You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Solved Spyware download fail
- Thread starter samsont1
- Start date
Broni
Posts: 56,041 +517
Results of screen317's Security Check version 0.99.5
Windows 7 (UAC is enabled)
Internet Explorer 8
``````````````````````````````
Antivirus/Firewall Check:
Windows Firewall Enabled!
McAfee Security Scan Plus
McAfee SecurityCenter
[size=1]WMI entry may not exist for antivirus; attempting automatic update.[/size]
```````````````````````````````
Anti-malware/Other Utilities Check:
Malwarebytes' Anti-Malware
Adobe Flash Player 10.1.85.3
Adobe Reader 9.1.2
Out of date Adobe Reader installed!
````````````````````````````````
Process Check:
objlist.exe by Laurent
Windows Defender MSMpEng.exe
Microsoft Security Essentials msseces.exe
````````````````````````````````
DNS Vulnerability Check:
GREAT! (Not vulnerable to DNS cache poisoning)
``````````End of Log````````````
Windows 7 (UAC is enabled)
Internet Explorer 8
``````````````````````````````
Antivirus/Firewall Check:
Windows Firewall Enabled!
McAfee Security Scan Plus
McAfee SecurityCenter
[size=1]WMI entry may not exist for antivirus; attempting automatic update.[/size]
```````````````````````````````
Anti-malware/Other Utilities Check:
Malwarebytes' Anti-Malware
Adobe Flash Player 10.1.85.3
Adobe Reader 9.1.2
Out of date Adobe Reader installed!
````````````````````````````````
Process Check:
objlist.exe by Laurent
Windows Defender MSMpEng.exe
Microsoft Security Essentials msseces.exe
````````````````````````````````
DNS Vulnerability Check:
GREAT! (Not vulnerable to DNS cache poisoning)
``````````End of Log````````````
Broni
Posts: 56,041 +517
Update Adobe Reader
You can download it from https://www.techspot.com/downloads/2083-adobe-reader-dc.html
After installing the latest Adobe Reader, uninstall all previous versions.
Note. If you already have Adobe Photoshop® Album Starter Edition installed or do not wish to have it installed UNcheck the box which says Also Download Adobe Photoshop® Album Starter Edition.
Alternatively, you can uninstall Adobe Reader (33.5 MB), download and install Foxit PDF Reader(3.5MB) from HERE.
It's a much smaller file to download and uses a lot less resources than Adobe Reader.
Note: When installing FoxitReader, make sure to UN-check any pre-checked toolbar, or other garbage.
On this page:
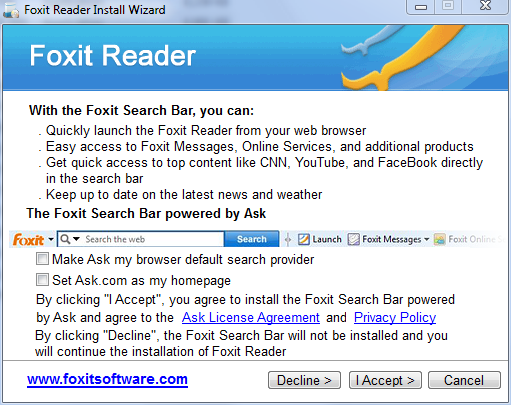
make sure, you have both boxes UN-checked AND (important!) click on Decline button
You can download it from https://www.techspot.com/downloads/2083-adobe-reader-dc.html
After installing the latest Adobe Reader, uninstall all previous versions.
Note. If you already have Adobe Photoshop® Album Starter Edition installed or do not wish to have it installed UNcheck the box which says Also Download Adobe Photoshop® Album Starter Edition.
Alternatively, you can uninstall Adobe Reader (33.5 MB), download and install Foxit PDF Reader(3.5MB) from HERE.
It's a much smaller file to download and uses a lot less resources than Adobe Reader.
Note: When installing FoxitReader, make sure to UN-check any pre-checked toolbar, or other garbage.
On this page:

make sure, you have both boxes UN-checked AND (important!) click on Decline button
Broni
Posts: 56,041 +517
Open Windows Explorer. Go Tools>Folder Options>View tab, put a checkmark next to Show hidden files, and folders.
Upload following files to http://www.virustotal.com/ for security check:
- C:\Nexon\MapleStory\JackMs.exe
IMPORTANT! If the file is listed as already analyzed, click on Reanalyse file now button.
Post scan results.
Upload following files to http://www.virustotal.com/ for security check:
- C:\Nexon\MapleStory\JackMs.exe
IMPORTANT! If the file is listed as already analyzed, click on Reanalyse file now button.
