Lenovo has found itself at the center of a bloatware-related security controversy once again after a number of users discovered the company was using a little-known feature in Windows 8 and Windows 10 that allows OEMs to embed a Windows executable in their system firmware.
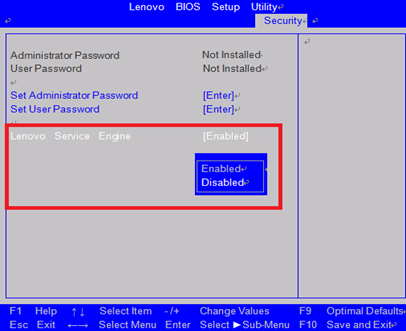
As Ars Technica correctly explains, the feature grants OEMs like Lenovo the ability to load software onto a Windows machine even when a system is wiped clean and a fresh OS installation is performed. Between October 2014 and April of this year, Lenovo allegedly used the technique to install a feature on certain desktops and notebooks it calls Lenovo Service Engine.
Curiously enough, the description of what Lenovo Service Engine does differs on desktops and notebooks.
On desktops, Lenovo claims the software only sends basic information about the system to a Lenovo server and that it only happens once when the system first obtains an Internet connection. On notebooks, Lenovo Service Engine installs OneKey Optimizer which is a firmware, driver and app updater for Lenovo systems.
The issue isn't so much that Lenovo is silently running executables and installing software even on fresh installs of Windows (ok, so maybe it is) but that the Lenovo Service Engine and OneKey Optimizer leave a system open to attack. An Ars Technica forum member found that on Windows 7 systems, Lenovo Service Engine appears to overwrite a Windows system file then creates system services that grab files over unencrypted HTTP.
Lenovo has since stopped including Lenovo Service Engine on new systems and has provided an update to disable it on notebooks and instructions on how to do the same on desktops.