Government agencies and high profile institutions from at least 20 countries may have fallen victim to a sophisticated new cyber-attack, according to security firm Kaspersky and Hungary's Laboratory of Cryptography and System Security (CrySyS). Dubbed MiniDuke, the attack in question takes advantage of a recently discovered PDF exploit in Adobe Reader and involves some old school low level code written in assembler.
To compromise victims the attackers used social engineering techniques, which involved sending malicious PDF documents to their targets. These documents were apparently very authentic looking and referred to highly relevant topics including human rights, Ukraine's foreign policy, and NATO membership plans. Once opened this would trigger a very small 20kb downloader unique to each targeted system that will load on subsequent boots and use a set of mathematical calculations to encrypt communications based on the system’s fingerprint.
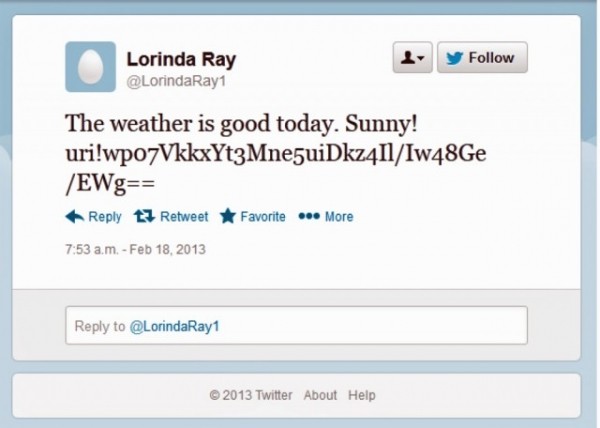
MiniDuke is flexible enough that the malware’s Command and Control (C2) operators can constantly change how their backdoors retrieve further commands as needed and stay hidden. Methods include using high-availability services like Twitter and Google to deliver encrypted URLs for the backdoors. These URLs provide access to the C2s, which then provide commands and encrypted transfers of additional backdoors onto the system hidden inside GIF files using a method known as steganography to gain control of a machine.
CrySys identified servers in Panama, France, Switzerland, Germany and the U.S. as the source of the code. That said, there are no clear indications as to who was behind the attacks. It’s believed the hackers are attempting to steal political intelligence and were last active as recently as February 20.
Government computers in the Czech Republic, Ireland, Portugal and Romania along with think tanks, research institutes and healthcare providers in the United States were mentioned among the targets.
"This is a very unusual cyber attack," said Eugene Kaspersky, founder and chief executive of Kaspersky Lab. "I remember this style of malicious programming from the end of the 1990s and the beginning of the 2000s. I wonder if these types of malware writers, who have been in hibernation for more than a decade, have suddenly awoken and joined the sophisticated group of threat actors active in the cyber world."