Post scan results.
Antivirus Version Last Update Result
AhnLab-V3 2010.11.05.01 2010.11.05 -
AntiVir 7.10.13.145 2010.11.05 TR/Spy.Gen
Antiy-AVL 2.0.3.7 2010.11.05 Trojan/Win32.OnLineGames.gen
Authentium 5.2.0.5 2010.11.05 -
Avast 4.8.1351.0 2010.11.05 -
Avast5 5.0.594.0 2010.11.05 -
AVG 9.0.0.851 2010.11.06 -
BitDefender 7.2 2010.11.06 -
CAT-QuickHeal 11.00 2010.11.04 Trojan.Agent.ATV
ClamAV 0.96.2.0-git 2010.11.05 PUA.Packed.Themida-1
Comodo 6626 2010.11.05 -
DrWeb 5.0.2.03300 2010.11.06 -
Emsisoft 5.0.0.50 2010.11.05 Win32.SuspectCrc!IK
eSafe 7.0.17.0 2010.11.04 Win32.PCKDumped
eTrust-Vet 36.1.7958 2010.11.05 -
F-Prot 4.6.2.117 2010.11.05 -
F-Secure 9.0.16160.0 2010.11.06 -
Fortinet 4.2.249.0 2010.11.05 -
GData 21 2010.11.05 -
Ikarus T3.1.1.90.0 2010.11.05 Win32.SuspectCrc
Jiangmin 13.0.900 2010.11.05 Trojan/PSW.OnLineGames.bmhy
K7AntiVirus 9.67.2903 2010.11.03 -
Kaspersky 7.0.0.125 2010.11.05 -
McAfee 5.400.0.1158 2010.11.06 -
McAfee-GW-Edition 2010.1C 2010.11.05 -
Microsoft 1.6301 2010.11.05 -
NOD32 5595 2010.11.05 probably a variant of Win32/PSW.OnLineGames.EQHJBHZ
Norman 6.06.10 2010.11.05 W32/Suspicious_Gen2.CHKFH
nProtect 2010-11-05.01 2010.11.05 Trojan/W32.Agent.8867840
Panda 10.0.2.7 2010.11.05 -
PCTools 7.0.3.5 2010.11.05 Trojan.Gen
Prevx 3.0 2010.11.06 Medium Risk Malware
Rising 22.72.03.04 2010.11.05 -
Sophos 4.59.0 2010.11.06 -
Sunbelt 7228 2010.11.06 Trojan.Win32.Generic!BT
SUPERAntiSpyware 4.40.0.1006 2010.11.05 -
Symantec 20101.2.0.161 2010.11.06 Trojan.Gen
TheHacker 6.7.0.1.076 2010.11.05 W32/Behav-Heuristic-064
TrendMicro 9.120.0.1004 2010.11.05 -
TrendMicro-HouseCall 9.120.0.1004 2010.11.06 -
VBA32 3.12.14.1 2010.11.05 Trojan-GameThief.Win32.OnLineGames.wbxl
ViRobot 2010.10.4.4074 2010.11.05 -
VirusBuster 12.71.7.0 2010.11.05 TrojanSpy.Agent.QUIQ
Additional information
Show all
MD5 : 0c597ceead437f63230a2fd49148cb5d
SHA1 : af08e7f49b9a8009588068a002b2a539d9696866
SHA256: 4d1cc023ba8c622bf282ea66f5c9c8a85fc3ef1bdd2e466324c2adbd059bc23f
ssdeep: 98304:a4B3aaftbsmDbpkAjxYBWBhQIY7hdOH6CNC/Mu6GL/BRxXRZAXa3L:a4BKaftb/mVWoaN
q7FRZk+L
File size : 8867840 bytes
First seen: 2010-11-06 00:17:11
Last seen : 2010-11-06 00:17:11
TrID:
Win32 Executable Generic (68.0%)
Generic Win/DOS Executable (15.9%)
DOS Executable Generic (15.9%)
Autodesk FLIC Image File (extensions: flc, fli, cel) (0.0%)
sigcheck:
publisher....: Wizet
copyright....: Copyright _ 2003
product......: Wizet MapleStory
description..: MapleStory
original name: MapleStory.exe
internal name: MapleStory
file version.: 1, 0, 0, 1
comments.....:
signers......: -
signing date.: -
verified.....: Unsigned
PEiD: Armadillo v1.71
PEInfo: PE structure information
[[ basic data ]]
entrypointaddress: 0x561865
timedatestamp....: 0x4A93ED28 (Tue Aug 25 13:54:48 2009)
machinetype......: 0x14c (I386)
[[ 5 section(s) ]]
name, viradd, virsiz, rawdsiz, ntropy, md5
, 0x1000, 0x6BD000, 0x6BD000, 6.55, ec55278f2cbeba393dc42f42f923f284
.rsrc, 0x6BE000, 0x1F4D0, 0x1F4D0, 6.65, 537b4539b7f56214c50097f92035c18a
.idata , 0x6DE000, 0x1000, 0x1000, 0.25, 7570c9aa4de54b2a9dbf9a129236bd94
Themida , 0x6DF000, 0x194000, 0x194000, 7.64, 0cada496d98ae1597fd6483cca8a3c4c
