In context: Security firm ESET discovered the first UEFI rootkit that had been used in the wild back in 2018. This type of persistent threat used to be the subject of theoretical discussions among security researchers, but over the past years, it's become clear that it's a lot more common than previously thought, despite being relatively hard to develop.
This week, Kaspersky researchers revealed a new firmware rootkit dubbed "CosmicStrand," which is believed to be the work of an unknown group of Chinese malicious actors.
Researchers explain that the rootkit was discovered in firmware images of several Asus and Gigabyte motherboards equipped with an Intel H81 chipset, one of the longest-living Haswell-era chipsets that was finally discontinued in 2020.
Since UEFI firmware is the first piece of code that runs when you turn a computer on, this makes CosmicStrand particularly hard to remove compared to other types of malware. Firmware rootkits are also harder to detect and pave the way for hackers to install additional malware on a target system.
Simply wiping the storage in your PC won't remove the infection, and neither will replacing storage devices altogether. UEFI is essentially a small operating system that lives inside a non-volatile memory chip, usually soldered on the motherboard. This means that removing CosmicStrand requires special tools to reimage the flash chip while the PC is powered off. Anything else would leave your computer in an infected state.
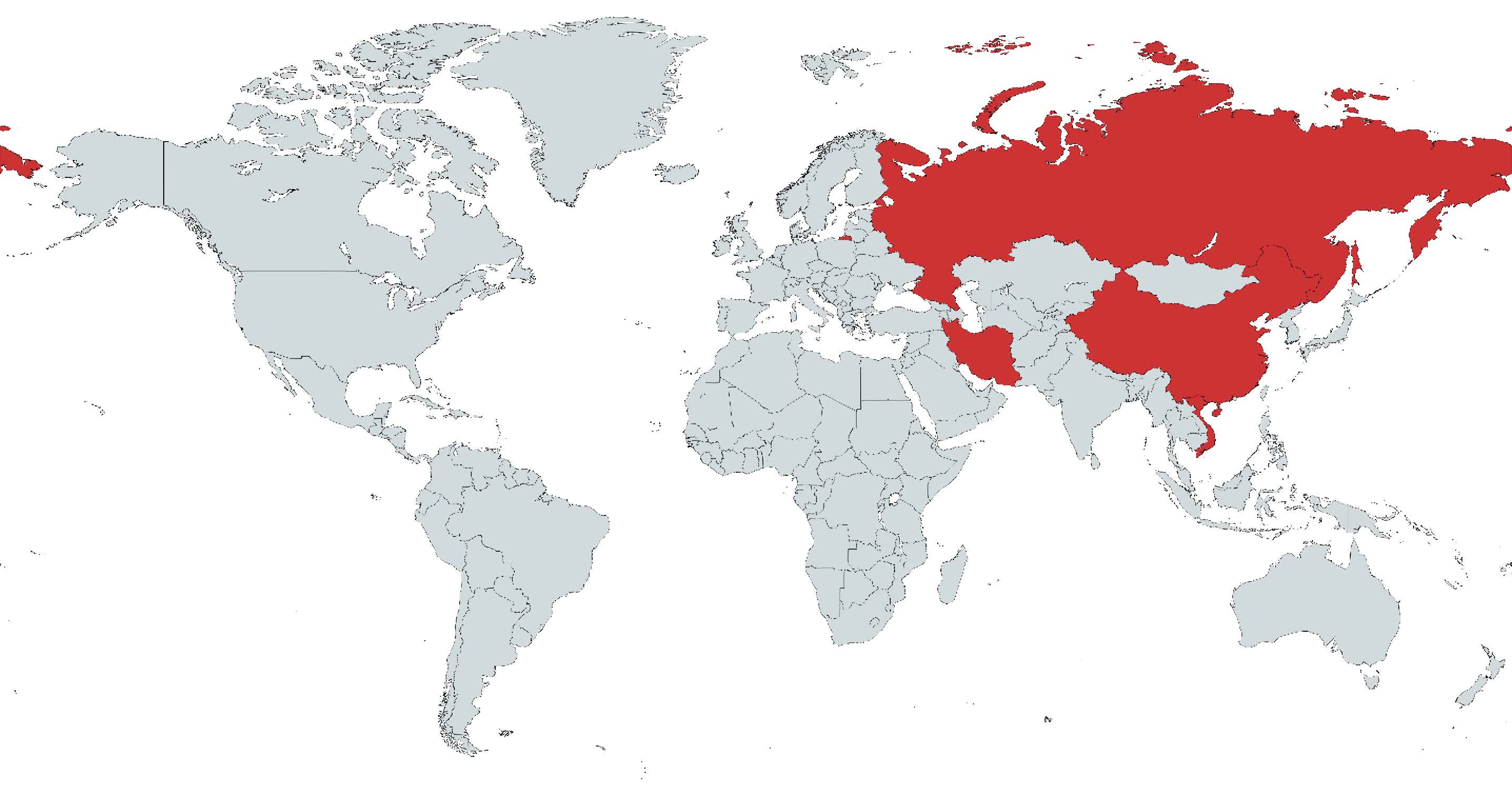
So far, it appears only Windows systems in countries like Russia, China, Iran, and Vietnam have been compromised. However, the UEFI implant has been used in the wild since late 2016, which raises the possibility that this type of infection is more common than previously assumed.
