I saw an alert from my anti-virus just seconds before this screen came on that says " Your computer has been blocked" "The United States Department of Justice" . They want me to get a money pak and pay them $300.00 and get my computer unlocked and prevent further prosecution. It claims it is due to pornography of children under 18. I know this is a scam because there has been no porn viewed at all at anytime. Surely someone knows what this is and how to fix it. Conventional methods are not working. As soon as I reboot, before I can run any virus scan this whole page comes back up blocking everything. I cannot even access the task manager. Someone please help!!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Solved Computer totally locked by virus or malware scam
- Thread starter cableman
- Start date
- Status
- Not open for further replies.
Jay Pfoutz
Posts: 4,279 +49
Hi there!
Farbar Recovery Scan Tool
Download Farbar Recovery Scan Tool and save it to a flash drive.
Depending on your type of system, you will have to select 32-bit or 64-bit accordingly. How do I tell?
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
Farbar Recovery Scan Tool
Download Farbar Recovery Scan Tool and save it to a flash drive.
Depending on your type of system, you will have to select 32-bit or 64-bit accordingly. How do I tell?
Plug the flashdrive into the infected PC.
Enter System Recovery Options.
To enter System Recovery Options from the Advanced Boot Options:
- Restart the computer.
- As soon as the BIOS is loaded begin tapping the F8 key until Advanced Boot Options appears.
- Use the arrow keys to select the Repair your computer menu item.
- Choose your language settings, and then click Next.
- Select the operating system you want to repair, and then click Next.
- Select your user account and click Next.
- Insert the installation disc.
- Restart your computer.
- If prompted, press any key to start Windows from the installation disc. If your computer is not configured to start from a CD or DVD, check your BIOS settings.
- Click Repair your computer.
- Choose your language settings, and then click Next.
- Select the operating system you want to repair, and then click Next.
- Select your user account an click Next.
- Startup Repair
System Restore
Windows Complete PC Restore
Windows Memory Diagnostic Tool
Command Prompt
- Startup Repair
- Select Command Prompt
- In the command window type in notepad and press Enter.
- The notepad opens. Under File menu select Open.
- Select "Computer" and find your flash drive letter and close the notepad.
- In the command window type e:\frst.exe and press Enter
Note: Replace letter e with the drive letter of your flash drive. - The tool will start to run.
- When the tool opens click Yes to the disclaimer.
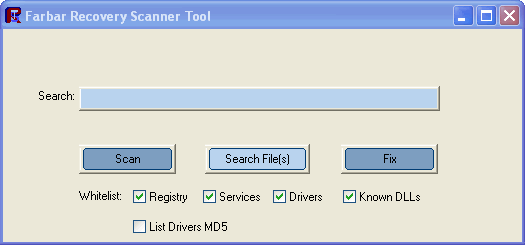
- Place a check next to List Drivers MD5 as well as the default check marks that are already there
- Press Scan button. It will do its scan and save a log on your flash drive.
- Close out of the message after that, then type in the text services.exe in to the "Search:" text box. Then, press the Search file(s) button, just as below:

When done searching, FRST makes a log, Search.txt, on the C:\ drive or on your flash drive. - Type exit in the Command Prompt window and reboot the computer normally
- FRST will make a log (FRST.txt) on the flash drive and also the search.txt logfile, please copy and paste the logs in your reply.
Thank you. I managed to get it to run and here are the results. I am running 32 bit windows xp
Farbar Recovery Scan Tool (x86) Version: 09-01-2013
Ran by User at 2008-04-22 13:38:26
Running from F:\
================== Search: "services.exe" ===================
C:\WINDOWS\system32\services.exe
[2004-08-04 00:56] - [2009-02-06 07:11] - 0110592 ____A (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
C:\WINDOWS\system32\dllcache\services.exe
[2009-08-25 07:27] - [2009-02-06 07:11] - 0110592 ____C (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
C:\WINDOWS\ServicePackFiles\i386\services.exe
[2009-08-25 07:57] - [2008-04-13 20:12] - 0108544 ____N (Microsoft Corporation) 0e776ed5f7cc9f94299e70461b7b8185
C:\WINDOWS\$NtUninstallKB956572_0$\services.exe
[2009-08-25 10:22] - [2004-08-04 00:56] - 0108032 ____C (Microsoft Corporation) c6ce6eec82f187615d1002bb3bb50ed4
C:\WINDOWS\$NtUninstallKB956572$\services.exe
[2009-08-31 22:14] - [2008-04-13 20:12] - 0108544 ____C (Microsoft Corporation) 0e776ed5f7cc9f94299e70461b7b8185
C:\WINDOWS\$NtServicePackUninstall$\services.exe
[2009-08-31 22:03] - [2009-02-06 06:22] - 0110592 ____C (Microsoft Corporation) 4712531ab7a01b7ee059853ca17d39bd
C:\WINDOWS\$hf_mig$\KB956572\SP3QFE\services.exe
[2009-08-25 07:27] - [2009-02-06 07:06] - 0110592 ____A (Microsoft Corporation) 020ceaaedc8eb655b6506b8c70d53bb6
C:\WINDOWS\$hf_mig$\KB956572\SP3GDR\services.exe