.mackt, 0x873000, 0x2000, 0x2000, 3.37, d89fedd20ed6ea3c9284c2b19aca1229
[[ 15 import(s) ]]
advapi32.dll: RegQueryValueExA, RegSetValueExA, RegDeleteValueA, RegOpenKeyExA, AdjustTokenPrivileges, RegCloseKey, OpenProcessToken, LookupPrivilegeValueA
dinput8.dll: DirectInput8Create
gdi32.dll: DeleteObject, CreateCompatibleDC, SelectObject, BitBlt, DeleteDC, GetObjectA, CreateDIBSection
kernel32.dll: FindFirstFileA, WaitForSingleObject, CreateProcessA, MultiByteToWideChar, IsDBCSLeadByte, SystemTimeToFileTime, GetLocalTime, GetVersion, FileTimeToSystemTime, lstrcpy, CompareFileTime, lstrcmp, GetVolumeInformationA, GetWindowsDirectoryA, GetLastError, CreateDirectoryA, FreeLibrary, GetProcAddress, LoadLibraryA, lstrcmpi, SetUnhandledExceptionFilter, IsBadWritePtr, GetVersionExA, LocalAlloc, lstrlen, FormatMessageA, GetCurrentThreadId, GetModuleFileNameA, Sleep, GetModuleHandleA, DeleteFileA, GetTickCount, VirtualQuery, UnmapViewOfFile, MapViewOfFile, CreateFileMappingA, GetFileType, GetStdHandle, SetHandleCount, GetEnvironmentStringsW, GetEnvironmentStrings, FreeEnvironmentStringsW, FreeEnvironmentStringsA, LCMapStringW, LCMapStringA, GetOEMCP, GetACP, GetCPInfo, ReadFile, VirtualFree, HeapCreate, HeapDestroy, GetEnvironmentVariableA, UnhandledExceptionFilter, GetCurrentThread, TlsFree, TlsAlloc, FatalAppExitA, LeaveCriticalSection, EnterCriticalSection, DeleteCriticalSection, FindNextFileA, FindClose, GetSystemDirectoryA, GetTempPathA, GetTempFileNameA, CopyFileA, OpenMutexA, CreateFileA, SetFilePointer, WriteFile, LoadLibraryExA, IsBadReadPtr, GetCurrentProcess, CloseHandle, InterlockedExchange, InitializeCriticalSection, HeapSize, IsBadCodePtr, HeapReAlloc, GetCommandLineA, GetStartupInfoA, ExitProcess, FileTimeToLocalFileTime, ExitThread, TlsGetValue, TlsSetValue, CreateThread, RaiseException, RtlUnwind, lstrlenW, GetProcessHeap, HeapAlloc, HeapFree, WideCharToMultiByte, VirtualProtect, LocalFree, InterlockedIncrement, CreateMutexA, OpenProcess, SetEvent, SetEnvironmentVariableA, CompareStringW, CompareStringA, GetLocaleInfoW, SetEndOfFile, SetConsoleCtrlHandler, GetTimeZoneInformation, FlushFileBuffers, SetStdHandle, GetUserDefaultLCID, EnumSystemLocalesA, GetLocaleInfoA, IsValidCodePage, IsValidLocale, VirtualAlloc, InterlockedDecrement, GetStringTypeW, GetStringTypeA, Thread32Next, Thread32First, Process32Next, Process32First, CreateToolhelp32Snapshot, TerminateProcess, CreateEventA, GetFileSize, SetLastError, ReleaseMutex
netapi32.dll: Netbios
oleaut32.dll: VariantChangeType, VariantClear, GetErrorInfo, VariantInit, SetErrorInfo, SysFreeString, CreateErrorInfo, SysAllocString, VariantCopy, SafeArrayDestroy, SafeArrayCreate
shell32.dll: SHGetSpecialFolderPathA
user32.dll: SetRect, SetRectEmpty, CharUpperBuffA, EnumThreadWindows, ShowCursor, MapVirtualKeyA, SetWindowPos, GetWindowRect, MoveWindow, GetWindow, SendMessageA, FindWindowA, IsWindowEnabled, GetWindowThreadProcessId, AttachThreadInput, BringWindowToTop, wsprintfA, PtInRect, wvsprintfA, MessageBoxA, LoadBitmapA, CreateWindowExA, EnableWindow, OffsetRect, GetDlgItem, DialogBoxParamA, GetWindowTextA
version.dll: VerQueryValueA, GetFileVersionInfoA, GetFileVersionInfoSizeA
