It's not uncommon for developers to have a bit of fun with those who download pirated copies of their games.
In 2013, for example, Greenheart Games released a "cracked" version of Game Dev Tycoon featuring an in-game punishment that made it impossible to progress beyond a certain point. Maxis did something similar a year later with The Sims 4. Others simply concede that piracy is inevitable and upload their games to torrent sites before pirates have the opportunity to do so.
One developer, however, may be taking anti-piracy measures a bit too far.
As Motherboard highlights, a Reddit users recently noticed something fishy with an installer for an add-on for Microsoft Flight Simulator. The piece of software in question, DLC from Flight Sim Labs, Ltd. (FSLabs, for short), reportedly included a file called "text.exe" which apparently extracts all saved usernames and passwords from Chrome and seemingly sends them to FSLabs.
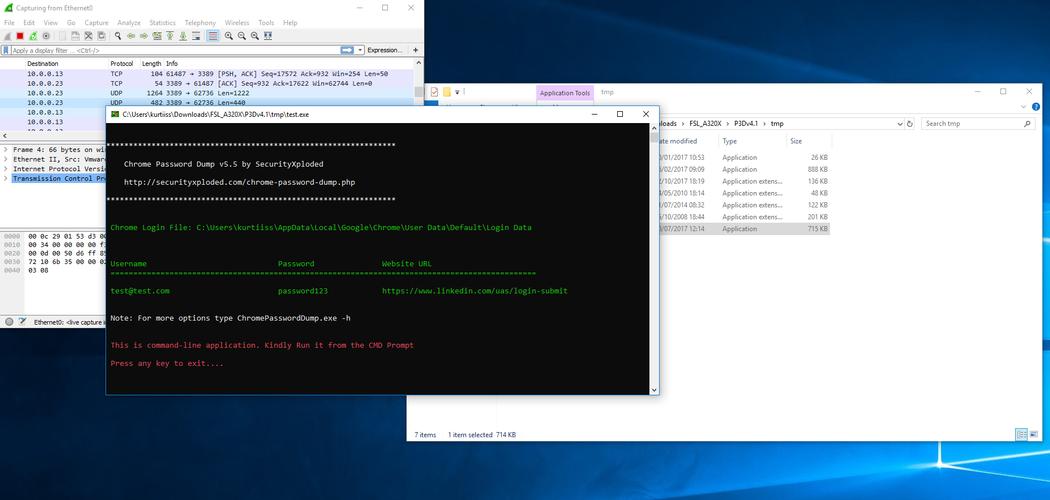
(Screenshot of password stealer courtesy Fidus Information Security)
Andrew Mabbitt, founder of cybersecurity company Fidus Information Security, verified to Motherboard that the malicious software is indeed included in FSLabs' installer. Mabbitt described it as "by far one of the most extreme, and bizarre, methods of Digital Rights Management (DRM) we've ever seen."
Lefteris Kalamaras, founder and owner of FSLabs, had the following to say in a forum post:
1) First of all - there are no tools used to reveal any sensitive information of any customer who has legitimately purchased our products. We all realize that you put a lot of trust in our products and this would be contrary to what we believe.
2) There is a specific method used against specific serial numbers that have been identified as pirate copies and have been making the rounds on ThePirateBay, RuTracker and other such malicious sites.
3) If such a specific serial number is used by a pirate (a person who has illegally obtained our software) and the installer verifies this against the pirate serial numbers stored in our server database, it takes specific measures to alert us. "Test.exe" is part of the DRM and is only targeted against specific pirate copies of copyrighted software obtained illegally. That program is only extracted temporarily and is never under any circumstances used in legitimate copies of the product. The only reason why this file would be detected after the installation completes is only if it was used with a pirate serial number (not blacklisted numbers).
As Mabbitt points out, the malware file itself is "dropped on every single PC it [the FSLabs software] was installed on." Kalamaras doesn't seem to deny this.
In a follow-up post, Kalamaras said they realize that "a few of you were uncomfortable with this particular method which might be considered to be a bit heavy handed on our part. It is for this reason we have uploaded an updated installer that does not include the DRM check file in question."
Motherboard notes that FSLabs has not yet responded to questions regarding what they do with information obtained by the password-stealing malware. In Kalamaras's original post (above), it is noted that "this method has already successfully provided information that we're going to use in our ongoing legal battles against such criminals."
Lead image via Flight Sims Labs Ltd