[2009-08-25 07:27] - [2009-02-06 07:11] - 0110592 ____A (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
=== End Of Search ===
Farbar Recovery Scan Tool (x86) Version: 09-01-2013
Ran by User at 2008-04-22 13:38:26
Running from F:\
================== Search: "services.exe" ===================
C:\WINDOWS\system32\services.exe
[2004-08-04 00:56] - [2009-02-06 07:11] - 0110592 ____A (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
C:\WINDOWS\system32\dllcache\services.exe
[2009-08-25 07:27] - [2009-02-06 07:11] - 0110592 ____C (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
C:\WINDOWS\ServicePackFiles\i386\services.exe
[2009-08-25 07:57] - [2008-04-13 20:12] - 0108544 ____N (Microsoft Corporation) 0e776ed5f7cc9f94299e70461b7b8185
C:\WINDOWS\$NtUninstallKB956572_0$\services.exe
[2009-08-25 10:22] - [2004-08-04 00:56] - 0108032 ____C (Microsoft Corporation) c6ce6eec82f187615d1002bb3bb50ed4
C:\WINDOWS\$NtUninstallKB956572$\services.exe
[2009-08-31 22:14] - [2008-04-13 20:12] - 0108544 ____C (Microsoft Corporation) 0e776ed5f7cc9f94299e70461b7b8185
C:\WINDOWS\$NtServicePackUninstall$\services.exe
[2009-08-31 22:03] - [2009-02-06 06:22] - 0110592 ____C (Microsoft Corporation) 4712531ab7a01b7ee059853ca17d39bd
C:\WINDOWS\$hf_mig$\KB956572\SP3QFE\services.exe
[2009-08-25 07:27] - [2009-02-06 07:06] - 0110592 ____A (Microsoft Corporation) 020ceaaedc8eb655b6506b8c70d53bb6
C:\WINDOWS\$hf_mig$\KB956572\SP3GDR\services.exe
[2009-08-25 07:27] - [2009-02-06 07:11] - 0110592 ____A (Microsoft Corporation) 65df52f5b8b6e9bbd183505225c37315
=== End Of Search ===
Jay Pfoutz
Posts: 4,279 +49
I didn't know you had Windows XP...here, let's do this:
OTLPE + Farbar Recovery Scan Tool
OTLPE + Farbar Recovery Scan Tool
- Download OTLPENet.exe to your desktop
- Download Farbar Recovery Scan Tool and save it to a flash drive.
- Ensure that you have a blank CD in the drive
- Double click OTLPENet.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
- As the CD needs to detect your hardware and load the operating system, I would recommend a nice cup of tea whilst it loads

- Your system should now display a Reatogo desktop.
- Insert the flash drive with FRST on it
- Locate the flash drive and run FSRT
- The tool will start to run.

- When the tool opens click Yes to disclaimer.
- Press Scan button. It will do its scan and save a log on your flash drive.
- Close out of the message after that, then type in the text services.exe in to the "Search:" text box. Then, press the Search file(s) button, just as below:

When done searching, FRST makes a log, Search.txt, on the C:\ drive or on your flash drive. - Type exit in the Command Prompt window and reboot the computer normally
- FRST will make a log (FRST.txt) on the flash drive and also the search.txt logfile, please copy and paste the logs in your reply.
I am in the process of what you want but keep in mind this virus locks me out of everything. The only way I can get control is to reboot in safe mode and very very quickly open task manager and watch for the "user exe." file to stop from running. If I am not fast enough it will go to the scam screen. This is why we can't see the exe. file that needs deleting because I have already stopped it from runnning by the time I ran the scan. I understand what you want and I will try to get it done. Please understand I have very limited access, spotty at best. I do understand your request and if it does what I think you want it to do then it will record the file we want to delete. Anyway, I am learning so I am doing what you ask at the moment, give me a little time. It locks me out if I am not very quick.
Scan result of Farbar Recovery Scan Tool (FRST) (x86) Version: 09-01-2013
Ran by SYSTEM at 14-01-2013 21:48:39
Running from D:\
Microsoft Windows XP (X86) OS Language: English(US)
The current controlset is ControlSet001
==================== Registry (Whitelisted) ===================
HKLM\...\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup [13594624 2009-03-11] (NVIDIA Corporation)
HKLM\...\Run: [Apoint] C:\Program Files\DellTPad\Apoint.exe [159744 2007-07-02] (Alps Electric Co., Ltd.)
HKU\Administrator\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2010-08-11] (Google Inc.)
HKU\Administrator\...\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe [15360 2008-04-13] (Microsoft Corporation)
HKU\Default User\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\LocalService\...\Run: [Adobe CS Manager] C:\Documents and Settings\LocalService\Application Data\f5e49575-7082-41e2-9a98-12146ef3cef179\feeaefcef.exe [0 2008-04-22] ()
HKU\LocalService\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\NetworkService\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\User\...\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe [15360 2008-04-13] (Microsoft Corporation)
HKU\User\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2010-08-11] (Google Inc.)