wininet.dll: FtpGetFileSize, HttpSendRequestA, InternetSetStatusCallback, HttpOpenRequestA, InternetOpenA, InternetCloseHandle, FtpGetFileA, InternetConnectA, FtpOpenFileA
winmm.dll: timeGetTime
ws2_32.dll: htonl, htons, closesocket, inet_addr, socket, getpeername, getsockname, WSAStartup, WSACleanup, WSAGetLastError, gethostbyname, htons
ijl15.dll: ijlWrite, ijlRead, ijlFree, ijlInit
iphlpapi.dll: GetAdaptersInfo
ole32.dll: CoCreateGuid
[[ 3 export(s) ]]
ZtlTaskMemAllocImp, ZtlTaskMemFreeImp, ZtlTaskMemReallocImp
Prevx Info:
http://info.prevx.com/aboutprogramtext.asp?PX5=51271B390073A27250FF87B148357600EF54C710
ExifTool:
file metadata
CharacterSet: Unicode
CodeSize: 6139904
Comments:
CompanyName: Wizet
EntryPoint: 0x561865
FileDescription: MapleStory
FileFlagsMask: 0x003f
FileOS: Windows NT 32-bit
FileSize: 8.5 MB
FileSubtype: 0
FileType: Win32 EXE
FileVersion: 1, 0, 0, 1
FileVersionNumber: 1.0.0.1
ImageVersion: 0.0
InitializedDataSize: 1056768
InternalName: MapleStory
LanguageCode: Korean
LegalCopyright: Copyright 2003
LegalTrademarks:
LinkerVersion: 6.0
MIMEType: application/octet-stream
MachineType: Intel 386 or later, and compatibles
OSVersion: 4.0
ObjectFileType: Executable application
OriginalFilename: MapleStory.exe
PEType: PE32
PrivateBuild:
ProductName: Wizet MapleStory
ProductVersion: 1, 0, 0, 1
ProductVersionNumber: 1.0.0.1
SpecialBuild:
Subsystem: Windows GUI
SubsystemVersion: 4.0
TimeStamp: 2009:08:25 15:54:48+02:00
UninitializedDataSize: 0
AhnLab-V3 2010.11.05.01 2010.11.05 -
AntiVir 7.10.13.145 2010.11.05 TR/Spy.Gen
Antiy-AVL 2.0.3.7 2010.11.05 Trojan/Win32.OnLineGames.gen
Authentium 5.2.0.5 2010.11.05 -
Avast 4.8.1351.0 2010.11.05 -
Avast5 5.0.594.0 2010.11.05 -
AVG 9.0.0.851 2010.11.06 -
BitDefender 7.2 2010.11.06 -
CAT-QuickHeal 11.00 2010.11.04 Trojan.Agent.ATV
ClamAV 0.96.2.0-git 2010.11.05 PUA.Packed.Themida-1
Comodo 6626 2010.11.05 -
DrWeb 5.0.2.03300 2010.11.06 -
Emsisoft 5.0.0.50 2010.11.05 Win32.SuspectCrc!IK
eSafe 7.0.17.0 2010.11.04 Win32.PCKDumped
eTrust-Vet 36.1.7958 2010.11.05 -
F-Prot 4.6.2.117 2010.11.05 -
F-Secure 9.0.16160.0 2010.11.06 -
Fortinet 4.2.249.0 2010.11.05 -
GData 21 2010.11.05 -
Ikarus T3.1.1.90.0 2010.11.05 Win32.SuspectCrc
Jiangmin 13.0.900 2010.11.05 Trojan/PSW.OnLineGames.bmhy
K7AntiVirus 9.67.2903 2010.11.03 -
Kaspersky 7.0.0.125 2010.11.05 -
McAfee 5.400.0.1158 2010.11.06 -
McAfee-GW-Edition 2010.1C 2010.11.05 -
Microsoft 1.6301 2010.11.05 -
NOD32 5595 2010.11.05 probably a variant of Win32/PSW.OnLineGames.EQHJBHZ
Norman 6.06.10 2010.11.05 W32/Suspicious_Gen2.CHKFH
nProtect 2010-11-05.01 2010.11.05 Trojan/W32.Agent.8867840
Panda 10.0.2.7 2010.11.05 -
PCTools 7.0.3.5 2010.11.05 Trojan.Gen
Prevx 3.0 2010.11.06 Medium Risk Malware
Rising 22.72.03.04 2010.11.05 -
Sophos 4.59.0 2010.11.06 -
Sunbelt 7228 2010.11.06 Trojan.Win32.Generic!BT
SUPERAntiSpyware 4.40.0.1006 2010.11.05 -
Symantec 20101.2.0.161 2010.11.06 Trojan.Gen
TheHacker 6.7.0.1.076 2010.11.05 W32/Behav-Heuristic-064
TrendMicro 9.120.0.1004 2010.11.05 -
TrendMicro-HouseCall 9.120.0.1004 2010.11.06 -
VBA32 3.12.14.1 2010.11.05 Trojan-GameThief.Win32.OnLineGames.wbxl
ViRobot 2010.10.4.4074 2010.11.05 -
VirusBuster 12.71.7.0 2010.11.05 TrojanSpy.Agent.QUIQ
Additional information
