A new kind of ransomeware designed specifically to target gamers has been doing the rounds according to security analysts at Bromium. The malware, which is a variant of crypto-ransomware called TeslaCrypt, seeks out over 50 file extensions related to video games including Steam, single and multiplayer games, even game development software, and locks the files down. PC gamers are then forced to pay up $500 in Bitcoin or $1,000 in PayPal My Cash cards within 3 days, or they permanently lose their data.
Among the targeted games are a mix of titles including StarCraft II, Warcraft III, Bioshock 2, Call of Duty, DayZ, Diablo, Fallout 3, League of Legends, Minecraft, Metro 2033, Half-Life 2, Dragon Age: Origins, Resident Evil 4, World of Tanks, Metin 2, The Elder Scrolls, among others. The malware also searches for files associated with mods and DLC for other popular titles, as well as photos, documents and iTunes-related files.
The vehicle for delivery is a compromised Wordpress website which redirects visitors to the Angler exploit kit by using a malicious Flash clip hidden in an invisible banner. The exploit only affects Internet Explorer (up to IE 11) and Opera browsers and it scans for virtual machine driver files and "some anti-virus products" before compromising a machine.
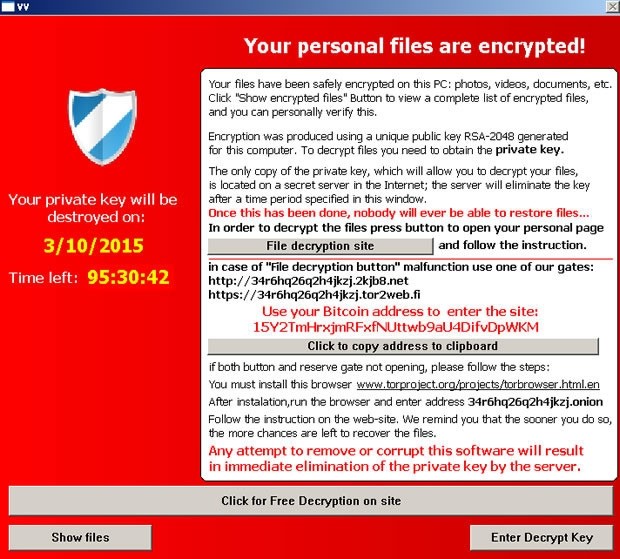
The attack is designed to look like another crypto-ransomware that surfaced last year called CryptoLocker, presumably to cash on its notoriety. It even replaces your wallpaper with a similar ransom note. But researchers say TeslaCrypt shares little code with CryptoLocker or its CryptoWall successor.
Victim are required to install Tor in order to make the payment anonymously. Of course, security experts are advising people not to pay up, and are suggesting users who want to be extra careful can use external drives to keep backups while keeping them unplugged when not in use.