HKLM\...\Policies\Explorer\Run: [7546] C:\DOCUME~1\ALLUSE~1\LOCALS~1\Temp\msiaufu.com [x]
Winlogon\Notify\!SASWinLogon: C:\Program Files\SUPERAntiSpyware\SASWINLO.DLL [X]
Winlogon\Notify\WgaLogon: WgaLogon.dll (Microsoft Corporation)
HKLM\...D6A79037F57F\InprocServer32: [Default-fastprox] fastprox.dll ATTENTION! ====> ZeroAccess
Tcpip\Parameters: [DhcpNameServer] 192.168.1.1 205.152.37.23
AppInit_DLLs: c:\progra~1\vaudix\sprote~1.dll
Lsa: [Authentication Packages] msv1_0 nwprovau
==================== Services (Whitelisted) ===================
2 9734BF6A-2DCD-40f0-BAB0-5AAFEEBE1269; C:\Program Files\Roxio\BackOnTrack\Disaster Recovery\SaibSVC.exe [125424 2008-08-01] ()
2 DeviceMonitorService; "C:\Program Files\Motorola Media Link\NServiceEntry.exe" [81920 2010-11-05] (Nero AG)
2 Eventlog; C:\Windows\System32\services.exe [110592 2009-02-06] (Microsoft Corporation)
2 MBAMScheduler; "C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe" [398184 2012-12-14] (Malwarebytes Corporation)
2 MBAMService; "C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe" [682344 2012-12-14] (Malwarebytes Corporation)
2 MotoHelper; C:\Program Files\Motorola\MotoHelper\MotoHelperService.exe [214896 2011-12-06] ()
3 MozillaMaintenance; "C:\Program Files\Mozilla Maintenance Service\maintenanceservice.exe" [115168 2012-10-24] (Mozilla Foundation)
2 NWCWorkstation; C:\Windows\System32\nwwks.dll [65536 2008-04-13] (Microsoft Corporation)
3 Roxio UPnP Renderer 11; "C:\Program Files\Roxio Creator 2009 Ultimate\Digital Home 11\RoxioUPnPRenderer11.exe" [313840 2008-08-13] (Sonic Solutions)
2 Roxio Upnp Server 11; "C:\Program Files\Roxio Creator 2009 Ultimate\Digital Home 11\RoxioUpnpService11.exe" [367088 2008-08-13] (Sonic Solutions)
2 RoxLiveShare11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxLiveShare11.exe" [309744 2008-08-13] (Sonic Solutions)
3 RoxMediaDB11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxMediaDB11.exe" [1124848 2008-08-13] (Sonic Solutions)
2 RoxWatch11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxWatch11.exe" [170480 2008-08-13] (Sonic Solutions)
2 STacSV; C:\WINDOWS\system32\StacSV.exe [94208 2007-05-10] (SigmaTel, Inc.)
3 TuneUp.Defrag; C:\Program Files\TuneUp Utilities 2010\TuneUpDefragService.exe [435016 2011-06-10] (TuneUp Software)
2 TuneUp.UtilitiesSvc; "C:\Program Files\TuneUp Utilities 2010\TuneUpUtilitiesService32.exe" [1021256 2009-10-30] (TuneUp Software)
2 winmgmt; C:\DOCUME~1\ALLUSE~1\ms62AFA401.dat [244224 2008-04-22] ()
2 FontCache3.0.0.0; c:\WINDOWS\Microsoft.NET\Framework\v3.0\WPF\PresentationFontCache.exe [x]
2 JavaQuickStarterService; "C:\Program Files\Java\jre6\bin\jqs.exe" -service -config "C:\Program Files\Java\jre6\lib\deploy\jqs\jqs.conf" [x]
==================== Drivers (Whitelisted) ====================
3 b57w2k; C:\Windows\System32\DRIVERS\b57xp32.sys [160256 2007-03-13] (Broadcom Corporation)
3 BCM43XX; C:\Windows\System32\DRIVERS\bcmwl5.sys [1952512 2009-04-30] (Broadcom Corporation)
3 CCDECODE; C:\Windows\System32\DRIVERS\CCDECODE.sys [17024 2008-04-13] (Microsoft Corporation)
2 fssfltr; C:\Windows\System32\DRIVERS\fssfltr_tdi.sys [54760 2010-04-28] (Microsoft Corporation)
3 HDAudBus; C:\Windows\System32\DRIVERS\HDAudBus.sys [144384 2008-04-13] (Windows (R) Server 2003 DDK provider)
3 HSFHWAZL; C:\Windows\System32\DRIVERS\HSFHWAZL.sys [211200 2007-08-02] (Conexant Systems, Inc.)
3 HSF_DPV; C:\Windows\System32\DRIVERS\HSF_DPV.sys [989952 2007-08-02] (Conexant Systems, Inc.)
3 KLSIENET; C:\Windows\System32\DRIVERS\usb101et.sys [32384 2004-08-03] (KLSI USA, Inc.)
3 MBAMProtector; \??\C:\WINDOWS\system32\drivers\mbam.sys [21104 2012-12-14] (Malwarebytes Corporation)
0 MpFilter; C:\Windows\System32\DRIVERS\MpFilter.sys [193552 2012-08-30] (Microsoft Corporation)
3 NABTSFEC; C:\Windows\System32\DRIVERS\NABTSFEC.sys [85248 2008-04-13] (Microsoft Corporation)
3 NdisIP; C:\Windows\System32\DRIVERS\NdisIP.sys [10880 2008-04-13] (Microsoft Corporation)
3 NPF; C:\Windows\System32\drivers\NPF.sys [50704 2008-04-22] (CACE Technologies, Inc.)
2 NwlnkIpx; C:\Windows\System32\DRIVERS\nwlnkipx.sys [88320 2008-04-13] (Microsoft Corporation)
2 NwlnkNb; C:\Windows\System32\DRIVERS\nwlnknb.sys [63232 2003-07-16] (Microsoft Corporation)
2 NwlnkSpx; C:\Windows\System32\DRIVERS\nwlnkspx.sys [55936 2003-07-16] (Microsoft Corporation)
3 NWRDR; C:\Windows\System32\DRIVERS\nwrdr.sys [163584 2008-04-13] (Microsoft Corporation)
4 RxFilter; C:\Windows\System32\DRIVERS\RxFilter.sys [57328 2008-08-11] (Sonic Solutions)
1 SASDIFSV; \??\C:\Program Files\SUPERAntiSpyware\SASDIFSV.SYS [12872 2010-02-20] (SUPERAdBlocker.com and SUPERAntiSpyware.com)
3 SASENUM; \??\C:\Program Files\SUPERAntiSpyware\SASENUM.SYS [12872 2010-02-20] ( SUPERAdBlocker.com and SUPERAntiSpyware.com)
1 SASKUTIL; \??\C:\Program Files\SUPERAntiSpyware\SASKUTIL.sys [67656 2010-08-27] (SUPERAdBlocker.com and SUPERAntiSpyware.com)
