This week, security researchers discovered a major bug called Heartbleed that affects almost two-thirds of the Internet, potentially exposing millions of passwords, credit card numbers, and other valuable information. Many popular websites like Yahoo, OkCupid, Github, and more were vulnerable.
The bad news is that you can't do much about it because it's up to each company to update OpenSSL on their servers and obtain new certificates to deal with the bug. Only after that you are supposed to update your passwords.
To ease some of the pain and guesswork, LastPass has added a new feature to ther security check tool, which highlights websites affected by the bug and whether they've taken the necessary steps to mitigate the risk, suggesting that you go ahead and update your passwords or wait.
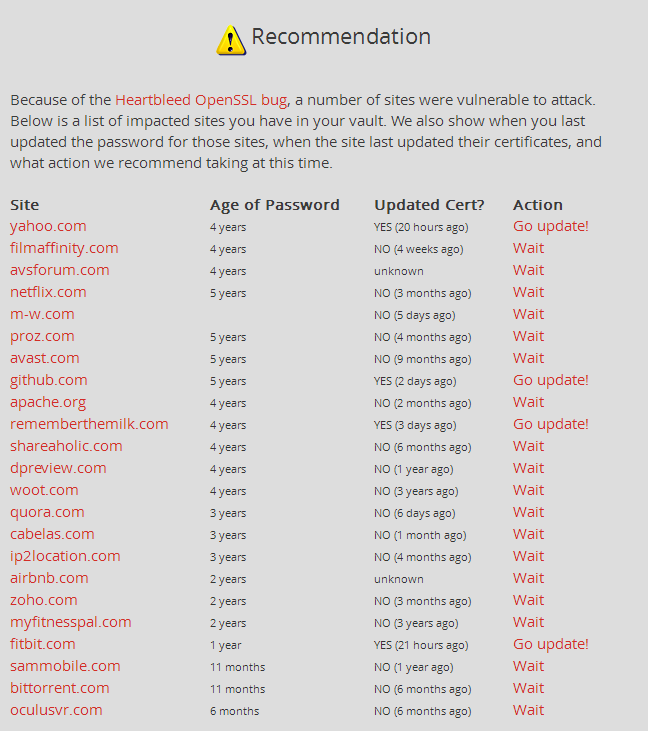
"To help our users take action and protect themselves in the wake of Heartbleed, we've added a feature to our Security Check tool", LastPass said in a blog post yesterday.
To run the security check, existing users need to click on the LastPass extension, and go to Tools->Security Check. A new browser window or tab will open asking you to take the LastPass security challenge. Just click the Start the challenge button, and a list of impacted sites will show up.
If you aren't a LastPass user it's still possible to access their Heartbleed Checker tool and enter the URL of any website individually to check whether it is vulnerable to the bug, and if the site has issued a patch. To download the latest version of LastPass just click here.
https://www.techspot.com/news/56341-lastpass-now-includes-recommendations-for-heartbleed.html