Show all
MD5 : 0c597ceead437f63230a2fd49148cb5d
SHA1 : af08e7f49b9a8009588068a002b2a539d9696866
SHA256: 4d1cc023ba8c622bf282ea66f5c9c8a85fc3ef1bdd2e466324c2adbd059bc23f
ssdeep: 98304:a4B3aaftbsmDbpkAjxYBWBhQIY7hdOH6CNC/Mu6GL/BRxXRZAXa3L:a4BKaftb/mVWoaN
q7FRZk+L
File size : 8867840 bytes
First seen: 2010-11-06 00:17:11
Last seen : 2010-11-06 00:17:11
TrID:
Win32 Executable Generic (68.0%)
Generic Win/DOS Executable (15.9%)
DOS Executable Generic (15.9%)
Autodesk FLIC Image File (extensions: flc, fli, cel) (0.0%)
sigcheck:
publisher....: Wizet
copyright....: Copyright _ 2003
product......: Wizet MapleStory
description..: MapleStory
original name: MapleStory.exe
internal name: MapleStory
file version.: 1, 0, 0, 1
comments.....:
signers......: -
signing date.: -
verified.....: Unsigned
PEiD: Armadillo v1.71
PEInfo: PE structure information
[[ basic data ]]
entrypointaddress: 0x561865
timedatestamp....: 0x4A93ED28 (Tue Aug 25 13:54:48 2009)
machinetype......: 0x14c (I386)
[[ 5 section(s) ]]
name, viradd, virsiz, rawdsiz, ntropy, md5
, 0x1000, 0x6BD000, 0x6BD000, 6.55, ec55278f2cbeba393dc42f42f923f284
.rsrc, 0x6BE000, 0x1F4D0, 0x1F4D0, 6.65, 537b4539b7f56214c50097f92035c18a
.idata , 0x6DE000, 0x1000, 0x1000, 0.25, 7570c9aa4de54b2a9dbf9a129236bd94
Themida , 0x6DF000, 0x194000, 0x194000, 7.64, 0cada496d98ae1597fd6483cca8a3c4c
.mackt, 0x873000, 0x2000, 0x2000, 3.37, d89fedd20ed6ea3c9284c2b19aca1229
[[ 15 import(s) ]]
advapi32.dll: RegQueryValueExA, RegSetValueExA, RegDeleteValueA, RegOpenKeyExA, AdjustTokenPrivileges, RegCloseKey, OpenProcessToken, LookupPrivilegeValueA
dinput8.dll: DirectInput8Create
gdi32.dll: DeleteObject, CreateCompatibleDC, SelectObject, BitBlt, DeleteDC, GetObjectA, CreateDIBSection
kernel32.dll: FindFirstFileA, WaitForSingleObject, CreateProcessA, MultiByteToWideChar, IsDBCSLeadByte, SystemTimeToFileTime, GetLocalTime, GetVersion, FileTimeToSystemTime, lstrcpy, CompareFileTime, lstrcmp, GetVolumeInformationA, GetWindowsDirectoryA, GetLastError, CreateDirectoryA, FreeLibrary, GetProcAddress, LoadLibraryA, lstrcmpi, SetUnhandledExceptionFilter, IsBadWritePtr, GetVersionExA, LocalAlloc, lstrlen, FormatMessageA, GetCurrentThreadId, GetModuleFileNameA, Sleep, GetModuleHandleA, DeleteFileA, GetTickCount, VirtualQuery, UnmapViewOfFile, MapViewOfFile, CreateFileMappingA, GetFileType, GetStdHandle, SetHandleCount, GetEnvironmentStringsW, GetEnvironmentStrings, FreeEnvironmentStringsW, FreeEnvironmentStringsA, LCMapStringW, LCMapStringA, GetOEMCP, GetACP, GetCPInfo, ReadFile, VirtualFree, HeapCreate, HeapDestroy, GetEnvironmentVariableA, UnhandledExceptionFilter, GetCurrentThread, TlsFree, TlsAlloc, FatalAppExitA, LeaveCriticalSection, EnterCriticalSection, DeleteCriticalSection, FindNextFileA, FindClose, GetSystemDirectoryA, GetTempPathA, GetTempFileNameA, CopyFileA, OpenMutexA, CreateFileA, SetFilePointer, WriteFile, LoadLibraryExA, IsBadReadPtr, GetCurrentProcess, CloseHandle, InterlockedExchange, InitializeCriticalSection, HeapSize, IsBadCodePtr, HeapReAlloc, GetCommandLineA, GetStartupInfoA, ExitProcess, FileTimeToLocalFileTime, ExitThread, TlsGetValue, TlsSetValue, CreateThread, RaiseException, RtlUnwind, lstrlenW, GetProcessHeap, HeapAlloc, HeapFree, WideCharToMultiByte, VirtualProtect, LocalFree, InterlockedIncrement, CreateMutexA, OpenProcess, SetEvent, SetEnvironmentVariableA, CompareStringW, CompareStringA, GetLocaleInfoW, SetEndOfFile, SetConsoleCtrlHandler, GetTimeZoneInformation, FlushFileBuffers, SetStdHandle, GetUserDefaultLCID, EnumSystemLocalesA, GetLocaleInfoA, IsValidCodePage, IsValidLocale, VirtualAlloc, InterlockedDecrement, GetStringTypeW, GetStringTypeA, Thread32Next, Thread32First, Process32Next, Process32First, CreateToolhelp32Snapshot, TerminateProcess, CreateEventA, GetFileSize, SetLastError, ReleaseMutex
netapi32.dll: Netbios
oleaut32.dll: VariantChangeType, VariantClear, GetErrorInfo, VariantInit, SetErrorInfo, SysFreeString, CreateErrorInfo, SysAllocString, VariantCopy, SafeArrayDestroy, SafeArrayCreate
shell32.dll: SHGetSpecialFolderPathA
user32.dll: SetRect, SetRectEmpty, CharUpperBuffA, EnumThreadWindows, ShowCursor, MapVirtualKeyA, SetWindowPos, GetWindowRect, MoveWindow, GetWindow, SendMessageA, FindWindowA, IsWindowEnabled, GetWindowThreadProcessId, AttachThreadInput, BringWindowToTop, wsprintfA, PtInRect, wvsprintfA, MessageBoxA, LoadBitmapA, CreateWindowExA, EnableWindow, OffsetRect, GetDlgItem, DialogBoxParamA, GetWindowTextA
version.dll: VerQueryValueA, GetFileVersionInfoA, GetFileVersionInfoSizeA
wininet.dll: FtpGetFileSize, HttpSendRequestA, InternetSetStatusCallback, HttpOpenRequestA, InternetOpenA, InternetCloseHandle, FtpGetFileA, InternetConnectA, FtpOpenFileA
winmm.dll: timeGetTime
ws2_32.dll: htonl, htons, closesocket, inet_addr, socket, getpeername, getsockname, WSAStartup, WSACleanup, WSAGetLastError, gethostbyname, htons
ijl15.dll: ijlWrite, ijlRead, ijlFree, ijlInit
iphlpapi.dll: GetAdaptersInfo
ole32.dll: CoCreateGuid
[[ 3 export(s) ]]
ZtlTaskMemAllocImp, ZtlTaskMemFreeImp, ZtlTaskMemReallocImp
Prevx Info:
http://info.prevx.com/aboutprogramtext.asp?PX5=51271B390073A27250FF87B148357600EF54C710
ExifTool:
file metadata
CharacterSet: Unicode
CodeSize: 6139904
Comments:
CompanyName: Wizet
EntryPoint: 0x561865
FileDescription: MapleStory
FileFlagsMask: 0x003f
FileOS: Windows NT 32-bit
FileSize: 8.5 MB
FileSubtype: 0
FileType: Win32 EXE
FileVersion: 1, 0, 0, 1
FileVersionNumber: 1.0.0.1
ImageVersion: 0.0
InitializedDataSize: 1056768
InternalName: MapleStory
LanguageCode: Korean
LegalCopyright: Copyright 2003
LegalTrademarks:
LinkerVersion: 6.0
MIMEType: application/octet-stream
MachineType: Intel 386 or later, and compatibles
OSVersion: 4.0
ObjectFileType: Executable application
OriginalFilename: MapleStory.exe
PEType: PE32
PrivateBuild:
ProductName: Wizet MapleStory
ProductVersion: 1, 0, 0, 1
ProductVersionNumber: 1.0.0.1
SpecialBuild:
Subsystem: Windows GUI
SubsystemVersion: 4.0
TimeStamp: 2009:08:25 15:54:48+02:00
UninitializedDataSize: 0
Broni
Posts: 56,041 +517
Run OTL
=====================================================================
Your computer is clean
1. We need to reset system restore to prevent your computer from being accidentally reinfected by using some old restore point(s). We'll create fresh, clean restore point, using following OTL script:
Run OTL
2. Now, we'll remove all tools, we used during our cleaning process
