
Microsoft plans to put more of an emphasis on the security of its Windows users moving forward, via the newly-announced "Secured-core PC" initiative. The initiative aims to offer Windows customers a better form of protection against "targeted firmware" attacks.
These attacks, according to Microsoft, are becoming more common in recent years. This is largely due to the ever-improving security features built into operating systems and their "connected services." Better security means more challenges for hackers to overcome, and reduced incentive for them to attempt to break into a system using software vulnerabilities; thus leading them to focus on firmware instead.
To address the growing threat that firmware-based attacks present, Microsoft has partnered up with various PC manufacturing and silicon partners to produce the secured-core PC defense. This defense's primary component is "System Guard Secure Launch," a device requirement that protects a PC's boot process from firmware attacks.
Microsoft's full explanation of how this concept works is quite technical in nature, but here's a summary, in the company's own words:
System Guard uses the Dynamic Root of Trust for Measurement (DRTM) capabilities that are built into the latest silicon from AMD, Intel, and Qualcomm to enable the system to leverage firmware to start the hardware and then shortly after re-initialize the system into a trusted state by using the OS boot loader and processor capabilities to send the system down a well-known and verifiable code path.
Put simply, Secure Launch acts as a sort of gatekeeper between system start-up (or, more specifically, BIOS/UEFI initialization) and actual Windows 10 operation. Using the power of newer CPUs, Secure Launch can ensure everything is running as planned, and no malicious code is attempting to latch itself onto your system before log-in.
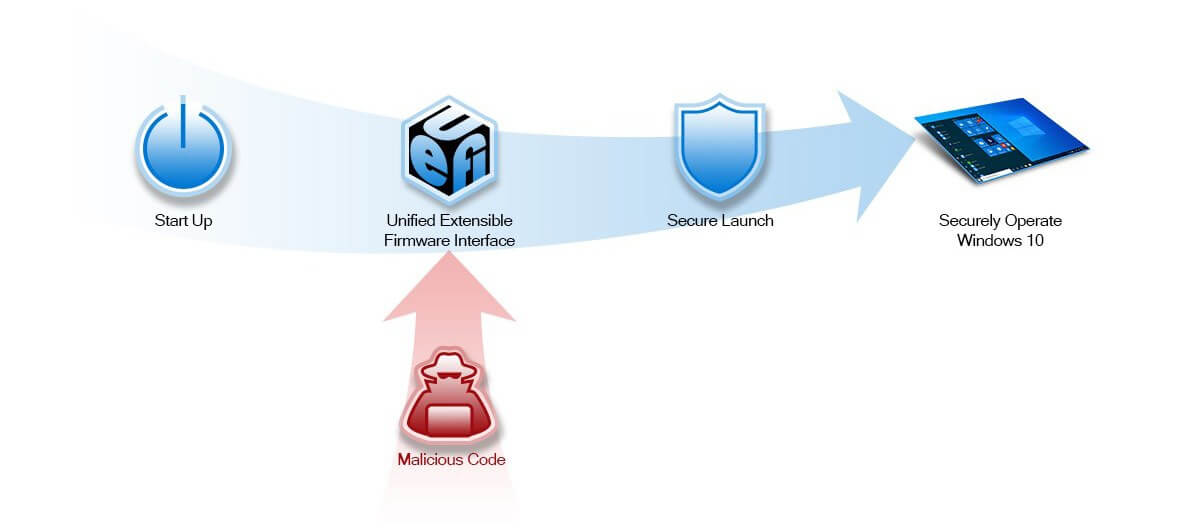
As nice as Secure Launch and the secured-core PC initiative as a whole sounds for those who take system security seriously, it doesn't seem like it'll be easily accessible to everyone. From what we can tell (we'll reach out to Microsoft for clarification on this point), only select PCs will be part of this initiative, at least for now.
On the official secured-core PC web page, Microsoft lists three supported laptops: the Lenovo ThinkPad X1 Yoga (4th-gen), the ThinkPad X1 Carbon (7th-gen), and the Panasonic Toughbook 55. It's unclear whether or not Secure Launch will make its way to custom or pre-built desktops PCs in the future. It's not likely, though -- Microsoft says secured-core PCs require "specific configuration[s]" to function.
https://www.techspot.com/news/82434-microsoft-ecured-core-pc-initiative-aims-protect-windows.html
[/s]