Back in 2017, security firm Qihoo360 discovered what could have been an early variant of CosmicStrand. In more recent years, researchers found additional UEFI rootkits such as MosaicRegressor, FinSpy, ESpecter, and MoonBounce.
As for CosmicStrand, it's a very potent malware that's less than 100 kilobytes in size. Not much is known about how it ended up on the target systems, but the way it works is simple. First, it infects the boot process by setting so-called "hooks" into certain points of the execution flow, thus adding the functionality the attacker needs to modify the Windows kernel loader before it is executed.
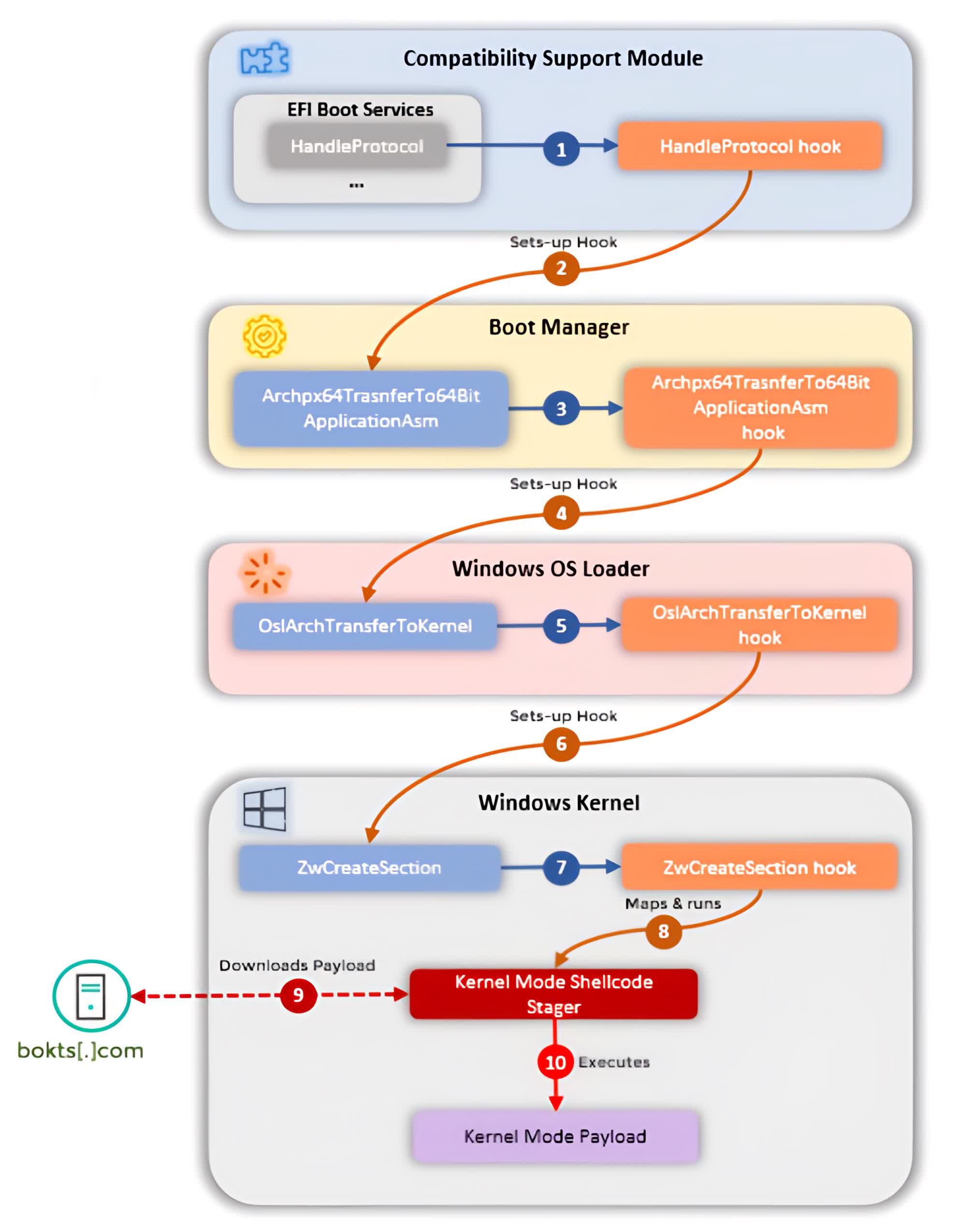
From there, the attackers can install another hook in the form of a function in the Windows kernel that is called in a subsequent boot process. This function deploys a shellcode in memory that can contact a command-and-control server and download additional malware on the infected PC.
CosmicStrand can also disable kernel protections like PatchGuard (known as Microsoft Kernel Patch Protection), which is a crucial Windows security feature. There are also some similarities in terms of code patterns between CosmicStrand and malware related to the MyKings botnet, which has been used to deploy cryptominers on victims' computers.
Kaspersky researchers are worried that CosmicStrand may be one of many firmware rootkits that have managed to stay hidden for years. They note that "the multiple rootkits discovered so far evidence a blind spot in our industry that needs to be addressed sooner rather than later."
https://www.techspot.com/news/95425-years-gigabyte-asus-motherboards-carried-uefi-malware.html