3 SLIP; C:\Windows\System32\DRIVERS\SLIP.sys [11136 2008-04-13] (Microsoft Corporation)
3 STHDA; C:\Windows\System32\drivers\sthda.sys [1222840 2007-05-10] (SigmaTel, Inc.)
3 streamip; C:\Windows\System32\DRIVERS\StreamIP.sys [15232 2008-04-13] (Microsoft Corporation)
3 TuneUpUtilitiesDrv; \??\C:\Program Files\TuneUp Utilities 2010\TuneUpUtilitiesDriver32.sys [10064 2009-10-14] (TuneUp Software)
3 WSTCODEC; C:\Windows\System32\DRIVERS\WSTCODEC.SYS [19200 2008-04-13] (Microsoft Corporation)
4 Abiosdsk; [x]
4 abp480n5; [x]
4 adpu160m; [x]
4 Aha154x; [x]
4 aic78u2; [x]
4 aic78xx; [x]
4 AliIde; [x]
4 amsint; [x]
4 asc; [x]
4 asc3350p; [x]
4 asc3550; [x]
4 Atdisk; [x]
3 BTCFilterService; C:\Windows\System32\DRIVERS\motfilt.sys [x]
4 cd20xrnt; [x]
2 CertPropSvc; [x]
1 Changer; [x]
4 CmdIde; [x]
4 Cpqarray; [x]
4 dac2w2k; [x]
4 dac960nt; [x]
4 dpti2o; [x]
4 hpn; [x]
1 i2omgmt; [x]
4 i2omp; [x]
4 ini910u; [x]
4 IntelIde; [x]
1 lbrtfdc; [x]
3 motccgp; C:\Windows\System32\DRIVERS\motccgp.sys [x]
3 motccgpfl; C:\Windows\System32\DRIVERS\motccgpfl.sys [x]
3 motmodem; C:\Windows\System32\DRIVERS\motmodem.sys [x]
3 MotoSwitchService; C:\Windows\System32\DRIVERS\motswch.sys [x]
3 Motousbnet; C:\Windows\System32\DRIVERS\Motousbnet.sys [x]
3 motusbdevice; C:\Windows\System32\DRIVERS\motusbdevice.sys [x]
4 mraid35x; [x]
1 PCIDump; [x]
3 PDCOMP; [x]
3 PDFRAME; [x]
3 PDRELI; [x]
3 PDRFRAME; [x]
4 perc2; [x]
4 perc2hib; [x]
4 ql1080; [x]
4 Ql10wnt; [x]
4 ql12160; [x]
4 ql1240; [x]
4 ql1280; [x]
4 Simbad; [x]
4 Sparrow; [x]
4 symc810; [x]
4 symc8xx; [x]
4 sym_hi; [x]
4 sym_u3; [x]
4 TosIde; [x]
4 ultra; [x]
4 ViaIde; [x]
3 WDICA; [x]
==================== NetSvcs (Whitelisted) ===================
==================== One Month Created Files and Folders ========
==================== One Month Modified Files and Folders ========
2013-01-14 19:34 - 2008-04-23 11:46 - 127231689 ____A (Igor Pavlov) C:\Documents and Settings\User\Desktop\OTLPENet.exe
==================== Known DLLs (Whitelisted) =================
==================== Bamital & volsnap Check =================
C:\Windows\explorer.exe
[2008-03-27 13:06] - [2008-04-13 19:12] - 1033728 ____A (Microsoft Corporation)
C:\Windows\System32\winlogon.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0507904 ____A (Microsoft Corporation)
C:\Windows\System32\svchost.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0014336 ____A (Microsoft Corporation)
C:\Windows\System32\services.exe
[2004-08-03 23:56] - [2009-02-06 06:11] - 0110592 ____A (Microsoft Corporation)
C:\Windows\System32\User32.dll
[2008-03-27 13:12] - [2008-04-13 19:12] - 0578560 ____A (Microsoft Corporation)
C:\Windows\System32\userinit.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0026112 ____A (Microsoft Corporation)
C:\Windows\System32\Drivers\volsnap.sys
[2004-08-03 22:00] - [2008-04-13 13:41] - 0052352 ____A (Microsoft Corporation)
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
==================== Restore Points (XP) =====================
RP: -> 2008-04-21 21:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP336
RP: -> 2008-04-20 20:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP335
RP: -> 2008-04-19 19:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP334
RP: -> 2008-04-18 18:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP333
RP: -> 2008-04-17 17:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP332
RP: -> 2008-04-16 17:30 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP331
RP: -> 2008-04-15 16:47 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP330
RP: -> 2008-04-14 16:08 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP329
RP: -> 2008-04-13 15:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP328
RP: -> 2008-04-12 14:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP327
RP: -> 2008-04-11 14:11 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP326
==================== Memory info ===========================
Percentage of memory in use: 15%
Total physical RAM: 2045.9 MB
Available physical RAM: 1720.78 MB
Total Pagefile: 1876.58 MB
Available Pagefile: 1795.79 MB
Total Virtual: 2047.88 MB
Available Virtual: 2002.18 MB
==================== Partitions =============================
1 Drive b: (RAMDisk) (Fixed) (Total:0.06 GB) (Free:0.06 GB) NTFS
2 Drive c: () (Fixed) (Total:111.79 GB) (Free:88.75 GB) NTFS ==>[Drive with boot components (Windows XP)]
3 Drive d: () (Removable) (Total:0.95 GB) (Free:0.24 GB) FAT
4 Drive e: (U3 System) (CDROM) (Total:0.01 GB) (Free:0 GB) CDFS
5 Drive x: (ReatogoPE) (CDROM) (Total:0.43 GB) (Free:0 GB) CDFS
Disk ### Status Size Free Dyn Gpt
-------- ---------- ------- ------- --- ---
Disk 0 Online 112 GB 0 B
Partitions of Disk 0:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 112 GB 32 KB
=========================================================
Disk: 0
Partition 1
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 2 C NTFS Partition 112 GB Healthy
=========================================================
==================== End Of Log ============================
Farbar Recovery Scan Tool (x86) Version: 09-01-2013
Ran by SYSTEM at 2013-01-14 21:50:19
Running from D:\
================== Search: "services.exe" ===================
=== End Of Search ===
Ran by SYSTEM at 14-01-2013 21:48:39
Running from D:\
Microsoft Windows XP (X86) OS Language: English(US)
The current controlset is ControlSet001
==================== Registry (Whitelisted) ===================
HKLM\...\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup [13594624 2009-03-11] (NVIDIA Corporation)
HKLM\...\Run: [Apoint] C:\Program Files\DellTPad\Apoint.exe [159744 2007-07-02] (Alps Electric Co., Ltd.)
