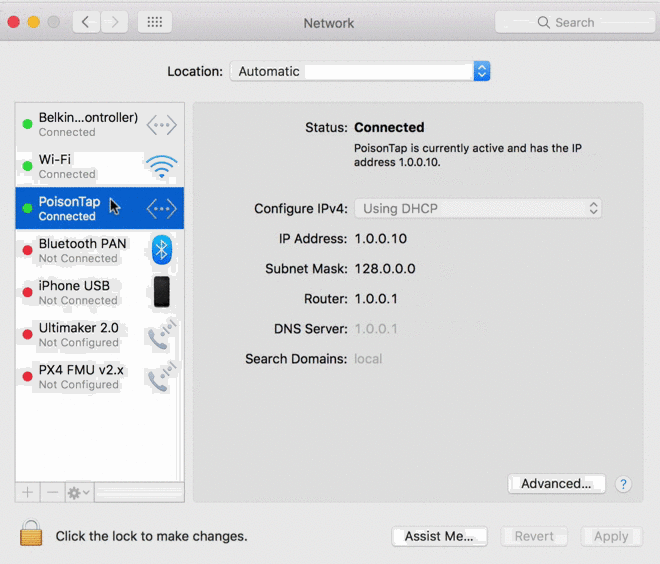
As Kamkar explains, this would normally behave as a secondary network interface but PoisonTrap crafts the DHCP response to make it appear as if almost all IP addresses on the Internet are part of PoisonTrap’s LAN. As such, the computer starts sending Internet traffic out to the hardware device instead of the actual Internet and as Kamkar highlights in the clip above, it’s all downhill from there.
The attack requires physical access to a machine, somewhat limiting the risk until you realize just how often you wander off away from your computer while at home, in the office or even at school. Fortunately, there are some safeguards you can take to minimize the threat such as using sites that are protected by HTTPS encryption whenever possible.
Or, you could simply do as Kamkar recommends and add cement to all of your USB ports.
https://www.techspot.com/news/67090-hacker-samy-kamkar-demonstrates-how-break-password-locked.html