Clean up with OTL:
If you still have any tools or logs leftover on your computer you can go ahead and delete those off of your computer now.
3. Make sure, Windows Updates are current.
4. If any Trojan was listed among your infection(s), make sure, you change all of your on-line important passwords (bank account(s), secured web sites, etc.) immediately!
5. Download, and install WOT (Web OF Trust): http://www.mywot.com/. It'll warn you (in most cases) about dangerous web sites.
6. Run Malwarebytes "Quick scan" once in a while to assure safety of your computer.
7. Run Temporary File Cleaner (TFC) weekly.
8. Download and install Secunia Personal Software Inspector (PSI): https://www.techspot.com/downloads/4898-secunia-personal-software-inspector-psi.html. The Secunia PSI is a FREE security tool designed to detect vulnerable and out-dated programs and plug-ins which expose your PC to attacks. Run it weekly.
9. (optional) If you want to keep all your programs up to date, download and install FileHippo Update Checker.
The Update Checker will scan your computer for installed software, check the versions and then send this information to FileHippo.com to see if there are any newer releases.
10. Run defrag at your convenience.
11. Read How did I get infected?, With steps so it does not happen again!: http://www.bleepingcomputer.com/forums/topic2520.html
12. Please, let me know, how is your computer doing.
- Under the Custom Scans/Fixes box at the bottom, paste in the following
Code::OTL :Services :Reg :Files C:\Nexon\MapleStory\JackMs.exe :Commands [purity] [emptytemp] [emptyflash] [Reboot] - Then click the Run Fix button at the top
- Let the program run unhindered, reboot the PC when it is done
- You will get a log that shows the results of the fix. Please post it.
=====================================================================
Your computer is clean
1. We need to reset system restore to prevent your computer from being accidentally reinfected by using some old restore point(s). We'll create fresh, clean restore point, using following OTL script:
Run OTL
- Under the Custom Scans/Fixes box at the bottom, paste in the following:
Code:
:OTL
:Commands
[purity]
[emptytemp]
[EMPTYFLASH]
[CLEARALLRESTOREPOINTS]
[Reboot]- Then click the Run Fix button at the top
- Let the program run unhindered, reboot the PC when it is done
- Post resulting log.
2. Now, we'll remove all tools, we used during our cleaning process
Clean up with OTL:
- Double-click OTL.exe to start the program.
- Close all other programs apart from OTL as this step will require a reboot
- On the OTL main screen, press the CLEANUP button
- Say Yes to the prompt and then allow the program to reboot your computer.
If you still have any tools or logs leftover on your computer you can go ahead and delete those off of your computer now.
3. Make sure, Windows Updates are current.
4. If any Trojan was listed among your infection(s), make sure, you change all of your on-line important passwords (bank account(s), secured web sites, etc.) immediately!
5. Download, and install WOT (Web OF Trust): http://www.mywot.com/. It'll warn you (in most cases) about dangerous web sites.