HKU\Administrator\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2010-08-11] (Google Inc.)
HKU\Administrator\...\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe [15360 2008-04-13] (Microsoft Corporation)
HKU\Default User\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\LocalService\...\Run: [Adobe CS Manager] C:\Documents and Settings\LocalService\Application Data\f5e49575-7082-41e2-9a98-12146ef3cef179\feeaefcef.exe [0 2008-04-22] ()
HKU\LocalService\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\NetworkService\...\RunOnce: [nltide_2] regsvr32 /s /n /I:U shell32 [x]
HKU\User\...\Run: [ctfmon.exe] C:\WINDOWS\system32\ctfmon.exe [15360 2008-04-13] (Microsoft Corporation)
HKU\User\...\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe" [39408 2010-08-11] (Google Inc.)
HKLM\...\Policies\Explorer\Run: [7546] C:\DOCUME~1\ALLUSE~1\LOCALS~1\Temp\msiaufu.com [x]
Winlogon\Notify\!SASWinLogon: C:\Program Files\SUPERAntiSpyware\SASWINLO.DLL [X]
Winlogon\Notify\WgaLogon: WgaLogon.dll (Microsoft Corporation)
HKLM\...D6A79037F57F\InprocServer32: [Default-fastprox] fastprox.dll ATTENTION! ====> ZeroAccess
Tcpip\Parameters: [DhcpNameServer] 192.168.1.1 205.152.37.23
AppInit_DLLs: c:\progra~1\vaudix\sprote~1.dll
Lsa: [Authentication Packages] msv1_0 nwprovau
==================== Services (Whitelisted) ===================
2 9734BF6A-2DCD-40f0-BAB0-5AAFEEBE1269; C:\Program Files\Roxio\BackOnTrack\Disaster Recovery\SaibSVC.exe [125424 2008-08-01] ()
2 DeviceMonitorService; "C:\Program Files\Motorola Media Link\NServiceEntry.exe" [81920 2010-11-05] (Nero AG)
2 Eventlog; C:\Windows\System32\services.exe [110592 2009-02-06] (Microsoft Corporation)
2 MBAMScheduler; "C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe" [398184 2012-12-14] (Malwarebytes Corporation)
2 MBAMService; "C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe" [682344 2012-12-14] (Malwarebytes Corporation)
2 MotoHelper; C:\Program Files\Motorola\MotoHelper\MotoHelperService.exe [214896 2011-12-06] ()
3 MozillaMaintenance; "C:\Program Files\Mozilla Maintenance Service\maintenanceservice.exe" [115168 2012-10-24] (Mozilla Foundation)
2 NWCWorkstation; C:\Windows\System32\nwwks.dll [65536 2008-04-13] (Microsoft Corporation)
3 Roxio UPnP Renderer 11; "C:\Program Files\Roxio Creator 2009 Ultimate\Digital Home 11\RoxioUPnPRenderer11.exe" [313840 2008-08-13] (Sonic Solutions)
2 Roxio Upnp Server 11; "C:\Program Files\Roxio Creator 2009 Ultimate\Digital Home 11\RoxioUpnpService11.exe" [367088 2008-08-13] (Sonic Solutions)
2 RoxLiveShare11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxLiveShare11.exe" [309744 2008-08-13] (Sonic Solutions)
3 RoxMediaDB11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxMediaDB11.exe" [1124848 2008-08-13] (Sonic Solutions)
2 RoxWatch11; "C:\Program Files\Common Files\Roxio Shared\11.0\SharedCOM\RoxWatch11.exe" [170480 2008-08-13] (Sonic Solutions)
2 STacSV; C:\WINDOWS\system32\StacSV.exe [94208 2007-05-10] (SigmaTel, Inc.)
3 TuneUp.Defrag; C:\Program Files\TuneUp Utilities 2010\TuneUpDefragService.exe [435016 2011-06-10] (TuneUp Software)
2 TuneUp.UtilitiesSvc; "C:\Program Files\TuneUp Utilities 2010\TuneUpUtilitiesService32.exe" [1021256 2009-10-30] (TuneUp Software)
2 winmgmt; C:\DOCUME~1\ALLUSE~1\ms62AFA401.dat [244224 2008-04-22] ()
2 FontCache3.0.0.0; c:\WINDOWS\Microsoft.NET\Framework\v3.0\WPF\PresentationFontCache.exe [x]
2 JavaQuickStarterService; "C:\Program Files\Java\jre6\bin\jqs.exe" -service -config "C:\Program Files\Java\jre6\lib\deploy\jqs\jqs.conf" [x]
==================== Drivers (Whitelisted) ====================
3 b57w2k; C:\Windows\System32\DRIVERS\b57xp32.sys [160256 2007-03-13] (Broadcom Corporation)
3 BCM43XX; C:\Windows\System32\DRIVERS\bcmwl5.sys [1952512 2009-04-30] (Broadcom Corporation)
3 CCDECODE; C:\Windows\System32\DRIVERS\CCDECODE.sys [17024 2008-04-13] (Microsoft Corporation)
2 fssfltr; C:\Windows\System32\DRIVERS\fssfltr_tdi.sys [54760 2010-04-28] (Microsoft Corporation)
