Leeky
Posts: 3,357 +116
Kaspersky security analysts have identified another cyber-threat (PDF) targeting the Middle East as part of ongoing research into Flame. Named Gauss, it displays all the hallmarks of being part of the same family as Flame (Stuxnet, Duqu) and is compromising financial account and log in information from computer users accessing Lebanese banks, as well as reporting hardware configurations to its creators.
"Gauss is a nation state sponsored banking Trojan which carries a warhead of unknown designation. Besides stealing various kinds of data from infected Windows machines, it also includes an unknown, encrypted payload which is activated on certain specific system configurations," said Kaspersky.
Kaspersky added that Gauss was likely created mid-2011 and deployed last September. Although it appears the command and control servers went silent in June, the worm sits dormant awaiting contact from them in the meantime.
Its infection mechanism is not yet fully known (the same is true of Flame), though analysts think both worms could potentially use the same methods of infection. Research so far suggests there is no self-spreading aspect to Gauss.
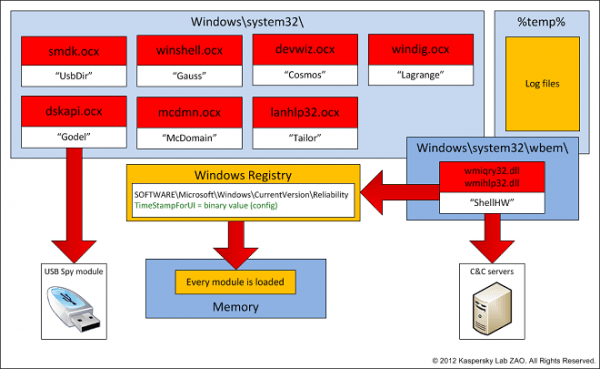
The new worm uses the same Windows shortcut (CVE-2010-2568) vulnerability exploited by Flame and Stuxnet, and infects USB memory sticks. Further investigation reveals the worm will run 30 times on the USB stick before completely removing all traces of itself.
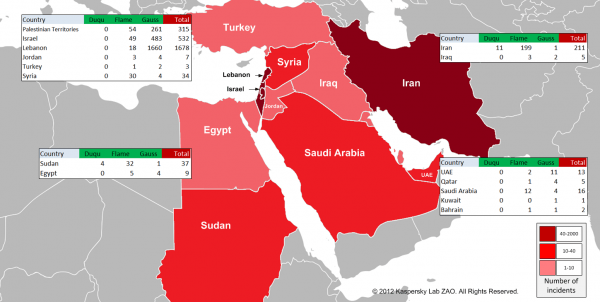
Analysis shows it has infected thousands of Lebanese computers and targets the country's financial institutions, specifically the Bank of Beirut, EBLF, BlomBank, BybiosBank, FransaBank, Credit Libanais, PayPal and Citibank. Other Middle Eastern countries and Israel also appear to have a limited number of infections.
Kaspersky say it's also capable of intercepting cookies and browsing activity, stealing account credentials for email and chat accounts and harvesting hardware configurations including BIOS details, which is reported back to command servers. It is unconfirmed whether the worm has been used to steal money from infected accounts.
More alarmingly however, it also appears to have a secret payload, which due to heavy encryption has eluded researchers. Kaspersky is even calling for world-class cryptographers to help break it, asking anyone interested in the challenge to contact them by email: theflame@kaspersky.com.
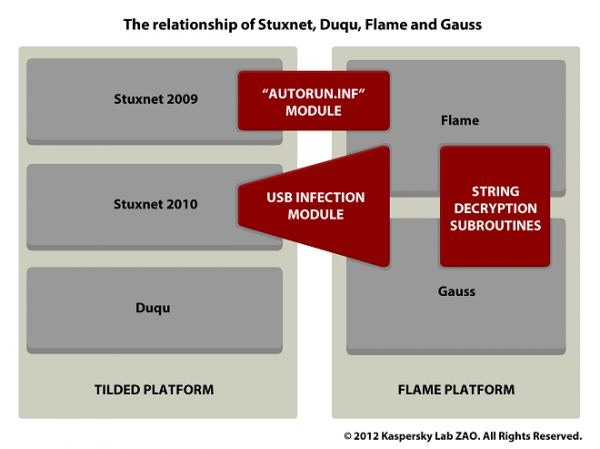
"After looking at Stuxnet, Duqu and Flame, we can say with a high degree of certainty that Gauss comes from the same factory or factories. All these attack toolkits represent the high end of nation-state sponsored cyber-espionage and cyberwar operations," Kaspersky said.