Why it matters: "BlackLotus" is being offered on underground forums as an all-powerful firmware rootkit, capable of surviving any removal effort and bypassing the most advanced Windows protections. If actual malware samples can prove the offer is real, of course.
A new powerful UEFI rootkit is reportedly up for sale on underground forums, offering advanced attack features that were previously available only to intelligence agencies and state-backed threat groups. BlackLotus, as the unknown seller has named the malware, is a firmware rootkit that can bypass Windows protections to run malicious code at the lowest level of the x86 architecture protection rings.
According to security researchers that spotted the BlackLotus ads on crimeware forums, a single rootkit user license costs up to $5,000, while a subsequent code rebuild is "just" $200. Considering the capabilities listed by the seller, even spending $5,000 could be seen a real bargain for cyber-criminals and black hat hackers around the world.
As summarized by security researcher Scott Scheferman, BlackLotus is written in Assembly and C and weighs 80 kilobytes (just around 81,920 bytes in size) while it's vendor independent. The rootkit has anti-VM, anti-debug and code obfuscation features to block or hinder analysis attempts, provides an "agent protection" at kernel level (ring 0) for persistence in the UEFI firmware, and it comes with a fully featured install guide and FAQ.
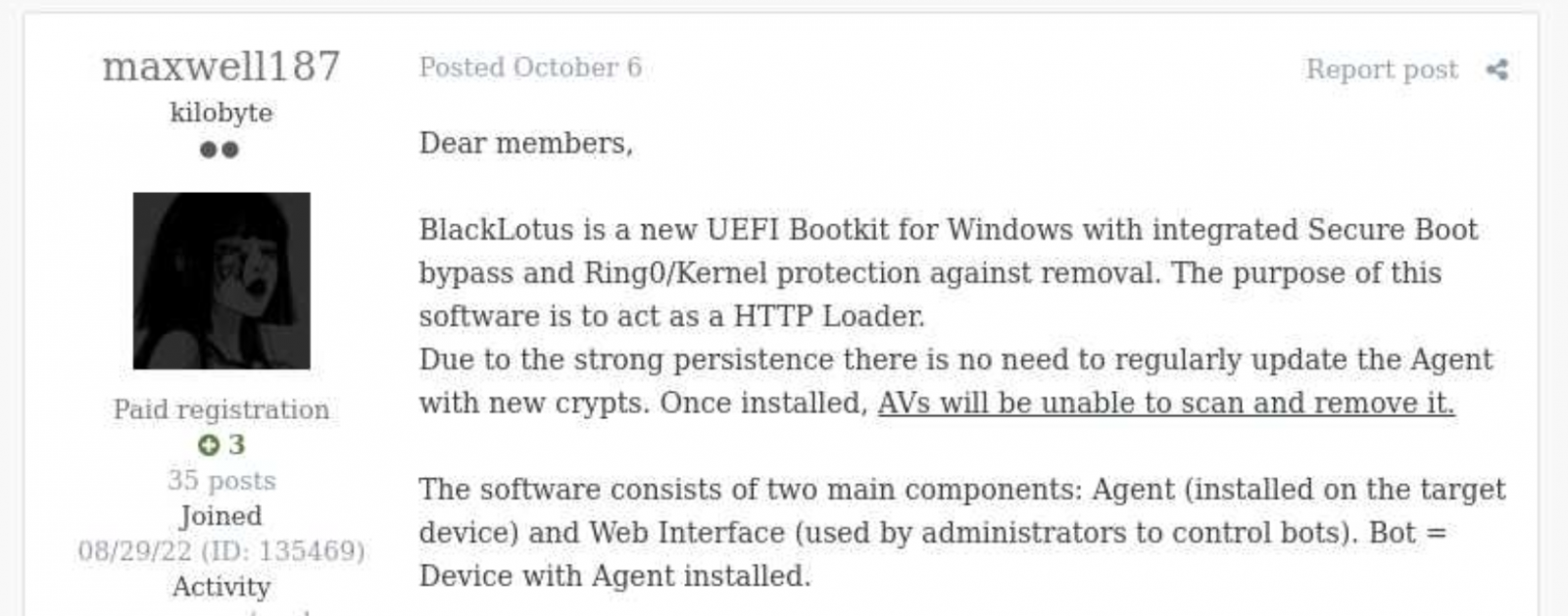
Like any other proper rootkit, BlackLotus is loaded in the very first stages of the boot process before the Windows startup phase. The malware can allegedly bypass many Windows security protections including Secure Boot, UAC, BitLocker, HVCI and Windows Defender, while offering the ability to load unsigned drivers. Other advanced features of the malware include a fully featured file transfer mode, and a "vulnerable signed bootloader" that cannot be invalidated without affecting hundreds of bootloader still in use today.
Scott Scheferman highlights the danger BlackLotus can pose for modern firmware-based security, making a threat level previously available only to advanced-persistent threats (APT) by state-sponsored groups like the Russian GRU or China's own APT 41 available to anyone. The new UEFI rootkit could represent a real leap forward for cyber-crime in terms of ease of use, scalability, accessibility, persistence, evasion and destruction potential.
UEFI rootkits were once considered to be very rare and specialized threats, but many discoveries in the past few years have shown a completely different scenario. As for BlackLotus, the security community will need to analyze an actual sample of the malware to determine if the advertised features are real, if it's production ready, or if it's just an elaborated scam.