3 HDAudBus; C:\Windows\System32\DRIVERS\HDAudBus.sys [144384 2008-04-13] (Windows (R) Server 2003 DDK provider)
3 HSFHWAZL; C:\Windows\System32\DRIVERS\HSFHWAZL.sys [211200 2007-08-02] (Conexant Systems, Inc.)
3 HSF_DPV; C:\Windows\System32\DRIVERS\HSF_DPV.sys [989952 2007-08-02] (Conexant Systems, Inc.)
3 KLSIENET; C:\Windows\System32\DRIVERS\usb101et.sys [32384 2004-08-03] (KLSI USA, Inc.)
3 MBAMProtector; \??\C:\WINDOWS\system32\drivers\mbam.sys [21104 2012-12-14] (Malwarebytes Corporation)
0 MpFilter; C:\Windows\System32\DRIVERS\MpFilter.sys [193552 2012-08-30] (Microsoft Corporation)
3 NABTSFEC; C:\Windows\System32\DRIVERS\NABTSFEC.sys [85248 2008-04-13] (Microsoft Corporation)
3 NdisIP; C:\Windows\System32\DRIVERS\NdisIP.sys [10880 2008-04-13] (Microsoft Corporation)
3 NPF; C:\Windows\System32\drivers\NPF.sys [50704 2008-04-22] (CACE Technologies, Inc.)
2 NwlnkIpx; C:\Windows\System32\DRIVERS\nwlnkipx.sys [88320 2008-04-13] (Microsoft Corporation)
2 NwlnkNb; C:\Windows\System32\DRIVERS\nwlnknb.sys [63232 2003-07-16] (Microsoft Corporation)
2 NwlnkSpx; C:\Windows\System32\DRIVERS\nwlnkspx.sys [55936 2003-07-16] (Microsoft Corporation)
3 NWRDR; C:\Windows\System32\DRIVERS\nwrdr.sys [163584 2008-04-13] (Microsoft Corporation)
4 RxFilter; C:\Windows\System32\DRIVERS\RxFilter.sys [57328 2008-08-11] (Sonic Solutions)
1 SASDIFSV; \??\C:\Program Files\SUPERAntiSpyware\SASDIFSV.SYS [12872 2010-02-20] (SUPERAdBlocker.com and SUPERAntiSpyware.com)
3 SASENUM; \??\C:\Program Files\SUPERAntiSpyware\SASENUM.SYS [12872 2010-02-20] ( SUPERAdBlocker.com and SUPERAntiSpyware.com)
1 SASKUTIL; \??\C:\Program Files\SUPERAntiSpyware\SASKUTIL.sys [67656 2010-08-27] (SUPERAdBlocker.com and SUPERAntiSpyware.com)
3 SLIP; C:\Windows\System32\DRIVERS\SLIP.sys [11136 2008-04-13] (Microsoft Corporation)
3 STHDA; C:\Windows\System32\drivers\sthda.sys [1222840 2007-05-10] (SigmaTel, Inc.)
3 streamip; C:\Windows\System32\DRIVERS\StreamIP.sys [15232 2008-04-13] (Microsoft Corporation)
3 TuneUpUtilitiesDrv; \??\C:\Program Files\TuneUp Utilities 2010\TuneUpUtilitiesDriver32.sys [10064 2009-10-14] (TuneUp Software)
3 WSTCODEC; C:\Windows\System32\DRIVERS\WSTCODEC.SYS [19200 2008-04-13] (Microsoft Corporation)
4 Abiosdsk; [x]
4 abp480n5; [x]
4 adpu160m; [x]
4 Aha154x; [x]
4 aic78u2; [x]
4 aic78xx; [x]
4 AliIde; [x]
4 amsint; [x]
4 asc; [x]
4 asc3350p; [x]
4 asc3550; [x]
4 Atdisk; [x]
3 BTCFilterService; C:\Windows\System32\DRIVERS\motfilt.sys [x]
4 cd20xrnt; [x]
2 CertPropSvc; [x]
1 Changer; [x]
4 CmdIde; [x]
4 Cpqarray; [x]
4 dac2w2k; [x]
4 dac960nt; [x]
4 dpti2o; [x]
4 hpn; [x]
1 i2omgmt; [x]
4 i2omp; [x]
4 ini910u; [x]
4 IntelIde; [x]
1 lbrtfdc; [x]
3 motccgp; C:\Windows\System32\DRIVERS\motccgp.sys [x]
3 motccgpfl; C:\Windows\System32\DRIVERS\motccgpfl.sys [x]
3 motmodem; C:\Windows\System32\DRIVERS\motmodem.sys [x]
3 MotoSwitchService; C:\Windows\System32\DRIVERS\motswch.sys [x]
3 Motousbnet; C:\Windows\System32\DRIVERS\Motousbnet.sys [x]
3 motusbdevice; C:\Windows\System32\DRIVERS\motusbdevice.sys [x]
4 mraid35x; [x]
1 PCIDump; [x]
3 PDCOMP; [x]
3 PDFRAME; [x]
3 PDRELI; [x]
3 PDRFRAME; [x]
4 perc2; [x]
4 perc2hib; [x]
4 ql1080; [x]
4 Ql10wnt; [x]
4 ql12160; [x]
4 ql1240; [x]
4 ql1280; [x]
4 Simbad; [x]
4 Sparrow; [x]
4 symc810; [x]
4 symc8xx; [x]
4 sym_hi; [x]
4 sym_u3; [x]
4 TosIde; [x]
4 ultra; [x]
4 ViaIde; [x]
3 WDICA; [x]
==================== NetSvcs (Whitelisted) ===================
==================== One Month Created Files and Folders ========
==================== One Month Modified Files and Folders ========
2013-01-14 19:34 - 2008-04-23 11:46 - 127231689 ____A (Igor Pavlov) C:\Documents and Settings\User\Desktop\OTLPENet.exe
==================== Known DLLs (Whitelisted) =================
==================== Bamital & volsnap Check =================
C:\Windows\explorer.exe
[2008-03-27 13:06] - [2008-04-13 19:12] - 1033728 ____A (Microsoft Corporation)
C:\Windows\System32\winlogon.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0507904 ____A (Microsoft Corporation)
C:\Windows\System32\svchost.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0014336 ____A (Microsoft Corporation)
C:\Windows\System32\services.exe
[2004-08-03 23:56] - [2009-02-06 06:11] - 0110592 ____A (Microsoft Corporation)
C:\Windows\System32\User32.dll
[2008-03-27 13:12] - [2008-04-13 19:12] - 0578560 ____A (Microsoft Corporation)
C:\Windows\System32\userinit.exe
[2004-08-03 23:56] - [2008-04-13 19:12] - 0026112 ____A (Microsoft Corporation)
C:\Windows\System32\Drivers\volsnap.sys
[2004-08-03 22:00] - [2008-04-13 13:41] - 0052352 ____A (Microsoft Corporation)
