Bottom line: On Tuesday, a security researcher publicly disclosed a zero-day vulnerability in the Zoom video conferencing app for macOS. It seems that a Zoom user's camera can be highjacked by malicious websites.
The problem exists because Zoom installs a local web server that accepts video call requests. What's worse is that uninstalling the app does not delete or uninstall the server, which can then reinstall Zoom without user intervention.
According to Jonathan Leitschuh, the researcher who discovered the security flaw, all that is needed to exploit the vulnerability is a malicious link. Once a user clicks the link, the computer will be auto-joined to a video conference call. Leitschuh says it works even if Zoom has been previously uninstalled. Others have confirmed the weakness on Twitter.
This Zoom vulnerability is bananas. I tried one of the proof of concept links and got connected to three other randos also freaking out about it in real time. https://t.co/w7JKHk8nZy pic.twitter.com/arOE6DbQaf
--- Matt Haughey (@mathowie) July 9, 2019
The same method may also be used to execute a denial of service (DoS) on a user's Mac. Because of the persistent web server, a bad actor could effectively lockup a Mac by continually pinging the server.
"This vulnerability would have allowed any webpage to DoS a Mac by repeatedly joining a user to an invalid call," Leitschuh said. "By simply sending repeated GET requests for a bad number, Zoom app would constantly request 'focus' from the OS."
Leitschuh documented his attempts to get Zoom to address the problem, initially notifying the company back in March. After 90 days, he did not feel that developers had adequately fixed the problem, although the DoS aspect has reportedly been patched. He also disclosed the issue to Chromium and Mozilla.
Zoom issued a statement saying that the web server is used to alleviate "poor user experience" caused by changes to the Safari browser.
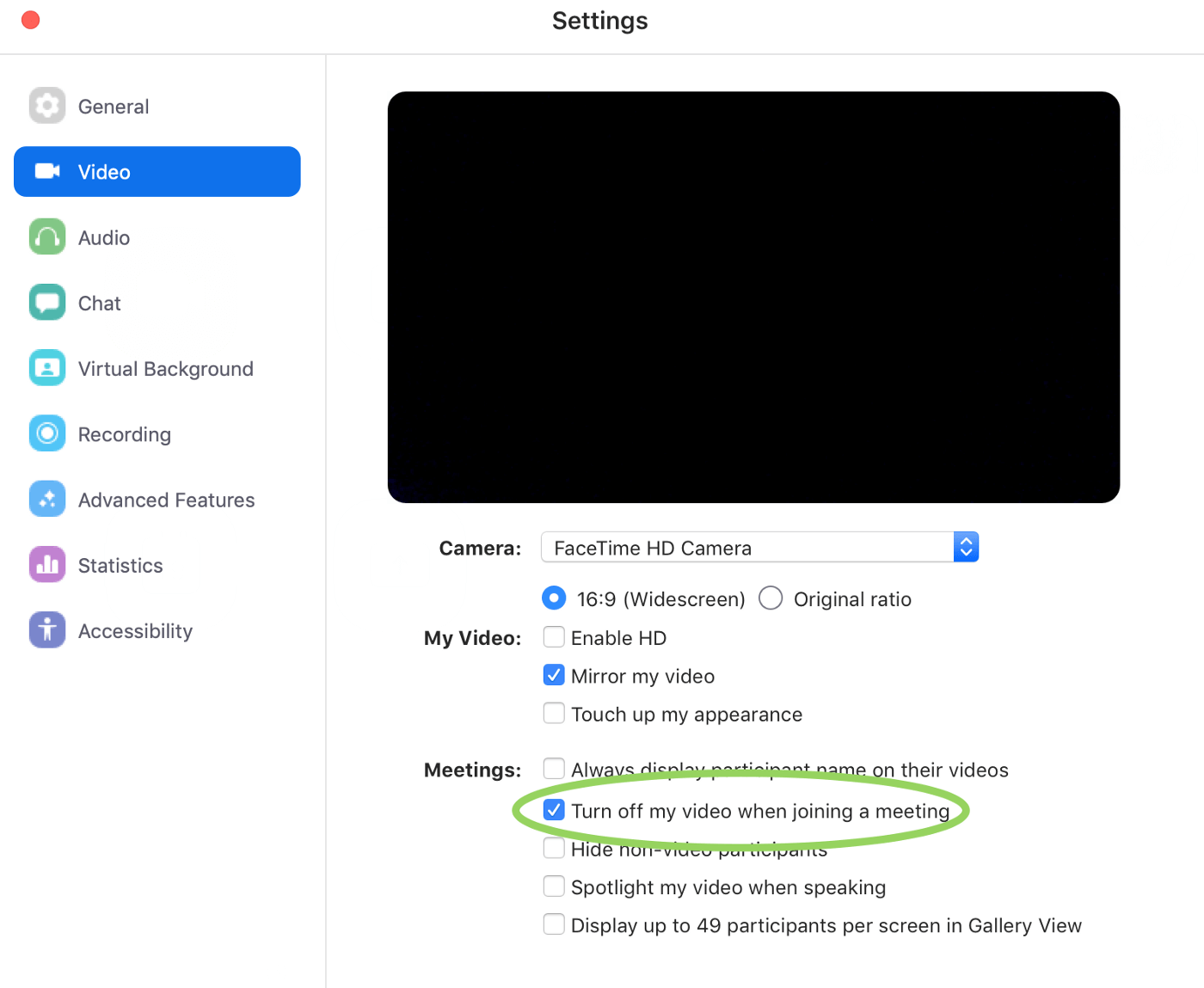
"This is a workaround to a change introduced in Safari 12," said Zoom's Chief Information Security Officer Richard Farley. "We feel that [a local web server] is a legitimate solution to a poor user experience problem, enabling our users to have faster, one-click-to-join meetings. We are not alone among video conferencing providers in implementing this solution."
Without the "workaround," users have to click a confirmation each time they want to use Zoom. The company says it does not plan on changing this feature. It will, however, issue an update this month that will allow the program to save user and administrator preferences regarding whether or not video is turned on or off when first joining a call.
This preference is currently the only way to foil the exploit. In the Settings, under Video, check the box that says, "Turn off my video when joining a meeting (see above)." If this fix is not enough for you or you have previously used Zoom but no longer need it, Leitschuh has some instructions for getting rid of the web server at the bottom of his blog post.
Masthead image credit: Neowin