
The many goodies arriving with iOS 12 may still be a ways away, but that doesn't mean users have nothing to look forward to in the meantime. On the contrary; the company today released the latest version of iOS 11,11.4.1.
While the update doesn't bring any particularly exciting or fun features of note, it does add a pretty nifty new security feature.
The feature, dubbed USB Restricted Mode, is designed to prevent third parties from gaining access to your device by using lightning-connected gadgets to crack your passcode and bypass Apple's safety mechanisms.
Though Apple doesn't explicitly say what this feature is for, it seems likely it's primary purpose is to prevent law enforcement from getting their hands on your data.
If you think back to the tragic San Bernardino shooting incident of 2015, you might recall that Apple refused to build a software backdoor for the FBI to access one of the killers' phones, fearing that doing so would set a dangerous legal precedent.
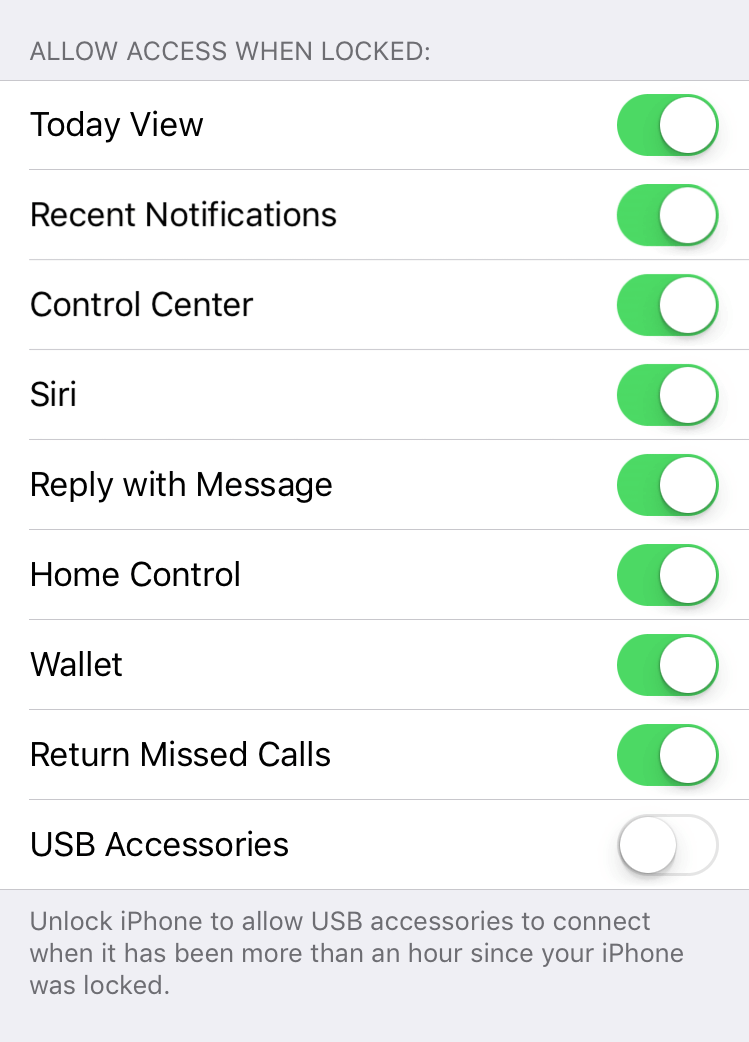
At any rate, USB Restricted Mode functions by preventing USB devices from connecting to your iPhone or iPad, and yes, that includes Lightning-powered accessories. USB Restricted Mode will be optional, of course; users can enable or disable it via their device's settings menu.
It's also worth noting that, even with the mode enabled, you won't need to go back to your settings menu every time you want to connect your favorite accessory to your device. Users can optionally choose to toggle a setting that only enables the feature after an hour has passed since their last device lock.
Although the USB Protected Mode feature is likely to cause additional friction between law enforcement and Apple down the line, it's nice to see a tech company take their users' privacy seriously - even in the face of government pressure.
https://www.techspot.com/news/75420-ios-1141-usb-restricted-mode-block-law-enforcement.html