We're used to hearing about new types of nasty Android malware, but a newly discovered strain could be one of the most aggressive ever found. Not only can RedDrop steal a device's photos, contacts, files, and other data, but it's also able to record live audio and rack up massive phone bills for the victim.
UK-based mobile security and data management firm Wandera uncovered RedDrop on the phones of employees at several global consultancy firms. It's described as "one of the most sophisticated pieces of Android malware."
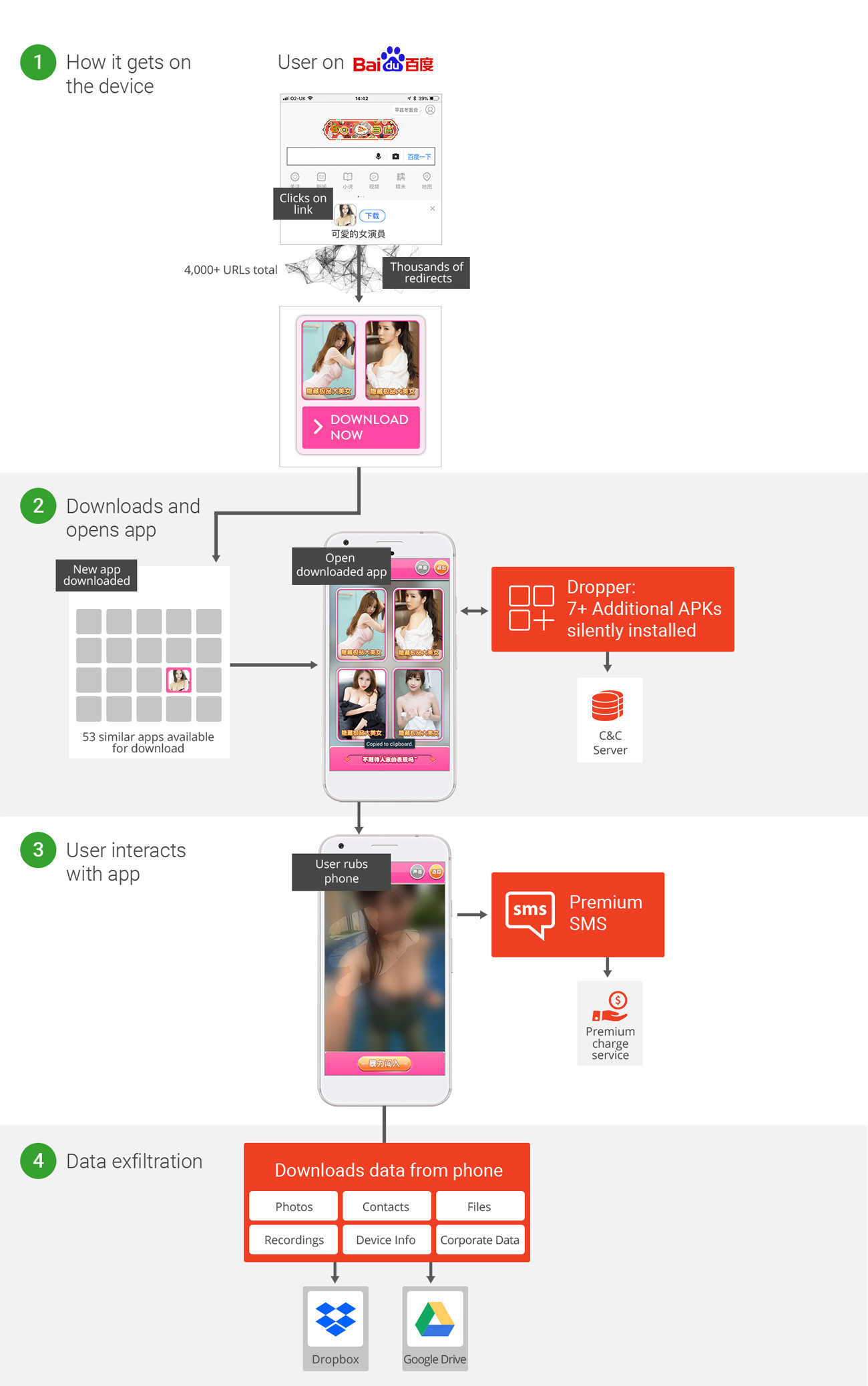
"Wandera's machine learning detections first uncovered one of the RedDrop apps when a user clicked on an ad displaying on popular Chinese search engine Baidu. The user was then taken to huxiawang.cn, the primary distribution site for the attack," wrote researchers.
The landing pages that follow contain content that tries to encourage visitors to download one of the 53 malicious apps from within the RedDrop family. The malware's creators use a content distribution network of over 4000 domains to distribute the applications, which are disguised as calculators, image editors, language learning aids, games, and adult content.
"We believe the group developed this complex CDN [content distribution network] to obfuscate where the malware was served from, making it harder for security teams to detect the source of the threat," added the researchers.
The RedDrop apps contain malicious embedded files, which are arranged in order so they can initiate the malicious functionality. Once installed, the malware downloads additional payloads such as APKs and JAR files from various C&C servers and stores them dynamically in the device's memory.
Each of the infected apps require users to interact with their device. One of them, called "CuteActress," asks players to rub the screen to reveal a seductively-dressed woman, but each time the display is rubbed, the user is unwittingly sending an SMS message to a premium-rate service. The malware even deletes all record of the messages being sent.
RedDrop can also harvest data such as local files (photos/contact etc.), SIM info, app and WiFi info, and device details. It can also grab live audio recordings of local surroundings using a device's microphone. The data is then sent back to the attackers' Dropbox or Drive folders to use for extortion purposes or launch further attacks.
"Not only does the attacker utilize a wide range of functioning malicious applications to entice the victim, they've also perfected every tiny detail to ensure their actions are difficult to trace," the researchers said. "The group that built this malware have planned it exceedingly well."
Wandera recommends disallowing third-party downloads, avoid rooting your device, check which permissions apps request, and use a security solution that can monitor and block C&C traffic at the device level.
