
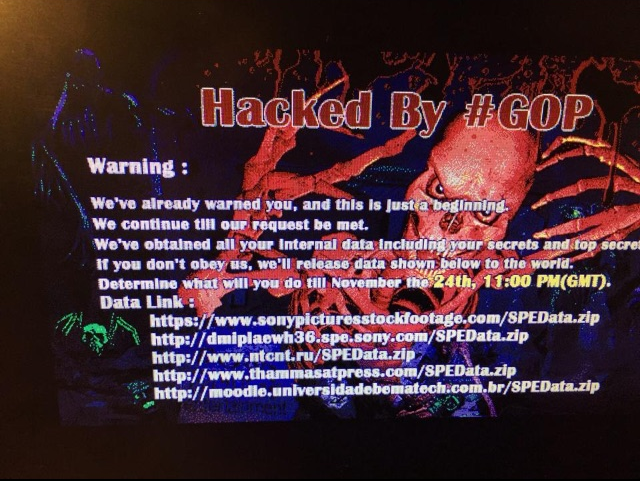
Sony Pictures is still reeling from the hack on its computer network in which a group calling itself the Guardians of Peace made off with loads of personal data on employees and celebrities. The sensitive data has since shown up on a number of outlets across the web and in an effort to slow the leaks, Sony has reportedly resorted to hacker methods of its own.
Two people familiar with the matter claim Sony is using hundreds of computers in Asia to launch distributed denial of service (DDoS) attacks on sites hosting the stolen data. Specifically, they’re using Amazon Web Services (AWS) – the e-commerce giant’s cloud computing arm – located in Singapore and Tokyo to pull off the attacks.
In a response to Re/code, Amazon said the activity being reported is not currently happening on AWS. A spokesperson for the company declined to say whether or not AWS had been used in such a matter before today.
If true, this wouldn’t be the first time that Sony has used such tactics. In the earlier days of file sharing, Sony worked with anti-piracy firm MediaDefender to flood popular file-sharing networks with bogus files in an effort to deter people from downloading their work.
It worked for a bit but eventually fire-sharing sites were able to easily identify the spoof files.
Early indications suggested North Korea was responsible for the attack on Sony Pictures. As recently as Tuesday, however, the FBI said they couldn’t yet determine who was behind the attack.
https://www.techspot.com/news/59140-sony-using-ddos-attacks-slow-spread-stolen-data.html