In brief: The infamous Emotet botnet is once again trying inventive tactics to deliver the infection and turn users' PCs into malware-spreading zombies. A new phishing campaign overlaps with the upcoming tax season in the US as it attempts to lure users into opening a fake document to install the malware.
Emotet is one of the most widespread infections in recent years - a dangerous botnet operation designed to steal users' information while simultaneously spreading third-party malicious programs. The malware usually tries to compromise a victim's PC through a carefully orchestrated phishing campaign, delivering seemingly legit emails with malicious attachments disguised as Office documents.
The latest phishing campaign is focused on spreading fake Form W-9 attachments, just in time for tax day when income tax returns need to be submitted to the IRS. The malicious email is seemingly sent by the IRS and private companies, while the attached Zip file contains a Word document inflated to over 500 megabytes.
As no legit Word document could ever reach that kind of size, the attachment is clearly a fake. Furthermore, the malicious nature of the document is fully exposed when a user tries to open it but Word says it has blocked macros from running on the system.
Microsoft is now blocking macros by default, as the technology has known widespread abuse by both Emotet and other malicious campaigns targeting Windows PCs.
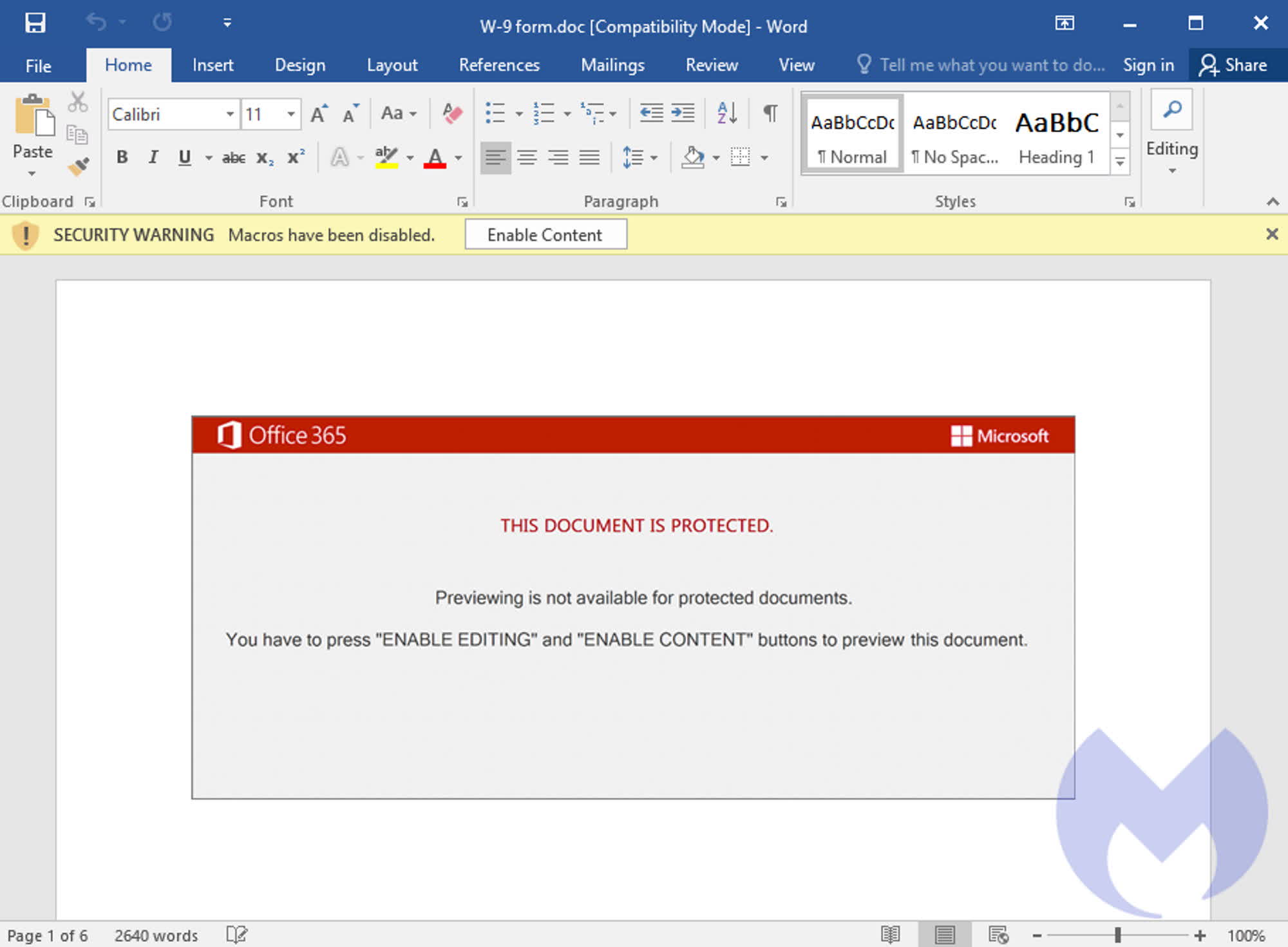
According to researchers at Intel's Unit 42, Emotet is trying to bypass the default macro blocking mechanism of Word – which should deter even the most oblivious user out there – by sending OneNote attachments instead. Once opened, the document says it is "protected" and the user has to double-click the "View" button to open it.
The View button is just a façade though, as the double click is needed to run a Visual Basic script embedded within. Once executed, the script will download and install the Emotet DLL payload with the legit regsvr32.exe system tool. OneNote will show a warning about the potentially malicious nature of the VB script. Needless to say, many oblivious users will happily avoid paying attention to said warning and will launch the script anyway.
Once executed, the Emotet malicious library is designed to quietly run in the background and steal email addresses, contacts, and other useful data. The malware will then wait for further orders coming from the command and control center, which in Emotet's case usually means downloading and running additional or third-party malware samples.
W-9 and other tax form attachments usually come in PDF format, so users should avoid opening Word, OneNote or other document types when they aren't 100 percent sure the message is legit.
https://www.techspot.com/news/98085-emotet-phishing-campaign-masquerading-w-9-tax-form.html