In brief: Facebook has patched a critical security flaw in WhatsApp's desktop platform that could have allowed an attacker to read files from the local file system on Windows and Mac and even pull off remote code execution.
The vulnerability, which carries a severity rating of 8.2 according to the National Institute of Standards and Technology, was discovered by security researcher Gal Weizman with PerimeterX.
Its origins date back to 2017 when he uncovered the ability to alter the text of someone else's reply. From there, Weizman realized he could craft authentic-looking messages with rich media that redirected the target to a destination of his choosing. Parlaying his success even further, the security researcher was able to use JavaScript to gain a one-click persistent XSS.
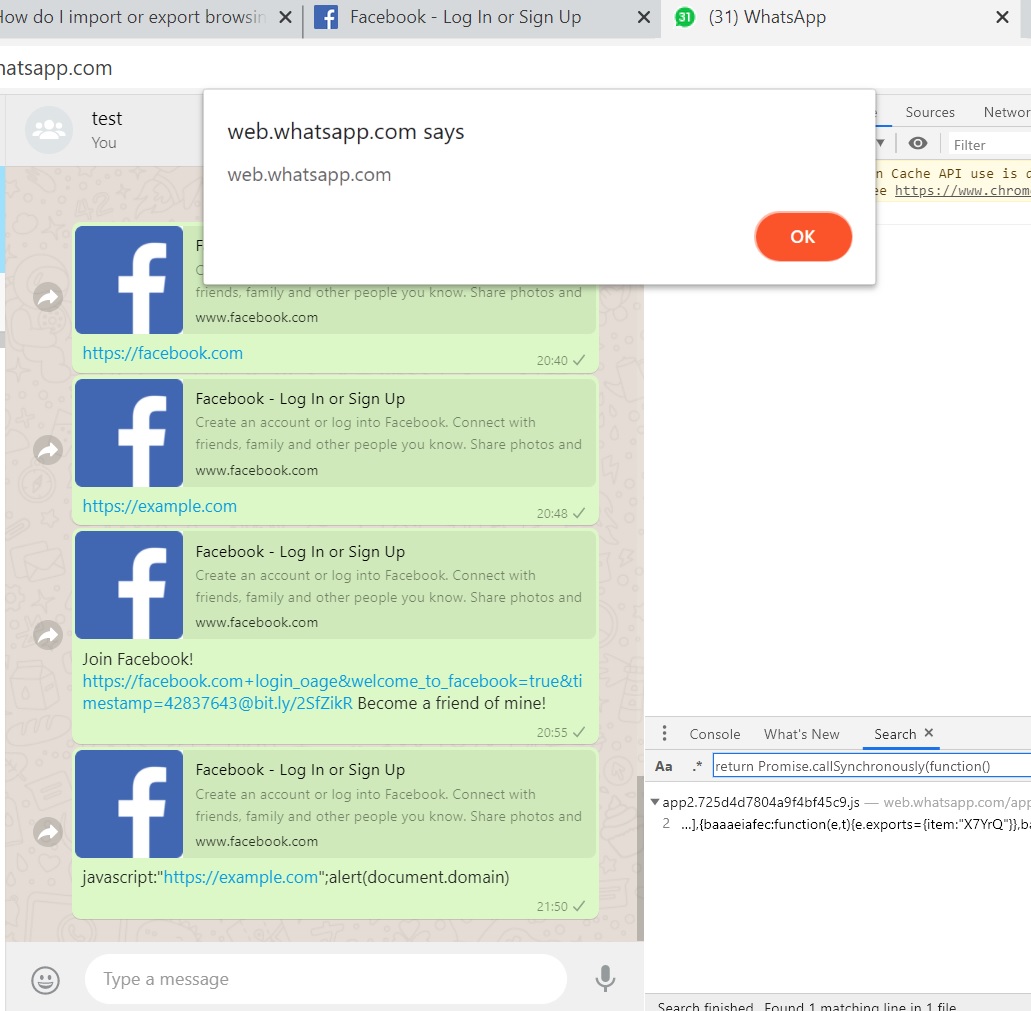
Weizman pressed on and was eventually able to enhance the power of the persistent XSS by bypassing WhatsApp's CPS rules. The coup de grâce was realizing that remote code execution was also possible.
After a bit of digging, the researcher realized that it all worked because the versions of the WhatsApp desktop applications being offered up by Facebook were based on Chrome 69, an outdated version of Google's browser.
This vulnerability was found when Chrome/78 was the stable version! A few versions before Chrome/78, the ability to use the javascript: trick was patched, and if WhatsApp would have updated their Electron web application from 4.1.4 to the latest which was 7.x.x at the time this vulnerability was found(!) - this XSS would never have existed!
Facebook said the vulnerability, CVE-2019-18426, affects WhatsApp Desktop prior to v0.3.9309 paired with WhatsApp for iPhone versions prior to 2.20.10.
Weizman's responsible disclosure of the vulnerability can be found in his PerimeterX blog post.
Masthead credit: WhatsApp by Ink Drop
