Why it matters: Cybersecurity firm Proofpoint recently released vulnerability findings related to two popular enterprise cloud applications, SharePoint Online and OneDrive. The firm's findings explained how bad actors can leverage basic functionality in the applications to encrypt and hold a user's files and data for ransom. The vulnerability presents hackers with another avenue to attack cloud-based data and infrastructure.
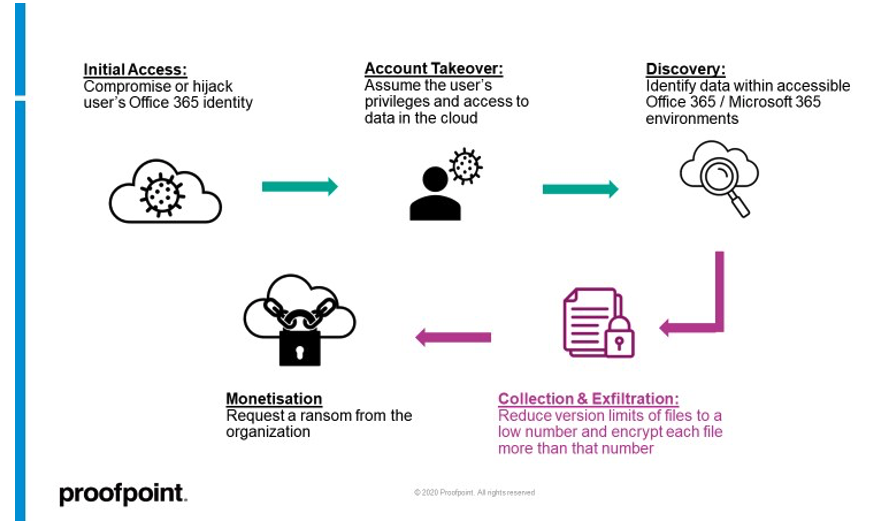
The exploit relies on a four-step attack chain that begins with a specific user's identity being compromised. The malicious actor uses the individual's credentials to access a user's SharePoint or OneDrive accounts, change versioning settings, and then encrypts the files multiple times, leaving no unencrypted version of the compromised files. Once encrypted, the files can only be accessed using the right decryption keys.
User accounts can be compromised by brute force or phishing attacks, improper authorization via third party OAuth apps, or hijacked user sessions. Once compromised, any action to exploit the vulnerability can be scripted to run automatically via application program interfaces (APIs), Windows PowerShell, or through the command line interface (CLI).
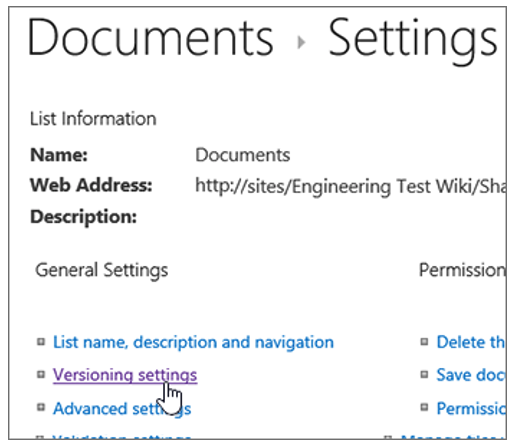
Versioning is a function in SharePoint and OneDrive that creates a historic record for each file, logging any document changes and the user(s) who made those changes. Users with appropriate permissions can then view, delete, or even restore earlier versions of the document. The number of versions kept is determined by the versioning settings in the application. Version settings do not require administrator-level permissions and can be accessed by any site owner or user with proper permissions.
Changing the number of document versions retained is key to this exploit. The malicious actor configures the versioning settings to keep the desired number of versions per file. The files are then encrypted more times than the number of versions retained, leaving no recoverable backed up versions.
For example, setting the document versioning to one and then encrypting the file twice would result in the master copy and single retained version both being encrypted. At this point the ransomed files must be decrypted using the corresponding decryption key or remain unrecovered.
Encryption is not the only way the versioning setting can be exploited. The hacker may opt to keep a copy of the original document and then proceed to make a number of changes to the document that exceeds the number of versions being kept. For example, if the versioning is set to retain the last 200 copies, the actor can make 201 changes. This would ensure that the master copy in SharePoint or OneDrive and all retained backups have been altered while holding the original copy for ransom.
Proofpoint's blog provides several recommendations to help protect you and your organization from this type of attack. These recommendations, some of which rely on Proofpoint's suite of cybersecurity products, focus on early detection of high-risk configurations and behaviors, enhanced access management, and ensuring sufficient backup and recovery policies are in place.
Image credit: Ransomware attack process from Proofpoint