Researchers at Kaspersky Lab have discovered an advanced piece of malware dubbed miniFlame (officially referred to as "SPE" and "John" by the designers) being used to attack high-profile targets. miniFlame works as an espionage add-on tool alongside similar state-sponsored code like Flame and Gauss as part of a one-two punch so to speak.
Up to this point, it was believed that Flame and Gauss were independent projects sharing no connection. miniFlame is the first piece of evidence that links the two pieces of code together, suggesting they all came from the same creators. Researchers now think they've just scratched the surface of massive cyber-spy operations going on in the Middle East.
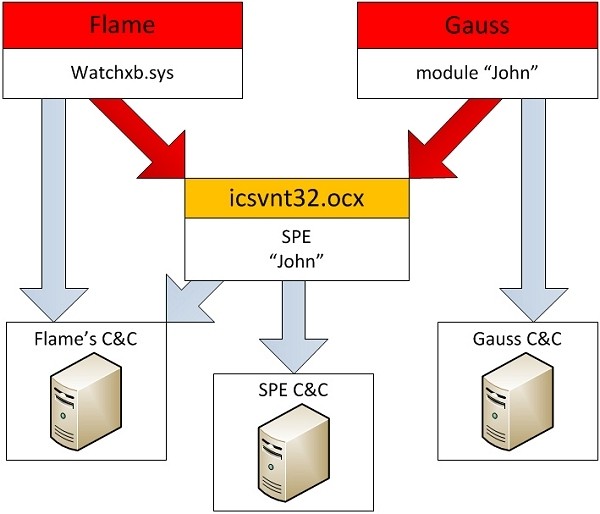
It is thought that thousands of systems were initially infected with Flame in an effort to steal data. This intel was then combed over to single out high-profile targets. Select systems were then infiltrated with miniFlame to gain more extensive intelligence, according to the report.
Once a system is infected with Flame and subsequently miniFlame, the attackers can then send out a module called browse32 that is able to delete Flame from the PC but leave miniFlame intact. Interestingly enough, miniFlame is even able to mark a registry key that will identify its presence to Flame. The key will prevent Flame from being reinstalled should it come in contact with the code in the future.
The specialized malware is believed to have only targeted around 50 systems thus far. This is far fewer than Flame's 5,000 - 6,000 infections or Gauss' 10,000 targets. Researchers say that six variants of miniFlame have been detected thus far dating back to as early as October 2010. Development likely started much sooner, perhaps as early as 2007.