What just happened? Several popular Minecraft mods and plugins hosted on platforms like CurseForge have been infected with malware, so players are advised to refrain from downloading or updating any mods and check for signs of infection on their systems. Players on macOS aren't affected, as the malware is hardcoded for Windows and Linux systems.
One of the reasons Minecraft is still such a popular game after 14 years is that it thrives on player creativity. The modding community that has grown around the game has expanded on the vanilla experience in many ways, from enhancing the visuals to tweaking gameplay mechanics or building entirely new games within its digital sandbox.
However, this popularity is now attracting malicious actors. One of the largest online platforms where gamers can find mods for Minecraft is advising users to stop downloading or updating mods downloaded from its servers. As spotted by ArsTechnica, CurseForge this week reported that hackers had infected several Minecraft projects uploaded to Curseforge and CraftBukkit servers.

This started with hackers compromising a number of developer accounts and injecting malware dubbed Fracturiser into their most popular plugins and mods. Some malicious copies have even made it into mod packs like Better Minecraft, and the earliest reports of infected plugins and mods were made in mid-April.
The makers of Prism Launcher, an open-source Minecraft launcher, believe the infections are widespread and have cataloged the mods and plugins that contain Fracturiser. The list includes Sky Villages, Dungeons Arise, Dungeonz, Better Minecraft mudpack series, Vault Integrations, Skyblock Core, Museum Curator Advanced, Autobroadcast, Create Infernal Expansion Plus, UVision Enhanced, UVision Server, UVision Lite, Additional Weapons+, and Vault Integrations Bug fix.
Those are just the confirmed infected packages from Curseforge. The Fracturiser malware is also embedded in several projects hosted on Bukkit, including Haven Elytra, Display Entity Editor, Simple Harvesting, The Nexus Event Custom Entity Editor, Easy Custom Foods, MCBounties, Ultimate Leveling, Anti Command Spam Bungeecord Support, Hydration, Anti Redstone Crash, No VPNS, Fragment Permission Plugin, Floating Damage, Skelegram, Ultra Swords Mod, and Ultimate Titles Animations Gradient RGB.
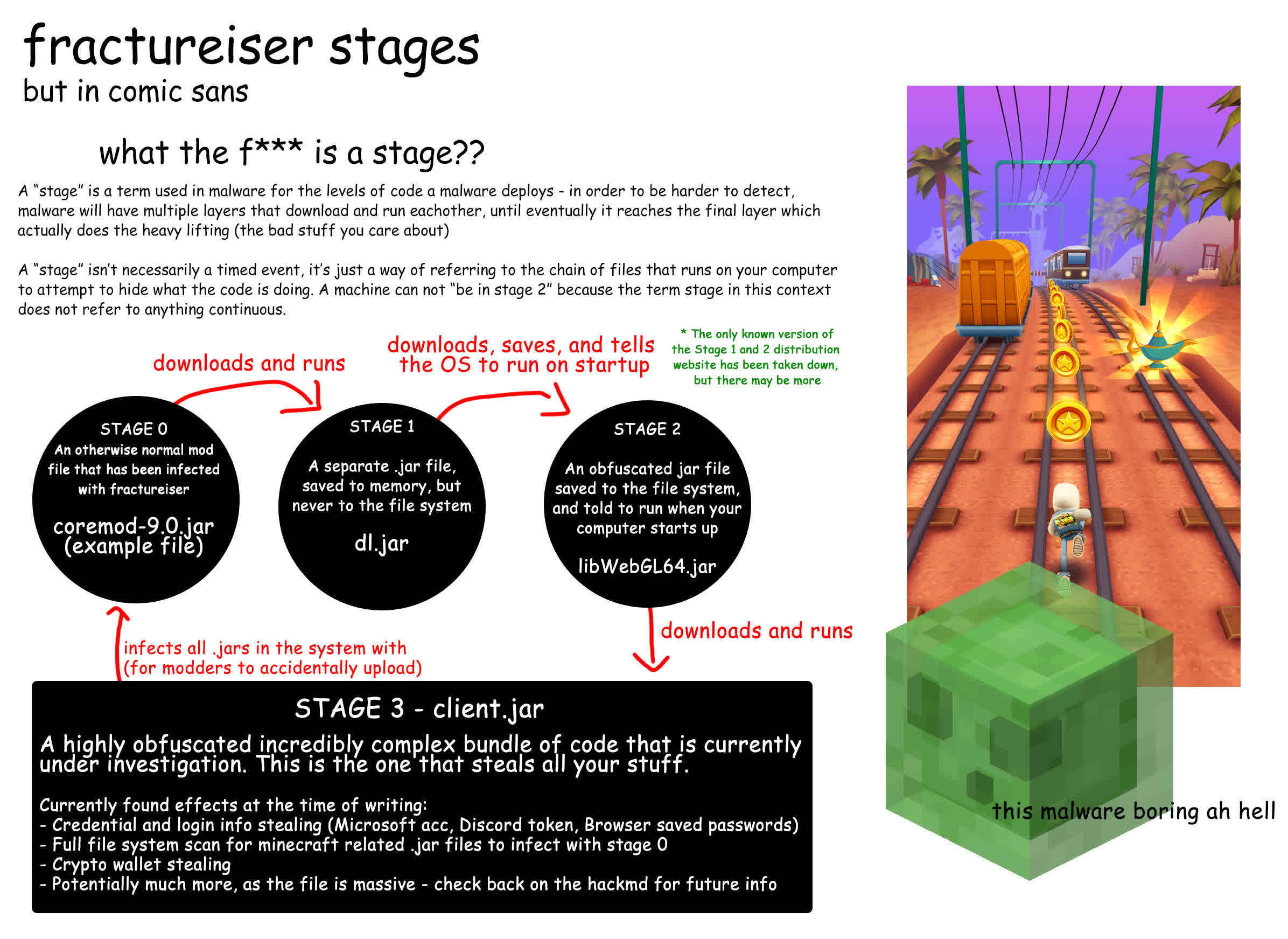
As for the Fracturiser malware, it runs on Windows and Linux systems and works in three stages. The first stage is when someone runs one of the infected mods. The next two stages download files from a command-and-control server and perform additional steps to infect all other Minecraft mods found on the target PC, as well as steal cookies and login information from web browsers, Discord, and Minecraft. The additional malware downloaded by Fracturiser will also replace cryptocurrency addresses in the clipboard.
As of writing this, only a few commercial antivirus solutions can detect Fracturiser files. That said, the folks over at Prism Launcher have already created Windows and Linux scripts you can run to check for infection. Alternatively, you can manually check for signs of the new malware by looking for the following:
- Linux: ~/.config/.data/lib.jar
- Windows: %LOCALAPPDATA%\Microsoft Edge\libWebGL64.jar (or ~\AppData\Local\Microsoft Edge\libWebGL64.jar)
- Make sure to show hidden files when checking
- Yes, "Microsoft Edge" with a space. MicrosoftEdge is the legitimate directory used by actual Edge.
- Also, check the registry for an entry at HKEY_CURRENT_USER:\Software\Microsoft\Windows\CurrentVersion\Run
- Or a shortcut in %appdata%\Microsoft\Windows\Start Menu\Programs\Startup
- All other OSes: Unaffected. The malware is hardcoded for Windows and Linux only. It is possible it will receive an update adding payloads for other OSes in the future.
If you found any signs of infection, you can use two separate tools to clean up your system, as described by Curseforge in this guide. It's also important to change your passwords for apps and services you have used recently on your infected PC.
Masthead credit: Nina Rivas