Last week, Samsung found itself in hot water after its Smart TV privacy policy effectively revealed that the devices are potentially eavesdropping on users and sharing the collected information. Shortly thereafter, the company updated the privacy policy, clarifying that only select commands get sent to a third party server, and assured that it employs techniques like data encryption to secure users' personal information. That's not always the case, it seems.
According to researchers at UK-based security firm Pen Test Partners, Samsung's Smart TVs transmit recorded voice data over the Internet in an unencrypted form, making it vulnerable to man-in-middle attacks.
Researcher David Lodge captured and analyzed the Internet traffic generated by Samsung's UE46ES8000 model, which went on sale in 2012, and found that the data is sent in plain text over port 443, which is normally used for TLS-secured HTTPS connections, and typically not blocked by network firewalls.
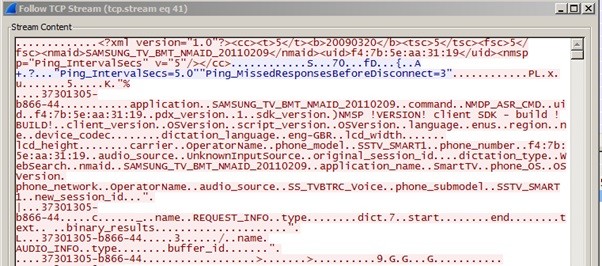
"What we see here is not SSL encrypted data," he said in a blog post. "It's not even HTTP data, it's a mix of XML and some custom binary data packet." The information transmitted by the television included its MAC address, the version of the OS in use, as well as the voice data.
Lodge's investigation also revealed that the response from the third party server was also unencrypted, and the security firm later claimed that its researchers were even able to decode the encoded voice audio, allowing them to replay whatever the television had recorded.
The South Korean electronics giant has now acknowledged that some of its smart TV models are indeed transmitting data in plain text, and claims that it's planning to release new code that would enable encryption.