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
==================== Restore Points (XP) =====================
RP: -> 2008-04-21 21:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP336
RP: -> 2008-04-20 20:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP335
RP: -> 2008-04-19 19:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP334
RP: -> 2008-04-18 18:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP333
RP: -> 2008-04-17 17:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP332
RP: -> 2008-04-16 17:30 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP331
RP: -> 2008-04-15 16:47 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP330
RP: -> 2008-04-14 16:08 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP329
RP: -> 2008-04-13 15:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP328
RP: -> 2008-04-12 14:46 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP327
RP: -> 2008-04-11 14:11 - 024576 _restore{27B4202B-6C03-47B2-A5C8-B45D68649848}\RP326
==================== Memory info ===========================
Percentage of memory in use: 15%
Total physical RAM: 2045.9 MB
Available physical RAM: 1720.78 MB
Total Pagefile: 1876.58 MB
Available Pagefile: 1795.79 MB
Total Virtual: 2047.88 MB
Available Virtual: 2002.18 MB
==================== Partitions =============================
1 Drive b: (RAMDisk) (Fixed) (Total:0.06 GB) (Free:0.06 GB) NTFS
2 Drive c: () (Fixed) (Total:111.79 GB) (Free:88.75 GB) NTFS ==>[Drive with boot components (Windows XP)]
3 Drive d: () (Removable) (Total:0.95 GB) (Free:0.24 GB) FAT
4 Drive e: (U3 System) (CDROM) (Total:0.01 GB) (Free:0 GB) CDFS
5 Drive x: (ReatogoPE) (CDROM) (Total:0.43 GB) (Free:0 GB) CDFS
Disk ### Status Size Free Dyn Gpt
-------- ---------- ------- ------- --- ---
Disk 0 Online 112 GB 0 B
Partitions of Disk 0:
===============
Partition ### Type Size Offset
------------- ---------------- ------- -------
Partition 1 Primary 112 GB 32 KB
=========================================================
Disk: 0
Partition 1
Type : 07
Hidden: No
Active: Yes
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
* Volume 2 C NTFS Partition 112 GB Healthy
=========================================================
==================== End Of Log ============================
Farbar Recovery Scan Tool (x86) Version: 09-01-2013
Ran by SYSTEM at 2013-01-14 21:50:19
Running from D:\
================== Search: "services.exe" ===================
=== End Of Search ===
Jay Pfoutz
Posts: 4,279 +49
FRST Fixlist
Please download attached fixlist.txt below, and save it to your flash drive in the same location as FRST.exe. Make sure it maintains the same name, otherwise the fix will fail.
NOTICE: This script was written specifically for this user, for use on this particular machine. Running this on another machine may cause damage to your operating system
Now, please enter OTLPE as earlier...
Run FRST and press the Fix button just once and wait.
The tool will make a log on the flashdrive (Fixlog.txt) please post it to your reply.
Now restart, let it boot normally and tell me how it went.
Good job so far.
Please download attached fixlist.txt below, and save it to your flash drive in the same location as FRST.exe. Make sure it maintains the same name, otherwise the fix will fail.
NOTICE: This script was written specifically for this user, for use on this particular machine. Running this on another machine may cause damage to your operating system
Now, please enter OTLPE as earlier...
Run FRST and press the Fix button just once and wait.
The tool will make a log on the flashdrive (Fixlog.txt) please post it to your reply.
Now restart, let it boot normally and tell me how it went.
Good job so far.
Attachments
You are amazing. I know that I am an amateur at these things but so far it seems to be fixed. I have fixed a couple of small virus's before on my own but this one was terrible. Thank you again and here is the log just in case something is still not right.
Fix result of Farbar Recovery Tool (FRST written by Farbar) (x86) Version: 09-01-2013
Ran by SYSTEM at 2013-01-15 14:39:09 Run:1
Running from D:\
==============================================
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InprocServer32\\Default value was restored successfully .
[HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}] should be deleted in normal mode (if present).
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\\7546 Value not found.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\\AppInit_DLLs Value was restored successfully .
winmgmt service deleted successfully.