6. Run Malwarebytes "Quick scan" once in a while to assure safety of your computer.
7. Run Temporary File Cleaner (TFC) weekly.
8. Download and install Secunia Personal Software Inspector (PSI): https://www.techspot.com/downloads/4898-secunia-personal-software-inspector-psi.html. The Secunia PSI is a FREE security tool designed to detect vulnerable and out-dated programs and plug-ins which expose your PC to attacks. Run it weekly.
9. (optional) If you want to keep all your programs up to date, download and install FileHippo Update Checker.
The Update Checker will scan your computer for installed software, check the versions and then send this information to FileHippo.com to see if there are any newer releases.
10. Run defrag at your convenience.
11. Read How did I get infected?, With steps so it does not happen again!: http://www.bleepingcomputer.com/forums/topic2520.html
12. Please, let me know, how is your computer doing.
All processes killed
========== OTL ==========
========== SERVICES/DRIVERS ==========
========== REGISTRY ==========
========== FILES ==========
C:\Nexon\MapleStory\JackMs.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Mcx1-SAMSON-PC
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Public
User: Samson
->Temp folder emptied: 473453 bytes
->Temporary Internet Files folder emptied: 407000 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 97100356 bytes
->Flash cache emptied: 2015 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 4646 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 32902 bytes
RecycleBin emptied: 0 bytes
Total Files Cleaned = 93.00 mb
[EMPTYFLASH]
User: All Users
User: Default
->Flash cache emptied: 0 bytes
User: Default User
->Flash cache emptied: 0 bytes
User: Mcx1-SAMSON-PC
->Flash cache emptied: 0 bytes
User: Public
User: Samson
->Flash cache emptied: 0 bytes
Total Flash Files Cleaned = 0.00 mb
OTL by OldTimer - Version 3.2.17.2 log created on 11052010_205810
Files\Folders moved on Reboot...
C:\Users\Samson\AppData\Local\Temp\FXSAPIDebugLogFile.txt moved successfully.
File\Folder C:\Users\Samson\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{662DCCE1-013A-40C6-A911-427FACBF5BD0}.tmp not found!
Registry entries deleted on Reboot...
========== OTL ==========
========== SERVICES/DRIVERS ==========
========== REGISTRY ==========
========== FILES ==========
C:\Nexon\MapleStory\JackMs.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Mcx1-SAMSON-PC
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: Public
User: Samson
->Temp folder emptied: 473453 bytes
->Temporary Internet Files folder emptied: 407000 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 97100356 bytes
->Flash cache emptied: 2015 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 4646 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 32902 bytes
RecycleBin emptied: 0 bytes
Total Files Cleaned = 93.00 mb
[EMPTYFLASH]
User: All Users
User: Default
->Flash cache emptied: 0 bytes
User: Default User
->Flash cache emptied: 0 bytes
User: Mcx1-SAMSON-PC
->Flash cache emptied: 0 bytes
User: Public
User: Samson
->Flash cache emptied: 0 bytes
Total Flash Files Cleaned = 0.00 mb
OTL by OldTimer - Version 3.2.17.2 log created on 11052010_205810
Files\Folders moved on Reboot...
C:\Users\Samson\AppData\Local\Temp\FXSAPIDebugLogFile.txt moved successfully.
File\Folder C:\Users\Samson\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{662DCCE1-013A-40C6-A911-427FACBF5BD0}.tmp not found!
Registry entries deleted on Reboot...
Broni
Posts: 56,041 +517
There were no trojans present
As for the computer running slow, I'm not sure, what to tell you.
My duty is to make sure, your computer is clean and it is.
You may have some other issues (hardware? Windows files?)).
I can see, you had MyCleanPC Registry Cleaner installed in the past.
Assuming, you used it, it may be a part of your problem.
Registry tools are not recommended and here is why: http://miekiemoes.blogspot.com/2008/02/registry-cleaners-and-system-tweaking_13.html
I also, somehow, missed the fact, that you appear to be running two AV programs, McAfee and Microsoft Security Essentials.
Is that true?
It's little bit confusing, because OTL shows MSE, but SecurityCheck doesn't.
Let me know.
Similar threads
- Replies
- 4
- Views
- 282
- Replies
- 29
- Views
- 1K
Latest posts
-
This new AIO cooler packs more displays than your entire setup
- pcnthuziast replied
-
Layoffs surge in tech: More than 100,000 jobs cut in 2025 so far
- ScottSoapbox replied
-
Steam beta update rolls out redesigned store, makes game discovery easier
- Skye Jacobs replied
-
TechSpot is dedicated to computer enthusiasts and power users.
Ask a question and give support.
Join the community here, it only takes a minute.