==== End of Fixlog ====
Fix result of Farbar Recovery Tool (FRST written by Farbar) (x86) Version: 09-01-2013
Ran by SYSTEM at 2013-01-15 14:39:09 Run:1
Running from D:\
==============================================
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InprocServer32\\Default value was restored successfully .
[HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}] should be deleted in normal mode (if present).
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\\7546 Value not found.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\\AppInit_DLLs Value was restored successfully .
winmgmt service deleted successfully.
==== End of Fixlog ====
Jay Pfoutz
Posts: 4,279 +49
Excellent work!
Let's do the following in Normal Mode to make sure we get all of the crap out of the system.
ComboFix scan
Please download ComboFix
 by sUBs
by sUBs
From TechSpot
Direct Link (alternative)
Please save the file to your Desktop.
Important information about ComboFix
After the download:
Safe Mode:
If you still cannot get ComboFix to run, try booting into Safe Mode, and run it there.
(To boot into Safe Mode, tap F8 after BIOS, and just before the Windows
logo appears. A list of options will appear, select "Safe Mode.")
Re-downloading:
If this doesn't work either, try the same method (above method), but try to download it again, except name
ComboFix.exe to iexplore.exe, explorer.exe, or winlogon.exe.
Malware is known for blocking all "user" processes, except for its whitelist of system important processes such as iexplore.exe, explorer.exe, winlogon.exe.
NOTE: If you encounter a message "illegal operation attempted on registry key that has been marked for deletion" and no programs will run - please just reboot and that will resolve that error.
Let's do the following in Normal Mode to make sure we get all of the crap out of the system.
ComboFix scan
Please download ComboFix

From TechSpot
Direct Link (alternative)
Please save the file to your Desktop.
Important information about ComboFix
After the download:
- Close any open browsers.
- Very Important: Temporarily disable your anti-virus, script blocking and any anti-malware real-time protection before performing a scan. They can interfere with ComboFix or remove some of its embedded files which may cause "unpredictable results". Please visit here if you don't know how.
- WARNING: Combofix will disconnect your machine from the Internet as soon as it starts
- Please do not attempt to re-connect your machine back to the Internet until ComboFix has completely finished.
- If there is no Internet connection after running ComboFix, then restart your computer to restore back your connection.
- Double click on ComboFix.exe & follow the prompts.
- When ComboFix finishes, it will produce a report for you.
- Please post the report, which will launch or be found at "C:\Combo-Fix.txt" in your next reply.
Safe Mode:
If you still cannot get ComboFix to run, try booting into Safe Mode, and run it there.
(To boot into Safe Mode, tap F8 after BIOS, and just before the Windows
logo appears. A list of options will appear, select "Safe Mode.")
Re-downloading:
If this doesn't work either, try the same method (above method), but try to download it again, except name
ComboFix.exe to iexplore.exe, explorer.exe, or winlogon.exe.
Malware is known for blocking all "user" processes, except for its whitelist of system important processes such as iexplore.exe, explorer.exe, winlogon.exe.
NOTE: If you encounter a message "illegal operation attempted on registry key that has been marked for deletion" and no programs will run - please just reboot and that will resolve that error.
Thank you again. I have been using the laptop normally but a little vervously since this is the worst mal-ware I have ever run across. I think it is obvious that it is a scam to get money out of naive people and after reading info provide from a google search it seems that a lot of people actually paid the money and were still left with a locked up computer. Kinda makes you wonder just what they might have been doing online to feel guilty about doesn't it? Thanks again with all my heart, I would send you a contribution but I don't have it right now. Tell me how to donate some money that will actually get to you and compensate you and I will send some when I can in a week or so because you didn't pressure me into money for helping only let it be known that compensation was available. That tells me you are a decent man who will help even expecting nothing in return. All seems to work ok so far. please tekk me if the log says something else needs doing. I am going to put bit defender on all my computers. It seems to be the highest rated product in it's dept. Thanks again. I am using Avast for now and it works will enough but not for these really nasty virus's
Jay Pfoutz
Posts: 4,279 +49
Thanks for the compliment. See my signature below, which provides a blue link to my donation page. That will allow it to go straight to my private account at PayPal.com.
Do you want to check for any remnants? A couple more scans can be in order. It's your choice...
Do you want to check for any remnants? A couple more scans can be in order. It's your choice...
I have been running anti-virus scans and mal-ware scana out the wazoo all night I think we cleaned that up and much more. I won't forget you next week when I get paid. I am going to have to start another thread in a different section. It seems that my HP laptoop is too bad to repair and what I need is some really good software to pull out my Microsoft word 2007 key so when I re-install it with an OEM disc I will still get full function. I already have the key for Windows 7 pro on the COA sticker, I really wanted 7 ultimate but I guess I will have to settle for pro until I can upgrade. Anyway if you see my post in that area and want to answer please do because you turned one of my worst nightmares into not so bad a job. I am going to install bit defender on all my computers. It seems to have the highest ratings now. Thanks again and I won't forget you you, you just have to give me to about the 27th. of this month. I am a sub-contractor and my pay schedule is crazy.
Jay Pfoutz
Posts: 4,279 +49
- Status
- Not open for further replies.
Similar threads
- Replies
- 17
- Views
- 914
- Replies
- 30
- Views
- 8K
Latest posts
-
Sound comes 1 sec delayed in the beginnig
- hdeveci replied
-
These credit cards feature OLEDs that light up upon payment
- techstrike replied
-
Unable to connect WI-FI with alexa app setup?
- Peter wilison replied
-
Fallout 4 mod downloads skyrocket following launch of TV series
- Farkinell replied
-
TechSpot is dedicated to computer enthusiasts and power users.
Ask a question and give support.
Join the community here, it only takes a minute.